Question 1
SIMULATION
Task 7: Verify the OCI Certificate with Load Balancer
Verify HTTPS connection to the load balancer by running the following command in Cloud Shell
curl -k https://<Public IP of PBT-CERT-LB-01>
Enter the following URL in the web browser:
https://<Public IP of PBT-CERT-LB-01>
If prompted with a certificate error, accept the risk and continue.
Verify web page content by ensuring the text, "You are visiting Web Server 1" from the index.html
file is displayed in the browser
Answer:
See the
solution below in
Explanation.
Explanation:
Task 7: Verify the OCI Certificate with Load Balancer
Step 1: Obtain the Public IP of the Load Balancer
Log in to the OCI Console.
Navigate to Networking > Load Balancers.
Click on PBT-CERT-LB-01.
Note the Public IP Address from the load balancer details page.
Step 2: Verify HTTPS Connection Using Cloud Shell
Open the OCI Cloud Shell from the top-right corner of the OCI Console.
Run the following command, replacing <Public IP of PBT-CERT-LB-01> with the public IP you noted:
curl -k https://<Public IP of PBT-CERT-LB-01>
Expected output: You should see the text "You are visiting Web Server 1" if the connection is
successful. The -k flag ignores certificate validation errors (common during initial testing with self-
signed or newly issued certificates).
If you encounter an error, ensure the load balancer is active, the listener is configured correctly, and
the backend server (PBT-CERT-VM-01) is reachable.
Step 3: Verify in a Web Browser
Open a web browser.
Enter the following URL, replacing <Public IP of PBT-CERT-LB-01> with the public IP you noted:
https://<Public IP of PBT-CERT-LB-01>
If prompted with a certificate warning (e.g., due to a self-signed certificate or untrusted CA), accepttheriskandproceed(click"Advanced"and"Proceed"orsimilar,dependingonyourbrowser).Verifythatthewebpagedisplaysthetext"YouarevisitingWebServer1"fromtheindex.htmlfile
created on PBT-CERT-VM-01.
Step 4: Troubleshoot (if needed)
If the text is not displayed:
Check the load balancer health status under Backend Sets > Health in the OCI Console.
Ensure the security list PBT-CERT-LB-SL-01 allows port 443 and the compute instance security list
allows port 80.
Verify the Apache service is running on PBT-CERT-VM-01 by SSHing in and running sudo systemctl
status httpd.
Topic 2, Misc. Questions
Comments
Question 2
An E-commerce company running on Oracle Cloud Infrastructure (OCI) wants to prevent accidental
misconfigurations that could expose sensitive data. They need an OCI service that can enforce
predefined security rules when creating or modifying cloud resources.
Which OCI service should they use?
- A. OCI Web Application Firewall (WAF)
- B. OCI Identity and Access Management (IAM)
- C. OCI Security Zone
- D. OCI Certificates
Answer:
C
Comments
Question 3
According to the Oracle Cloud Infrastructure (OCI) Shared Responsibility Model, which statement
accurately reflects OCI's responsibility for security?
- A. OCI is responsible for securing the underlying infrastructure but not customer data.
- B. Customers are responsible for securing both infrastructure and data.
- C. OCI has no security responsibilities; customers need to secure their resources.
- D. OCI provides security only for free-tier services; customers secure everything else.
Answer:
A
Comments
Question 4
In Oracle Cloud Infrastructure (OCI), bare metal instances provide customers with direct access to the
underlying hardware. To mitigate security risks when a customer terminates a bare metal instance,
OCI utilizes Root-of-Trust hardware.
What is the primary function of the Root-of-Trust hardware in this context?
- A. It automatically encrypts data at rest on the bare metal instance.
- B. It ensures all non-volatile memory on the terminated instance is securely wiped before reuse.
- C. It guarantees complete isolation between customer workloads on different instances.
- D. It eliminates the need for hypervisors, reducing the potential attack surface.
Answer:
B
Comments
Question 5
You have created a compartment TEST in your subscribed tenancy. Then, you created two groups,
test1 and test2, and want the users in these groups to be able to manage all the resources in the
TEST compartment.
Which policy would you use to achieve this?
- A. Allow group /test*/ to manage all resources in compartment test.
- B. Allow group test1, test2 to manage all resources in compartment test.
- C. Allow any-user to manage all resources in compartment test where any {request.groups.test1, test2}
- D. Allow any-user to manage all resources in compartment test where request.group='test*'
Answer:
B
Comments
Question 6
A company has implemented OCI IAM policies with multiple levels of compartments. A policy
attached to a parent compartment grants "manage virtual-network-family" permissions. A policy
attached to a child compartment grants "use virtual-network-family" permissions.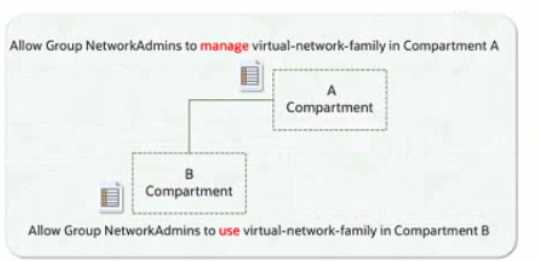
According to OCI IAM policy inheritance, how does the OCI IAM policy engine resolve the
permissions for a user attempting to perform an operation that requires 'manage' permissions in the
child compartment?
- A. The operation is denied due to conflicting policies.
- B. The policy in the parent compartment takes precedence, and the user is granted "manage" permissions.
- C. The policy in the child compartment takes precedence, and the user is granted "use" permissions only.
Answer:
B
Comments
Question 7
An OCI administrator notices that a compute instance running in the production compartment is
unable to create Object Storage buckets using the OCI CLI command:
oci os bucket create --name mybucket --compartment-id <compartment_OCID> --auth
instance_principal
The error message returned states:
"NotAuthorizedOrNotFound: You are not authorized to perform this action."
The administrator verifies that the instance has Internet access and can reach OCI endpoints.
What then could be causing the issue?
- A. The instance is using the wrong OCI CLI authentication method.
- B. The bucket name is already in use, causing a conflict.
- C. The policy is written at the root compartment instead of the production compartment.
- D. The instance is not part of any Dynamic Group or the matching rule is incorrect.
Answer:
D
Comments
Question 8
Your organization needs to implement strong password policies for users in OCI.
Which of the following statements is TRUE about password policies in OCI IAM?
- A. Custom password policies allow for granular control over password complexity.
- B. The default password policy cannot be modified.
- C. Only one password policy can be applied to all users in a domain.
- D. Simple password policies are suitable for production environments.
Answer:
A
Comments
Question 9
Within OCI IAM identity domains, the AD Bridge component serves a critical role. How does the AD
Bridge functionality specifically enhance Identity and Access Management (IAM) practices?
- A. It simplifies user provisioning by enabling automated synchronization of user accounts and group memberships from an existing Microsoft Active Directory (AD) environment.
- B. It facilitates delegated administration, allowing authorized AD users to manage specific resources within the OCI identity domain.
- C. It strengthens access security by providing an additional layer of authentication through AD integration.
- D. It directly integrates with OCI MFA providers, allowing for seamless enforcement of MFA for users authenticated through AD credentials.
Answer:
A
Comments
Question 10
A company is securing its compute instances (VMs and Bare Metal Machines) in Oracle Cloud
infrastructure (OCI) using a network firewall. As shown in the diagram, traffic flows from the internet
Gateway (IGW) to the firewall in the Public DMZ Subnet, and then to the compute instances in the
Public Subnet.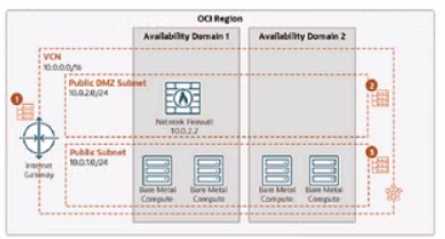
When configuring security lists and network security groups (NSGs) in this setup, what should they
consider?
- A. If the policy used with the firewall has no rules specified, the firewall allows all traffic.
- B. Ensure that any security list or NSG rules allow the traffic to enter the firewall for appropriate evaluation.
- C. Add stateful rules to the security list attached to the firewall subnet or include the firewall in an NSG containing stateful rules for better performance.
- D. Security list and NSG rules associated with the firewall subnet and VNICs are evaluated after the firewall.
Answer:
B
Comments
Page 1 out of 3
Viewing questions 1-10 out of 36
page 2