palo alto networks pccse practice test
Prisma Certified Cloud Security Engineer
Last exam update: Jul 20 ,2024
Question 1
Which two attributes of policies can be fetched using API? (Choose two.)
- A. policy label
- B. policy signature
- C. policy mode
- D. policy violation
Answer:
ad
Question 2
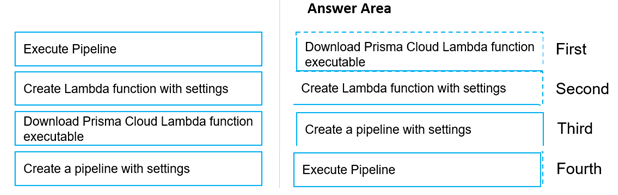
DRAG DROP
Move the steps to the correct order to set up and execute a serverless scan using AWS DevOps.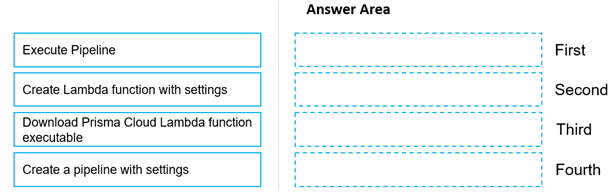
Answer:

Question 3
Which categories does the Adoption Advisor use to measure adoption progress for Cloud Security Posture Management?
- A. Visibility, Compliance, Governance, and Threat Detection and Response
- B. Network, Anomaly, and Audit Event
- C. Visibility, Security, and Compliance
- D. Foundations, Advanced, and Optimize
Answer:
c
Question 4
What is an automatically correlated set of individual events generated by the firewall and runtime sensors to identify unfolding attacks?
- A. policy
- B. incident
- C. audit
- D. anomaly
Answer:
b
Question 5
Which IAM Azure RQL query would correctly generate an output to view users who have sufficient permissions to create security groups within Azure AD and create applications?
- A. config where api.name = azure-active-directory-authorization-policy AND json.rule = defaultUserRolePermissions.allowedToCreateSecurityGroups is true and defaultUserRolePermissions.allowedToCreateApps is true
- B. config from cloud.resource where api.name = azure-active-directory-authorization-policy AND json.rule = defaultUserRolePermissions exists
- C. config from network where api.name = azure-active-directory-authorization-policy AND json.rule = defaultUserRolePermissions.allowedToCreateSecurityGroups is false and defaultUserRolePermissions.allowedToCreateApps is true
- D. config from cloud.resource where api.name = azure-active-directory-authorization-policy AND json.rule = defaultUserRolePermissions.allowedToCreateSecurityGroups is true and defaultUserRolePermissions.allowedToCreateApps is true
Answer:
d
Question 6
An S3 bucket within AWS has generated an alert by violating the Prisma Cloud Default policy `AWS S3 buckets are accessible to public`. The policy definition follows: config where cloud.type = 'aws' AND api.name='aws-s3api-get-bucket-acl' AND json.rule=((((acl.grants[?(@.grantee=='AllUsers')] size > 0) or policyStatus.isPublic is true) and publicAccessBlockConfiguration does not exist) or ((acl.grants[?(@.grantee=='AllUsers')] size > 0) and publicAccessBlockConfiguration.ignorePublicAcis is false) or (policyStatus.isPublic is true and publicAccessBlockConfiguration.restrictPublicBuckets is false)) and websiteConfiguration does not exist
Why did this alert get generated?
- A. an event within the cloud account
- B. network traffic to the S3 bucket
- C. configuration of the S3 bucket
- D. anomalous behaviors
Answer:
b
Question 7
While writing a custom RQL with array objects in the investigate page, which type of auto-suggestion a user can leverage?
- A. Auto-suggestion for array objects that are useful for comparing between arrays
- B. Auto-suggestion is not available for array objects
- C. Auto-suggestion for array objects that are useful for categorization of resource parameters
- D. Auto-suggestion for array objects that are useful for comparing between array elements
Answer:
c
Question 8
Which two required request headers interface with Prisma Cloud API? (Choose two.)
- A. Content-type:application/json
- B. x-redlock-auth
- C. >x-redlock-request-id
- D. Content-type:application/xml
Answer:
ab
Question 9
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
- A. add a new policy
- B. clone an existing policy
- C. disable an out-of-the-box policy
- D. edit the query in the out-of-the-box policy
Answer:
ab
Reference:
https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-policies/manage-prisma-cloud-policies
Question 10
Which of the following are correct statements regarding the use of access keys? (Choose two.)
- A. Access keys must have an expiration date
- B. Up to two access keys can be active at any time
- C. System Admin can create access key for all users
- D. Access keys are used for API calls
Answer:
bc