rpta C. i test that , only remoty is the error.
Which three are true concerning command rules?
ADF
You configured Kerberos authentication for databases running on servers A and B.
However a database link connecting the database on server A to the database on server B fails with
ORA-12638 Credential retrieval failed.
Where must you make a change to sqlnet.ora to allow the database link to use its stored credentials
Instead of trying to use Kerberos?
B
A DBA user created and configured this secure application role: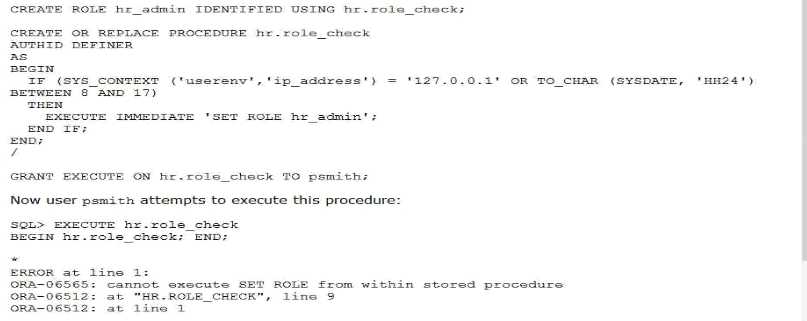
Why does the error occur?
D
rpta C. i test that , only remoty is the error.
se corrige la respuesta es e The HR.ROLE_CHECK procedure must be created with the AUTHID CURRENT_USERR clausere
You must mask data consistently In three database copies such that data relations across the
databases remain In place.
Which Data Masking Format allows this?
A
Respuesta D. Deterministic masking provides a solution for this problem. You can use the Substitute format to mask employee ID column(s) in all three databases. The Substitute format uses a table of values from which to substitute the original value with a mask value. As long as this table of values does not change, the mask is deterministic or consistent across the three databases
Examine this list:
1. You must monitor access to email column or salary column In the employees table.
2. If any activity is detected, the action must be audited and a notification sent out by email.
3. The database has Unified Auditing enabled.
4.
You have created and successfully tested the email sending procedure,
sysadmin_fga.emaii._ai.ert.
You create the audit policy: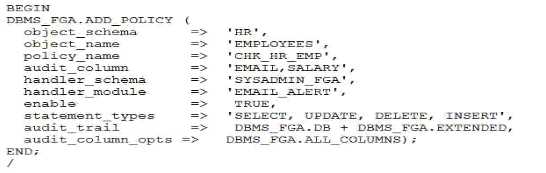
A user with select privilege on hr.employees executes this :
SELECT email FROM HR.EMPLOYEES;
What will be the result?
C
Database Vault Is configured and enabled In the Oracle database.
Three users are granted the dba, dv_omneb, and dv_acctmgb roles.
There is a requirement to create a user who can:
1. Connect to the database Instance
2. Select from dictionary views
Which users can complete the operation to meet the requirement?
D
Examine this command: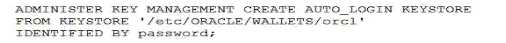
Which two statements are true?
AD
By default, Oracle creates an auto-login keystore, which can be opened from computers other than the computer on which the keystore resides. If you specify the LOCAL keyword, then Oracle Database creates a local auto-login keystore, which can be opened only from the computer on which the keystore resides.
Which two configurations can be used to protect sensitive data In a database?
CF
The sqinet.oia file on the client contains this parameter setting:
SQLNET.ENCRYPTION_CLIEKT = REQUESTED
What value for the parameter sQLNET.ENCRYPTION _server In the sqlnet.ora file on the server will
disable Encryption and Data Negotiation?
D
You are Implementing a security policy that makes use of the USERENV namespace.
Which USERRENV value does not change for the duration of a session?
A
Examine the statement:
CREATE BOLE hr_admin IDENTIFIED USING pac_mgr.hr_admin_rola_ch9ck;
Which three are true about the sec_mgr. hr_admin_role_check procedure?
CFG
not a. not d. It must include one or more security checks to validate the user.
b correct not c.. It must use invoker's rights to enable the role.
e correct. It must issue a SET ROLE SQL statement or DBMS_SESSION.SET_ROLE procedure when the user passes the security checks.
Which two are true about Database Privilege Analysis?
AE
not c. If the role, user, or object has been dropped, then the values that reflect the privilege captures for these in the privilege analysis data dictionary views are dropped as well.
not e. Privilege analysis shows the grant paths to the privilege but it does not suggest which grant path to keep.
d correct If a privilege is captured during run time, then it is saved under the run-time capture name
When querying the database view, VSECRYPTION_WALLET, the status Is OPEN_NO_MASTER _KEY.
What does this mean?
C
If the keystore is open but you have not created a TDE master encryption key yet , the STATUS column of the V$ENCRYPTION_WALLET view reminds you with an OPEN_NO_MASTER_KEY status.
OR
If WALLET_LOCATION is set for SSL wallet in sqlnet.ora and you have created the SSL wallet using orapki then also V$ENCRYPTION_WALLET is shows OPEN_NO_MASTER_KEY even when TDE is NOT configured .
Users and applications must be able to access a web server of type https using database package
UTL_HTTP.
Which three are part of the configuration to make this possible?
BDF
Examine these statements which execute successfully: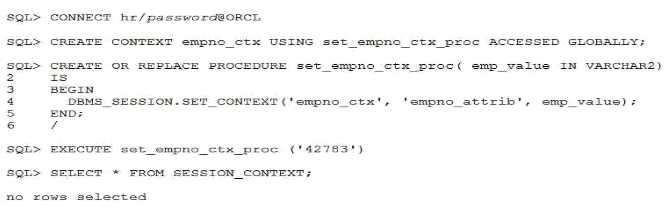
Which are the two reasons that no rows Are returned from the query?
DE
D, F Oracle Database Vault queries all the command rules that need to be applied.
For SELECT, DDL, and DML statements, multiple command rules may apply because the object owner and object name support wildcard notation.
B. If the associated rule set of any of the applicable command rules returns false or errors, Oracle Database Vault prevents the command from executing
E. If you disable a rule set, then the rule set always evaluates to TRUE.
C. FALSE . To customize and enforce the command rule, you associate it with a rule set, which is a collection of one or more rules.
G. False Command rules override object privileges.
E False , say if a command rule associated set is disabled no disable rule set THen the correct is B D y F