Question 1
[Cortex XDR Agent Configuration]
Based on the Malware profile image below, what happens when a new custom-developed
application attempts to execute on an endpoint?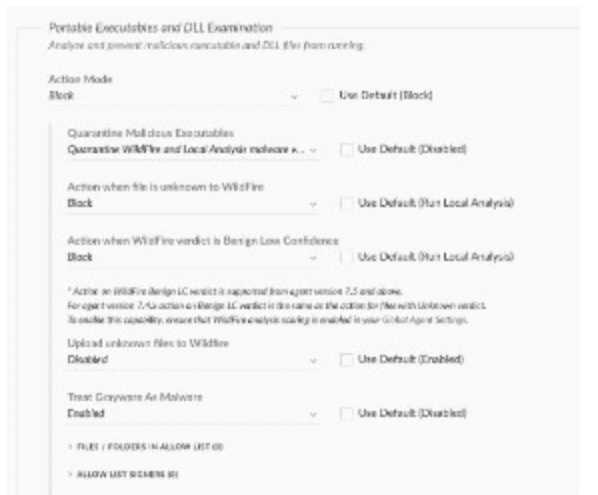
- A. It will immediately execute
- B. It will not execute
- C. It will execute after one hour
- D. It will execute after the second attempt
Answer:
B
Comments
Question 2
[Data Ingestion and Integration]
Which configuration profile option with an available built-in template can be applied to both
Windows and Linux systems by using XDR Collector?
- A. Filebeat
- B. HTTP Collector template
- C. XDR Collector settings
- D. Winlogbeat
Answer:
A
Comments
Question 3
[Detection Engineering]
What is the earliest time frame an alert could be automatically generated once the conditions of a
new correlation rule are met?
- A. Between 30 and 45 minutes
- B. Immediately
- C. 5 minutes or less
- D. Between 10 and 20 minutes
Answer:
C
Comments
Question 4
[Detection Engineering]
A Custom Prevention rule that was determined to be a false positive alert needs to be tuned. The
behavior was determined to be authorized and expected on the affected endpoint. Based on the
image below, which two steps could be taken? (Choose two.)
[Image description: A Custom Prevention rule configuration, assumed to trigger a Behavioral
Indicator of Compromise (BIOC) alert for authorized behavior]
- A. Apply an alert exception
- B. Apply an alert exclusion to the XDR behavioral indicator of compromise (BIOC) alert
- C. Apply an alert exclusion to the XDR agent alert
- D. Modify the behavioral indicator of compromise (BIOC) logic
Answer:
A,B
Comments
Question 5
[Data Ingestion and Integration]
In addition to using valid authentication credentials, what is required to enable the setup of the
Database Collector applet on the Broker VM to ingest database activity?
- A. Valid SQL query targeting the desired data
- B. Access to the database audit log
- C. Database schema exported in the correct format
- D. Access to the database transaction log
Answer:
A
Comments
Question 6
[Data Ingestion and Integration]
Which step is required to configure a proxy for an XDR Collector?
- A. Edit the YAML configuration file with the new proxy information
- B. Restart the XDR Collector after configuring the proxy settings
- C. Connect the XDR Collector to the Pathfinder
- D. Configure the proxy settings on the Cortex XDR tenant
Answer:
A
Comments
Question 7
[Maintenance and Troubleshooting]
How long is data kept in the temporary hot storage cache after being queried from cold storage?
- A. 1 hour, re-queried to a maximum of 12 hours
- B. 24 hours, re-queried to a maximum of 7 days
- C. 24 hours, re-queried to a maximum of 14 days
- D. 1 hour, re-queried to a maximum of 24 hours
Answer:
B
Comments
Question 8
[Post-Deployment Management and Configuration]
Which components may be included in a Cortex XDR content update?
- A. Device control profiles, agent versions, and kernel support
- B. Behavioral Threat Protection (BTP) rules and local analysis logic
- C. Antivirus definitions and agent versions
- D. Firewall rules and antivirus definitions
Answer:
B
Comments
Question 9
[Maintenance and Troubleshooting]
An insider compromise investigation has been requested to provide evidence of an unauthorized
removable drive being mounted on a company laptop. Cortex XDR agent is installed with default
prevention agent settings profile and default extension "Device Configuration" profile. Where can an
engineer find the evidence?
- A. Check Host Inventory -> Mounts
- B. dataset = xdr_data | filter event_type = ENUM.MOUNT and event_sub_type = ENUM.MOUNT_DRIVE_MOUNT
- C. The requested data requires additional configuration to be captured
- D. preset = device_control
Answer:
A
Comments
Question 10
[Cortex XDR Agent Configuration]
A static endpoint group is created by adding 321 endpoints using the Upload From File feature.
However, after group creation, the members count field shows 244 endpoints. What are two possible
reasons why endpoints were not added to the group? (Choose two.)
- A. Static groups have a limit of 250 endpoints when adding by file
- B. Endpoints added to the new group were previously added to an existing group
- C. Endpoints added to the group were in Disconnected or Connection Lost status when groupmembership was added
- D. The IP address, hostname, or alias of the endpoints must match an existing agent that has registered with the tenant
Answer:
C,D
Comments
Page 1 out of 4
Viewing questions 1-10 out of 50
page 2