palo alto networks pccsa practice test
Palo Alto Networks Certified Cybersecurity Associate
Last exam update: Jul 20 ,2024
Question 1
What does a hypervisor enable?
- A. high-speed searching of already aggregated security log files
- B. high-speed aggregation and viewing of security log files
- C. multiple physical machines to be configured into a high-performance cluster
- D. multiple guest operating systems to run on a single physical machine
Answer:
D
Question 2
DRAG DROP
Match the OSI network model Layer 3 function to the correct description.
Select and Place: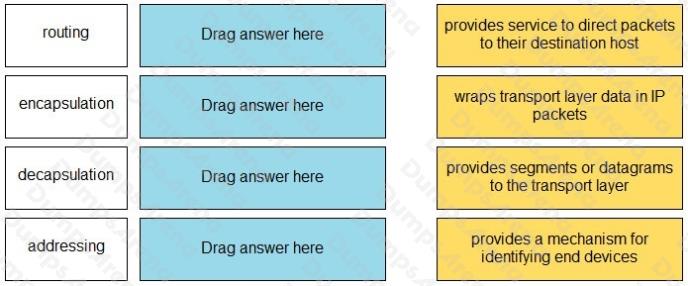
Answer:
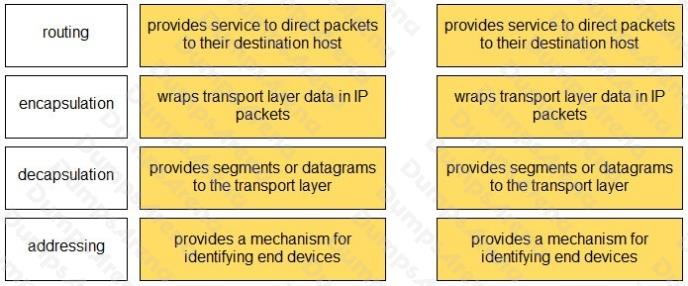
Question 3
Which two remote access methods are secure because they encrypt traffic? (Choose two.)
- A. IPsec-AH
- B. SSH
- C. VPN
- D. Telnet
- E. rlogin
Answer:
B C
Question 4
Which type of adversary would commit cybercrimes with the authorization of their country’s government?
- A. state-sponsored
- B. hacktivist
- C. gray hat
- D. white hat
Answer:
A
Question 5
Which protocol converts voice into a digital signal?
- A. IVO
- B. VoIP
- C. SNMP
- D. IGMP
Answer:
B
Question 6
From which resource can a Palo Alto Networks firewall get URL category information for URLs whose categories cannot be
found on the firewall?
- A. App-ID database
- B. WildFire
- C. PDF file
- D. PAN-DB database
Answer:
D
Question 7
A firewall located on an organization’s network perimeter can be used to protect against which type of attack?
- A. a malicious SaaS application file accessed from an unmanaged mobile phone
- B. ransomware installed from an infected USB drive
- C. malware installed on the laptop by a disgruntled employee
- D. a malicious PDF file located on an internet website
Answer:
D
Question 8
In the context of a mobile device management solution, what is a function of the “policy enforcement” feature?
- A. controls which websites can be accessed when connected to Wi-Fi
- B. controls which Wi-Fi networks can be accessed
- C. controls which phone numbers can be dialed
- D. controls which password/passcode settings are allowed
Answer:
A
Question 9
What does Palo Alto Networks Traps do first when an endpoint is asked to run an executable?
- A. send the executable to WildFire
- B. run a static analysis
- C. run a dynamic analysis
- D. check its execution policy
Answer:
D
Question 10
In PKI, which item is issued by a CA?
- A. digital certificate
- B. SSH key
- C. KDC ticket
- D. shared key
Answer:
A
Question 11
DRAG DROP
Match each cryptographic method with its description.
Select and Place: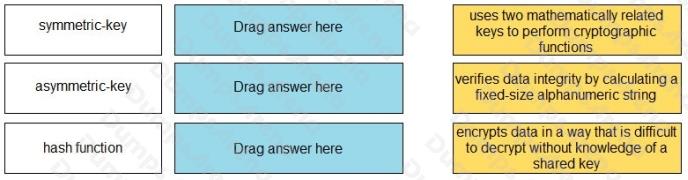
Answer:

Question 12
Which action must be taken prior to a successful ransomware attack to enable recovery from the attack?
- A. create a data snapshot on your IDS device
- B. back up all hosts that contain critical data
- C. update all firewall malware signatures
- D. limit external exposure of internal DNS resource records
Answer:
B
Question 13
Which type of firewall monitors traffic streams from beginning to end?
- A. circuit-level gateway
- B. stateless
- C. stateful
- D. packet filter
Answer:
C
Question 14
Which option describes a characteristic of a distributed denial-of-service attack?
- A. uses multiple types of malware to corrupt system services
- B. uses a single remote host to delete data from multiple target servers
- C. uses a single remote host to flood a target network with traffic
- D. uses a botnet to flood traffic to a target network
Answer:
D
Question 15
Which two types of SaaS applications are allowed by an IT department? (Choose two.)
- A. tolerated
- B. certified
- C. sanctioned
- D. unsanctioned
Answer:
A C
Explanation:
Reference: https://www.paloaltonetworks.com/cyberpedia/saas-security