oracle 1z0-1072-21 practice test
Oracle Cloud Infrastructure 2021 Architect Associate Exam
Last exam update: Jul 20 ,2024
Question 1
You have two NFS clients running in two different subnets within the same Oracle Cloud
Infrastructure (OCI) Virtual Cloud Network (VCN). You have created a shared file system for the two
NFS clients who want to connect to the same file system, but you want to restrict one of the clients to
have READ access while the other has READ/Write access. Which OCr feature would you leverage to
meet this requirement?
- A. Use VCN security rules to control access for the NFS clients
- B. Use OCI Identity Access Management to control access for the NFS clients
- C. Use File Storage NFS Export Options to control access for the NFS clients
- D. Use NFS security to control access for the NES clients
Answer:
C
Explanation:
Oracle Cloud Infrastructure File Storage service provides a durable, scalable, secure, enterprise-grade
network file system. You can connect to a File Storage service file system from any bare metal, virtual
machine, or container instance in your Virtual Cloud Network (VCN). You can also access a file system
from outside the VCN using Oracle Cloud Infrastructure FastConnect and Internet Protocol security
(IPSec) virtual private network (VPN).
EXPORT
Exports control how NFS clients access file systems when they connect to a mount target. File
systems are exported (made available) through mount targets. Each mount target maintains an
export set which contains one or many exports. A file system must have at least one export in one
mount target in order for instances to mount the file system. The information used by an export
includes the file system OCID, mount target OCID, export set OCID,
export path
, and client
export
options
. For more information, see
Managing Mount Targets
.
EXPORT SET
Collection of one or more exports that control what file systems the mount target exports using
NFSv3 protocol and how those file systems are found using the NFS mount protocol. Each mount
target has an export set. Each file system associated with the mount target has at least one export in
the export set.
EXPORT PATH
A path that is specified when an export is created. It uniquely identifies the file system within the
mount target, letting you associate up to 100 file systems to a single mount target. This path is
unrelated to any path within the file system itself, or the client mount point path.
EXPORT OPTIONS
NFS export options are a set of parameters within the export that specify the level of access granted
to NFS clients when they connect to a mount target. An NFS export options entry within an export
defines access for a single IP address or CIDR block range. For more information, see
Working with
NFS Export Options
.
Question 2
Which of the following statement is true regarding Oracle Cloud Infrastructure Object Storage Pre-
Authenticated Requests?
- A. It Is not possible to create pre-authenticated requests for "archive" storage tier
- B. Changing the bucket visibility does not change existing pre-authenticated requests
- C. It is not possible to create pre-authenticated requests for the buckets, but only for the objects
- D. Pre-authenticated requests don't have an expiration
Answer:
B
Explanation:
Pre-authenticated requests provide a way to let users access a bucket or an object without having
their own credentials, as long as the request creator has permissions to access those objects. For
example, you can create a request that lets an operations support user upload backups to a bucket
without owning API keys. Or, you can create a request that lets a business partner update shared
data in a bucket without owning API keys.
When you create a pre-authenticated request, a unique URL is generated. Anyone you provide this
URL to can access the Object Storage resources identified in the pre-authenticated request, using
standard HTTP tools like curl and wget.
Understand the following scope and constraints regarding pre-authenticated requests:
Users can't list bucket contents.
You can create an unlimited number of pre-authenticated requests.
There is no time limit to the expiration date that you can set.
You can't edit a pre-authenticated request. If you want to change user access options in response to
changing requirements, you must create a new pre-authenticated request.
The target and actions for a pre-authenticated request are based on the creator's permissions. The
request is not, however, bound to the creator's account login credentials. If the creator's login
credentials change, a pre-authenticated request is not affected.
You cannot delete a bucket that has a pre-authenticated request associated with that bucket or with
an object in that bucket.
Understand the following scope and constraints regarding public access:
Changing the type of access is bi-directional. You can change a bucket's access from public to private
or from private to public.
Changing the type of access doesn't affect existing pre-authenticated requests. Existing pre-
authenticated requests still work.
Question 3
You have a working application in the US East region. The app is a 3-tier app with a database backend
- you take regular backups of the database into OCI Object Storage in the US East region. For Business
continuity; you are leveraging OCI Object Storage cross-region copy feature to copy database backups
to the US West region. Which of the following three steps do you need to execute to meet your
requirement?
- A. Write an IAM policy and authorize the Object Storage service to manage objects on your behalf
- B. Specify an existing destination bucket
- C. Specify the bucket visibility for both the source and destination buckets
- D. Provide a destination object name
- E. Provide an option to choose bulk copying of objects
- F. Choose an overwrite rule
Answer:
ABF
Explanation:
You can copy objects to other buckets in the same region and to buckets in other regions.
You must have the required access to both the source and destination buckets when performing an
object copy. You must also have permissions to manage objects in the source and destination
buckets.
Because Object Storage is a regional service, you must authorize the Object Storage service for each
region carrying out copy operations on your behalf. For example, you might authorize the Object
Storage service in region US East (Ashburn) to manage objects on your behalf. Once you authorize
the Object Storage service, you can copy an object stored in a US East (Ashburn) bucket to a bucket in
another region.
You can use overwrite rules to control the copying of objects based on their entity tag (ETag) values.
Specify an existing target bucket for the copy request. The copy operation does not automatically
create buckets.
Question 4
Your IT department wants to cut down storage costs, but also meet compliance requirements as set
up by the central audit group. You have a legacy bucket with both Word does (*.docx) and Excel files
(*.xlsx). Your auditors want to retain only Excel files for compliance purposes. Your IT departments
wants to keep all other files for 365 days only. What two steps can you take to meet this
requirement?
- A. Create Object Storage Lifecycle rules to archive objects from the legacy bucket after 365 days without any pattern matching
- B. Create Object Storage Lifecycle rules to delete objects from the legacy bucket after 365 days with a filter type - include by pattern: ''.docx
- C. It is not possible to meet this requirement
- D. Create Object Storage Lifecycle rules to delete objects from the legacy bucket after 365 days with a filter type - exclude by pattern: ''.xlsx"
- E. Create Object Storage Lifecycle rules to delete objects from the legacy bucket after 365 days without any pattern matching
Answer:
BD
Explanation:
Object Lifecycle Management lets you automatically manage the archiving and deletion of objects.
By using Object Lifecycle Management to manage your
Object Storage
and
Archive Storage
data, you
can reduce your storage costs and the amount of time you spend managing data.
Use object name filters to specify which objects the lifecycle rule applies to.
You can add object filters in any order. Object Lifecycle Management evaluates the precedence of the
rules as follows:
Pattern exclusions
Pattern inclusions
Prefix inclusions
Question 5
Your application consists of three Oracle Cloud Infrastructure compute instances running behind a
public load balancer. You have configured the load balancer to perform health checks on these
instances, but one of the three instances fails to pass the configured health check. Which of the
following action will the load balancer perform?
- A. Stop sending traffic to the instance that failed health check
- B. Terminate the instance that failed health check
- C. Stop the instances that failed health check
- D. Remove the instance that failed the health check from the backend set
Answer:
A
Explanation:
health check A test to confirm the availability of backend servers. A health check can be a request or
a connection attempt. Based on a time interval you specify, the load balancer applies the health
check policy to continuously monitor backend servers. If a server fails the health check, the load
balancer takes the server temporarily out of rotation. If the server subsequently passes the health
check, the load balancer returns it to the rotation.
You configure your health check policy when you create a backend set. You can configure TCP-level or
HTTP-level health checks for your backend servers.
- TCP-level health checks attempt to make a TCP connection with the backend servers and validate
the response based on the connection status.
- HTTP-level health checks send requests to the backend servers at a specific URI and validate the
response based on the status code or entity data (body) returned.
The service provides application-specific health check capabilities to help you increase availability
and reduce your application maintenance window.
Question 6
You are a network architect of an application running on Oracle Cloud Infrastructure (OCI). Your
security team has informed you about a security patch that needs to be applied immediately to one
of the backend web servers. What should you do to ensure that the OCI load balancer does not
forward traffic to this backend server during maintenance?
- A. Drain all existing connections to this backend server and mark the backend web server offline
- B. Create another OCI load balancer for the backend web servers, which are active and handling traffic
- C. Edit the security list associated with the subnet to avoid traffic connectivity to this backend serve
- D. Stop the load balancer for maintenance and restart the load balancer after the maintenance is finished
Answer:
A
Explanation:
A load balancer improves resource utilization, facilitates scaling, and helps ensure high
availability. You can configure multiple load balancing policies and application-specific health
checks to ensure that the load balancer directs traffic only to healthy instances. The load
balancer can reduce your maintenance window by draining traffic from an unhealthy
application server before you remove it from service for maintenance.
The Load Balancing service considers a server marked drain available for existing persisted
sessions. New requests that are not part of an existing persisted session are not sent to that
server.
Edit Drain State: Opens a dialog box in which you can change the drain state.
If you set the server's drain status to true, the load balancer stops forwarding
new TCP connections and new non-sticky HTTP requests to this backend server.
This setting allows an administrator to take the server out of rotation for
maintenance purposes.
e. Edit Offline State: Opens a dialog box in which you can change the offline
status.
If you set the server's offline status to true, the load balance forwards no ingress
traffic to this backend server.
Question 7
You have launched a compute instance running Oracle database in a private subnet in the Oracle
Cloud Infrastructure US East region. You have also created a Service Gateway to back up the data files
to OCI Object Storage in the same region. You have modified the security list associated with the
private subnet to allow traffic to the Service Gateway, but your instance still cannot access OCI Object
Storage. How can you resolve this issue?
- A. Add a stateful rule that enables ingress HTTPS (TOP port 443) traffic to 001 Object Storage in the security list associated with the private subnet
- B. Add a stateful rule that enables egress HTTPS (TCP port 443) traffic to OCI Object Storage in the security list associated with the private subnet
- C. Add a rule in the Route Table associated with the private subnet with Target type as "Service Gateway" and destination service as all IAD services in the Oracle Service Network.'
- D. Use the default Security List, which has ports open for OCI Object Storage
Answer:
C
Explanation:
A service gateway lets your virtual cloud network (VCN) privately access specific Oracle services
without exposing the data to the public internet. No internet gateway or NAT is required to reach
those specific services. The resources in the VCN can be in a private subnet and use only private IP
addresses. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and
never traverses the internet.
The service gateway is regional and enables access only to supported Oracle servicesin the same
regionas the VCN.
For traffic to be routed from a subnet in your VCN to a service gateway, you must add a rule
accordingly to the subnet's route table. The rule must use the service gateway as the target. For the
destination, you must use the
service CIDR label
that is enabled for the service gateway. This means
that you don't have to know the specific public CIDRs, which could change over time.
Question 8
You have two line of business operations (LOB1, LOB2) leveraging Oracle Cloud Infrastructure. LOB1
is deployed in VCN1 in the OCI US East region, while LOB2 is deployed in VCN2 in the US West region.
You need to peer VCN1 and VCN2 for disaster recovery and data backup purposes. To ensure you can
utilize the OCI Virtual Cloud Network remote peering feature, which CIDR ranges should be used?
- A. VCN1 (10.0.0.0/16) and VCN2 (10.0.1.0/24)
- B. VCN1 (10.0.0.0/16) and VCN2 (172.16.0.0/16)
- C. VCN1 (172.16.1.0/24) and VCN2 (172.16.1.0/27)
- D. VCN1 (192.168.0.0/16) and VCN2 (192.168.1.0/27)
Answer:
B
Explanation:
VCN1 (10.0.0.0/16) will use the IP Range from 10.0.0.0 to 10.0.255.255 and the VNC 2
(172.16.0.0/16) will use the IP Range from 172.16.0.0 to 172.16.255.255 the will not be overlap
between the 2 VCN
Question 9
You have created a new compartment called Production to host some production apps. You have also
created users in your tenancy and added them to a Group called "production group". Your users are
still unable to access the Production compartment. How can you resolve this situation?
- A. Every compartment you create comes with a predefined set of policies, so no further action is needed
- B. Your users get automatic access to all compartments, so no further action is needed
- C. Write an IAM Policy for each specific user granting them access to the production compartment
- D. Write an IAM Policy for "production_group" granting it access to the production compartment
Answer:
D
Explanation:
When creating a compartment, you must provide anamefor it (maximum 100 characters, including
letters, numbers, periods, hyphens, and underscores) that is unique within its parent compartment.
You must also provide adescription, which is a non-unique, changeable description for the
compartment, from 1 through 400 characters.
After creating a compartment, you need to write at least onepolicyfor it, otherwise no one can
access it (except administrators or users who have permissions set at the tenancy level). When
creating a compartment inside another compartment, the compartment inherits access permissions
from compartments higher up its hierarchy.
When you create an access policy, you need to specify which compartment to attach it to. This
controls who can later modify or delete the policy. Depending on how you've designed your
compartment hierarchy, you might attach it to the tenancy, a parent, or to the specific compartment
itself.
Question 10
You have the following compartment structure in your tenancy. Root compartment->Training-
>Training-subl ->Training-sub2 You create a policy in the root compartment to allow the default
admin for the account (Administrators) to manage block volumes in compartment Training-sub2.
What policy would you write to meet this requirement?
- A. Allow group Administrators to manage volume-family in root compartment
- B. Allow group Administrators to manage volume-family in compartment Training-sub1 :Training- sub2
- C. Allow group Administrators to manage volume-family in compartment Training: Training-sub 1 :Training-sub2
- D. Allow group Administrators to manage volume-family in compartment Training-sub2
Answer:
C
Explanation:
a policy statement must specify the compartment for which access is being granted (or the tenancy).
Where you create the policy determines who can update the policy. If you attach the policy to the
compartment or its parent, you can simply specify the compartment name. If you attach the policy
further up the hierarchy, you must specify the path. The format of the path is each compartment
name (or OCID) in the path, separated by a colon:
<compartment_level_1>:<compartment_level_2>:. . .<compartment_level_n>
For example, assume you have a three-level compartment hierarchy, shown here: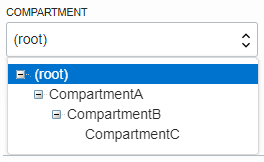
You want to create a policy to allow NetworkAdmins to manage VCNs in CompartmentC. If you want
to attach this policy to CompartmentC or to its parent, CompartmentB, write this policy statement:
Allow group NewtworkAdmins to manage virtual-network-family in compartment CompartmentC
However, if you want to attach this policy to CompartmentA (so that only administrators of
CompartmentA can modify it), write this policy statement that specifies the path:
Allow
group NewtworkAdmins
to manage
virtual-network-family
in
compartment
CompartmentB:CompartmentC
To attach this policy to the tenancy, write this policy statement that specifies the path from
CompartmentA to CompartmentC:
Allow
group NewtworkAdmins
to manage
virtual-network-family
in
compartment
CompartmentA:CompartmentB:CompartmentC
Question 11
You have an instance running in a development compartment that needs to make API calls against
other OCI services, but you do not want to configure user credentials or a store a configuration file on
the instance. How can you meet this requirement?
- A. Create a dynamic group with matching rules to include your instance
- B. Instances can automatically make calls to other OCI services
- C. Instances are secure and cannot make calls to other OCI services
- D. Create a dynamic group with matching rules to include your instance and write a policy for this dynamic group
Answer:
D
Explanation:
Dynamic groups allow you to group Oracle Cloud Infrastructure computer instances as "principal"
actors (similar to user groups).
When you create a dynamic group, rather than adding members explicitly to the group, you instead
define a set ofmatching rulesto define the group members. For example, a rule could specify that all
instances in a particular compartment are members of the dynamic group. The members can change
dynamically as instances are launched and terminated in that compartment.
A dynamic group has no permissions until you write at least onepolicythat gives that dynamic group
permission to either the tenancy or a compartment. When writing the policy, you can specify the
dynamic group by using either the unique name or the dynamic group's OCID. Per the preceding
note, even if you specify the dynamic group name in the policy, IAM internally uses the OCID to
determine the dynamic group.
Question 12
Which two Oracle Cloud Infrastructure services use a Dynamic Routing Gateway?
- A. OCI FastConnect Public Peering
- B. Local Peering
- C. OCI FastConnect Private Peering
- D. Internet Gateway
- E. OCI IPSec VPN Connect
Answer:
CE
Explanation:
You can think of a DRG as a virtual router that provides a path for private traffic (that is, traffic that
uses private IPv4 addresses) between your VCN and networks outside the VCN's region.
You use a DRG when connecting your existing on-premises network to your virtual cloud network
(VCN) with one (or both) of these:
IPSec VPN
Oracle Cloud Infrastructure FastConnect
(Private Only)
You also use a DRG when peering a VCN with a VCN in a different region:
Remote VCN Peering (Across Regions)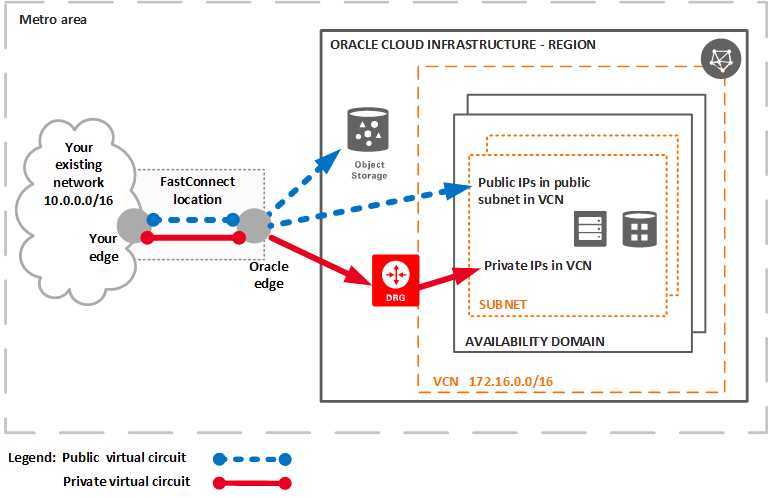
Question 13
Which two statements are true about Oracle Cloud Infrastructure IPSec VPN Connect?
- A. Each OCI IPSec VPN consists of multiple redundant IPSec tunnels
- B. OCI IPSec VPN tunnel supports only static routes to route traffic
- C. OCI IPSec VPN can be configured in tunnel mode only
- D. OCI IPSec VPN can be configured in trans port mode only
Answer:
AC
Explanation:
VPN Connect provides a site-to-site IPSec VPN between your on-premises network and your virtual
cloud network (VCN). The IPSec protocol suite encrypts IP traffic before the packets are transferred
from the source to the destination and decrypts the traffic when it arrives.
On general, IPSec can be configured in the following modes:
Transport mode:IPSec encrypts and authenticates only the actual payload of the packet, and the
header information stays intact.
Tunnel mode (supported by Oracle):IPSec encrypts and authenticates the entire packet. After
encryption, the packet is then encapsulated to form a new IP packet that has different header
information.
Oracle Cloud Infrastructure supports only the tunnel mode for IPSec VPNs.
Each Oracle IPSec VPN consists of multiple redundant IPSec tunnels. For a given tunnel, you can use
either Border Gateway Protocol (BGP)dynamic routingorstatic routingto route that tunnel's traffic.
More details about routing follow.
IPSec VPN site-to-site tunnels offer the following advantages:
Public internet lines are used to transmit data, so dedicated, expensive lease lines from one site to
another aren't necessary.
The internal IP addresses of the participating networks and nodes are hidden from external users.
The entire communication between the source and destination sites is encrypted, significantly
lowering the chances of information theft.
Question 14
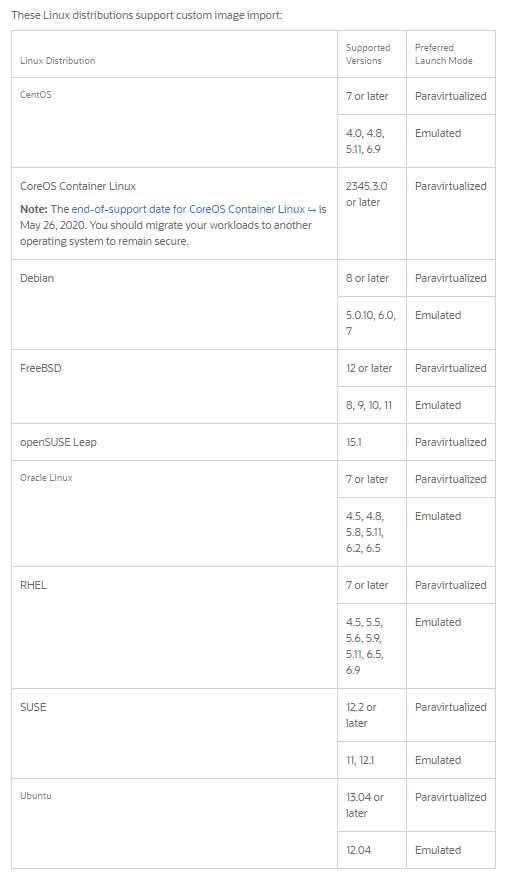
You are running several Linux based operating systems in your on .premises environment that you
want to import to OCI as custom images. You can launch your imported images as OCI compute
Virtual machines. Which two modes below can be used to launch these imported Linux VMs?
- A. Native
- B. Mixed
- C. Paravirtualized
- D. Emulated
Answer:
CD
Explanation:
You can use the Console or API to import exported images from Object Storage. To import an image,
you need read access to the Object Storage object containing the image.
during the Import you can select the Launch mode:
For custom images where the image format is.oci, Oracle Cloud Infrastructure selects the applicable
launch mode based on the launch mode for the source image.
For custom images exported from Oracle Cloud Infrastructure where the image type is QCOW2,
selectNative Mode.
To import other custom images selectParavirtualized ModeorEmulated Mode. For more
information, see
Bring Your Own Image (BYOI)
.
Question 15
You have deployed a compute instance (VM.Standard2.24) to run an Oracle database. With this set
up, you run into some performance issues and want to leverage an OCI Dense IO shape
(VM.DenseIO2.24), with which you get 25.6 TB local NVMe SSD. You do not want to lose the
configuration changes you made to the instance. Which of the following TWO steps ARE NOT
required to make this transition?
- A. Terminate the VM.Standard2.24 instance and do not preserve the boot volume
- B. Create a new instance using the VM.Dense102.24 shape using the preserved boot volume and move the Oracle Database data to NVMe disks
- C. Terminate the VM.Standard2.24 instance and preserve the boot volume
- D. Create a new instance using a VM.DenseIO2.24 shape using the preserved boot volume and move the Oracle Database data to block volumes
Answer:
AD
Explanation:
You can permanently terminate (delete) instances that you no longer need. Any attached VNICs and
volumes are automatically detached when the instance terminates. Eventually, the instance's public
and private IP addresses are released and become available for other instances. By default, the
instance's boot volume is deleted when you terminate the instance, however you canpreserve the
boot volumeassociated with the instance, so that you can attach it to a different instance as a data
volume, or use it to launch a new instance.
Dense I/O Shapes Designed for large databases, big data workloads, and applications that require
high-performance local storage. DenseIO shapes include locally-attached NVMe-based SSDs.
so once you create theVM.DenseIOyou need to moce the Database to locally-attached NVMe-based
SSDs