b anc c... Just as in validnode checking, both invited/excluded cannot be specified together. If they are, invited nodes take precedence.
Database Vault is not used in your installation.
Why is a conventional secure application role more secure than a normal role?
D
The listener configuration contains these lines related to Valid Node Checking for Registration
(VNCR);
Which two statements are true?
C
b anc c... Just as in validnode checking, both invited/excluded cannot be specified together. If they are, invited nodes take precedence.
Which statement is true about Network ACLs?
D
Explanation:
TheNETWORK_ACL_ADMINpackage provides the interface to administer the network access control
lists (ACL). ACLs are used to control access by users to external network services and resources from
the
database
through
PL/SQL
network
utility
packages
including
UTL_TCP
,
UTL_HTTP
,
UTL_SMTP
and
UTL_INADDR
.
https://docs.oracle.com/database/121/ARPLS/d_networkacl_adm.htm#ARPLS74568
You must disable OS authentication for database administrative users on a RAC database.
Which option must you use to do this?
D
By default users that are able to logon as the 'oracle' user on the unix/linux box are able to login to the database with administrator privileges via the command 'sqlplus / as sysdba'.
This form of authentication relies on the feature called 'Operating System Authentication' - No password is required for the user 'oracle'.
You may want to disable this authentication, and if any operating system user tries to login to the database instance, the user should be forced to use the command 'sqlplus sys@as sysdba' and supply the correct password. How would that be possible if at all?
Which type of attack attempts to find data by repeatedly trying similar SQL with a modified
predicate?
D
Which two statements are true about Valid Node Checking for Registration (VNCR)?
AD
You are required to remove embedded passwords from scripts that connect to database instances.
Which tool can be used to implement this requirement?
C
You grant user JANE the SYSDBA administrative privilege. Which two are true?
D
As an Autonomous Transaction Processing (ATP) database administrator, you want to extend the
storage capacity In the database.
Examine this command and output from the database: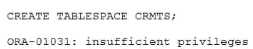
What is the reason for the error?
C
Which two statements are true about Database Vault factors?
AC