oracle 1z0-1104-21 practice test
Oracle Cloud Infrastructure Security 2021 Associate Exam
Last exam update: Jun 27 ,2025
Question 1
What is the minimum active storage duration for logs used by Logging Analytics to be archived?
- A. 60 days
- B. 10 days
- C. 30 days
- D. 15 days
Answer:
C
Explanation:
https://docs.oracle.com/en-us/iaas/logging-analytics/doc/manage-storage.html#:~:text=The%20minimum%20Active%20Storage%20Duration,be%20archived%20is%20
30%20days
.
The minimum Active Storage Duration (Days) for logs before they can be archived is30 days.
Question 2
Which components are a part of the OCI Identity and Access Management service?
- A. Policies
- B. Regional subnets
- C. Compute instances
- D. VCN
Answer:
A
Explanation:
https://docs.oracle.com/en-us/iaas/Content/Identity/Concepts/overview.htm
Question 3
Which WAF service component must be configured to allow, block, or log network requests when
they meet specified criteria?
- A. Protection rules
- B. Bot Management
- C. Origin
- D. Web Application Firewall policy
Answer:
A
Explanation:
Protection rules
Protection rules can be configured to either allow, block, or log network requests when they meet
the specified criteria of a protection rule. The WAF will observe traffic to your web application over
time and suggest new rules to apply.
https://www.oracle.com/security/cloud-security/what-is-waf/
Question 4
Which statement is true about standards?
- A. They may be audited.
- B. They are result of a regulation or contractual requirement or an industry requirement.
- C. They are methods and instructions on how to maintain or accomplish the directives of the policy.
- D. They are the foundation of corporate governance.
Answer:
B
Question 5
Which cache rules criterion matches if the concatenation of the requested URL path and query are
identical to the contents of the value field?
- A. URL_PART_CONTAINS
- B. URL_IS
- C. URL_PART_ENDS_WITH
- D. URL_STARTS_WITH
Answer:
B
Explanation:
URL_IS:Matches if the concatenation of request URL path and query is identical to the contents of
thevaluefield. URL must start with a/.
https://docs.oracle.com/en-us/iaas/tools/terraform-provider-oci/4.57.0/docs/d/waas_waas_policy.html
Question 6
Which is NOT a compliance document?
- A. Certificate
- B. Penetration test report
- C. Attestation
- D. Bridge letter
Answer:
B
Explanation:
Types of Compliance Documents
When viewing compliance documents, you can filter on the following types:
Attestation.A Payment Card Industry (PCI) Data Security Standard (DSS) Attestation of Compliance
document.
Audit.A general audit report.
Bridge Letter (BridgeLetter).A bridge letter. Bridge letters provide compliance information for the
period of time between the end date of an SOC report and the date of the release of a new SOC
report.
Certificate.A document indicating certification by a particular authority, with regard to certification
requirements and examination results conforming to said requirements.
SOC3.A Service Organization Controls 3 audit report that provides information relating to a service
organization's internal controls for security, availability, confidentiality, and privacy.
Other.A compliance document that doesn't fit into any of the preceding, more specific categories.
https://docs.oracle.com/en-
us/iaas/Content/ComplianceDocuments/Concepts/compliancedocsoverview.htm
Question 7
On which option do you set Oracle Cloud Infrastructure Budget?
- A. Compartments
- B. Instances
- C. Free-form tags
- D. Tenancy
Answer:
A
Explanation:
How Budgets Work
Budgets are set on
cost-tracking tags
or on compartments (including the root compartment) to track
all spending in that cost-tracking tag or for that compartment and its children.
https://docs.oracle.com/en-us/iaas/Content/Billing/Concepts/budgetsoverview.htm
Question 8
Which OCI cloud service lets you centrally manage the encryption keys that protect your data and the
secret credentials that you use to securely access resources?
- A. Data Safe
- B. Cloud Guard
- C. Data Guard
- D. Vault
Answer:
D
Explanation:
Oracle Cloud Infrastructure Vaultis a managed service that lets you centrally manage the encryption
keys that protect your data and the secret credentials that you use to securely access resources.
Vaults securely store master encryption keys and secrets that you might otherwise store in
configuration files or in code. Specifically, depending on the protection mode, keys are either stored
on the server or they are stored on highly available and durable hardware security modules (HSM)
that meet Federal Information Processing Standards (FIPS) 140-2 Security Level 3 security
certification.
https://docs.oracle.com/en-us/iaas/Content/KeyManagement/Concepts/keyoverview.htm
Question 9
Which type of file system does file storage use?
- A. NFSv3
- B. iSCSI
- C. Paravirtualized
- D. NVMe
- E. SSD
Answer:
A
Explanation:
TheFile Storageservice supports the Network File System version 3.0 (NFSv3) protocol. The service
supports the Network Lock Manager (NLM) protocol for file locking functionality.
https://docs.oracle.com/en-us/iaas/Content/File/Concepts/filestorageoverview.htm
Question 10
Which Oracle Cloud Service provides restricted access to target resources?
- A. Bastion
- B. Internet Gateway
- C. Load balancer
- D. SSL certificate
Answer:
A
Explanation:
Bastion
Oracle Cloud Infrastructure Bastionprovides restricted and time-limited access to target resources
that don't have public endpoints.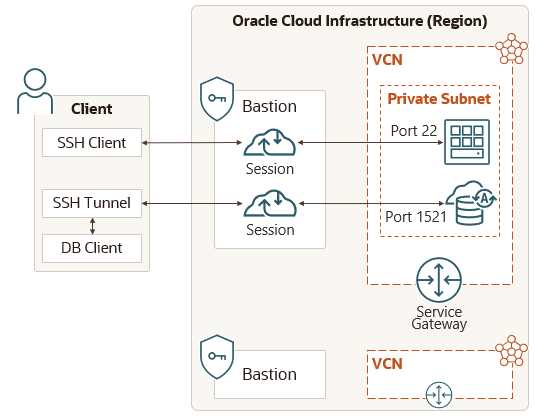
https://docs.oracle.com/en-us/iaas/Content/Security/Concepts/security_features.htm
Question 11
How can you convert a fixed load balancer to a flexible load balancer?
- A. There is no way to covert the load balancer.
- B. Use Update Shape workflows.
- C. Delete the fixed load balancer and create a new one.
- D. Using the Edit Listener option.
Answer:
B
Question 12
Which architecture is based on the principle of “never trust, always verify”?
- A. Federated identity
- B. Zero trust
- C. Fluid perimeter
- D. Defense in depth
Answer:
B
Explanation:
Enterprise
Interest
in
Zero
Trust
is
Growing
Ransomware and breaches are top of the news cycle and a major concern for organizations big and
small. So, many are now looking at the Zero Trust architecture and its primary principle never trust,
always verify to provide greater protection.
According to
Report Linker
, the Zero Trust security market is projected to grow from USD 15.6 billion
in 2019 to USD 38.6 billion by 2024 and that sounds right based on the large number of companies
pitching their Zero Trust wares at RSA 2020.
The enterprise was well represented at the conference and there was a tremendous amount of
interest in Zero Trust. Interestingly, even though Zero Trust environments are often made up of
several solutions from multiple vendors it hasnt prevented each of the vendors from evangelizing
their flavors of Zero Trust. This left the thousands of attendees to attempt to cut through the Zero
Trust buzz and noise and make their own conclusions to the best approach.
https://blogs.oracle.com/cloudsecurity/post/rsa-2020-recap-cloud-security-moves-to-the-front
Question 13
Which type of firewalls are designed to protect against web application attacks, such as SQL injection
and cross-site scripting?
- A. Stateful inspection firewall
- B. Web Application Firewall
- C. Incident firewall
- D. Packet filtering firewall
Answer:
B
Explanation:
SQL injections. Cross-site scripting. Distributed denial of service (DDoS) attacks. Botnets. These are
just some of the cyber-weapons increasingly being used by malicious actors to target web
applications, cause data breaches, and expose sensitive business information.
Oracle WAF uses a multilayered approach to protect web applications from a host of cyberthreats
including malicious bots, application layer (L7) DDoS attacks, cross-site scripting, SQL injection, and
vulnerabilities defined by the Open Web Application Security Project (OWASP). When a threat is
identified, Oracle WAF automatically blocks it and alerts security operations teams so they can
investigate further.
https://www.oracle.com/a/ocom/docs/security/oci-web-application-firewall.pdf
Question 14
What does an audit log event include?
- A. Audit type
- B. Header
- C. Footer
- D. Type of input
Answer:
B
Explanation:
The HTTP header fields and values in the request.
https://docs.oracle.com/en-us/iaas/Content/Audit/Reference/logeventreference.htm
Question 15
Which is NOT a part of Observability and Management Services?
- A. Event Services
- B. OCI Management Service
- C. Logging Analytics
- D. Logging
Answer:
B
Explanation:
https://www.oracle.com/in/manageability/