Question 1
Where does an administrator configure the VLANs used in VRF Lite? (Choose two.)
- A. uplink interface of the default Tier-0 gateway
- B. uplink trunk segment
- C. uplink interface of the VRF gateway
- D. downlink interface of the default Tier-0 gateway
- E. segment connected to the Tier-1 gateway
Answer:
bc
Comments
Question 2
How does the Traceflow tool identify issues in a network?
- A. Compares intended network state in the control plane with Tunnel End Point (TEP) keepalives in the data plane.
- B. Injects ICMP traffic into the data plane and observes the results in the control plane.
- C. Compares the management plane configuration states containing control plane traffic and error reporting from transport node agents.
- D. Injects synthetic traffic into the data plane and observes the results in the control plane.
Answer:
d
Comments
Question 3
Which statement is true about an alarm in a Suppressed state?
- A. An alarm can be suppressed for a specific duration in hours.
- B. An alarm can be suppressed for a specific duration in seconds.
- C. An alarm can be suppressed for a specific duration in minutes.
- D. An alarm can be suppressed for a specific duration in days.
Answer:
a
Comments
Question 4
Which three of the following describe the Border Gateway Routing Protocol (BGP) configuration on a Tier-0 Gateway? (Choose three.)
- A. It supports a 4-byte autonomous system number.
- B. The network is divided into areas that are logical groups.
- C. Can be used as an Exterior Gateway Protocol.
- D. BGP is enabled by default.
- E. EIGRP is disabled by default.
Answer:
acd
Comments
Question 5
A company is deploying NSX micro-segmentation in their vSphere environment to secure a simple application composed of web, app, and database tiers.
The naming convention will be:
WKS-WEB-SRV-XXX
WKY-APP-SRR-XXX
WKI-DB-SRR-XXX What is the optimal way to group them to enforce security policies from NSX?
- A. Use Edge as a firewall between tiers.
- B. Group all by means of tags membership.
- C. Create an Ethernet based security policy.
- D. Do a service insertion to accomplish the task.
Answer:
b
Comments
Question 6
A customer has a network where BGP has been enabled and the BGP neighbor is configured on the Tier-0 Gateway. An NSX administrator used the get gateways command to retrieve this information: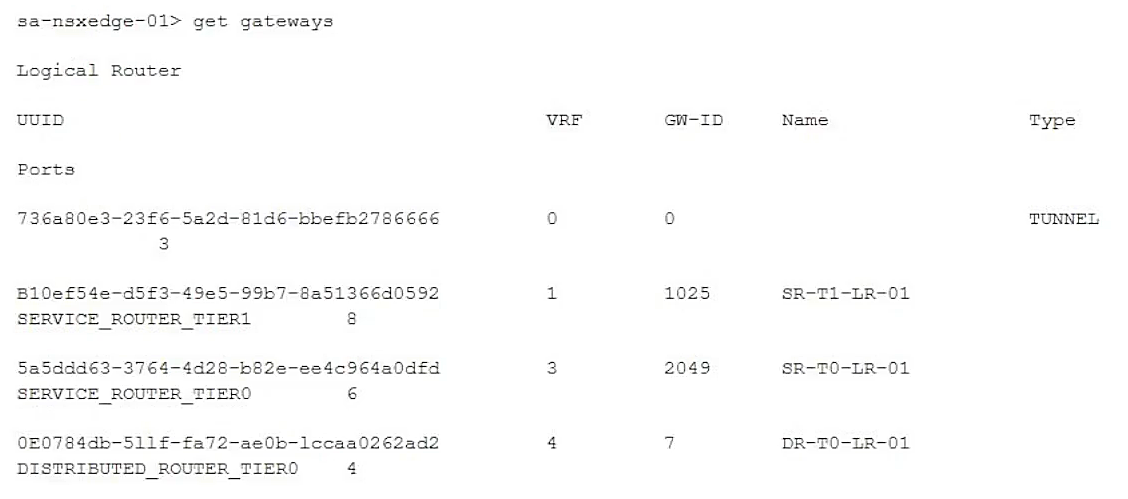
Which two commands must be executed to check BGP neighbor status? (Choose two.)
- A. vrf 3
- B. sa-nsxedge-01(tier1_sr)> get bgp neighbor
- C. vrf 4
- D. sa-nsxedge-01(tier0_dr)> get bgp neighbor
- E. vrf 1
- F. sa-nsxedge-01(tier0_sr)> get bgp neighbor
Answer:
af
Comments
Question 7
Which two statements are true about IDS Signatures? (Choose two.)
- A. Users can upload their own IDS signature definitions.
- B. An IDS signature contains data used to identify the creator of known exploits and vulnerabilities.
- C. IDS signatures can be High Risk, Suspicious, Low Risk and Trustworthy.
- D. An IDS signature contains data used to identify known exploits and vulnerabilities.
- E. An JDS signature contains a set of instructions that determine which traffic is analyzed.
Answer:
cd
Comments
Question 8
Which VPN type must be configured before enabling a L2VPN?
- A. SSL-based IPSec VPN
- B. Route-based IPSec VPN
- C. Port-based IPSec VPN
- D. Policy-based IPSec VPN
Answer:
b
Comments
Question 9
Which two of the following features are supported for the Standard NSX Application Platform Deployment? (Choose two.)
- A. NSX Network Detection and Response
- B. NSX Intelligence
- C. NSX Malware Prevention Metrics
- D. NSX Intrinsic Security
- E. NSX Intrusion Detection and Prevention
Answer:
ab
Comments
Question 10
What is the VMware recommended way to deploy a virtual NSX Edge Node?
- A. Through the NSX UI
- B. Through automated or interactive mode using an ISO
- C. Through the vSphere Web Client
- D. Through the OVF command line tool
Answer:
c
Comments
Page 1 out of 10
Viewing questions 1-10 out of 105
page 2