Question 1
Which of the following statements about IP-VRFs in Nokia’s SR Linux is FALSE?
- A. An IP-VRF is a Layer 3 network instance.
- B. Packets in an IP-VRF are forwarded based on the destination IP address.
- C. The router maintains a distinct route table for each IP-VRF instance.
- D. Multiple servers can be connected to the same subnet in an IP-VRF.
Answer:
D
Explanation:
Multiple servers connected to the same subnet typically reside within the same Layer 2 domain or
MAC-VRF. IP-VRFs operate at Layer 3 and segment routing and forwarding by separate routing tables,
so multiple servers on the same subnet are not a function of IP-VRF.
Comments
Question 2
Which of the following statements about the MAC table shown in the exhibit output is FALSE?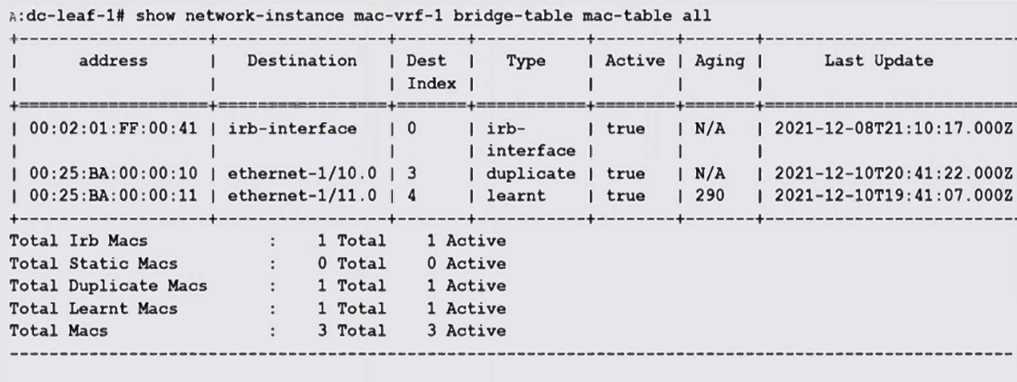
- A. The MAC address 00:25: BA:00:00:10 is learnt on more than one interface.
- B. The MAC re-learning rate has exceeded the threshold within the specified time frame.
- C. [interface ethernet-1/10 is configured with the MAC address 00:25:BA:00:00:10.
- D. Mac-duplication detection is enabled in mac-vrf-1.
Answer:
A
Explanation:
The MAC address 00:25:BA:00:00:10 is listed as "duplicate," but it appears only once associated with
interface ethernet-1/10. Therefore, it is not learned on more than one interface.
Comments
Question 3
Which of the following statements about a MAC-VRF is FALSE?
- A. A MAC-VRF is a Layer 2 network instance.
- B. Bridge table entries contain an exit interface for each destination address.
- C. Packets received in a MAC-VRF are forwarded based on destination IP address.
- D. Multiple devices can be connected to the same IP subnet using a MAC-VRF.
Answer:
C
Explanation:
In a MAC-VRF, packets are forwarded based on Layer 2 information such as destination MAC
addresses, not on destination IP addresses.
Comments
Question 4
Which of the following statements about resilient ECMP load balancing is TRUE?
- A. The hash value used to distribute traffic is calculated as a modulo function on specific fields of the packet header.
- B. Hash buckets are used to ensure that flows egressing the same interface on one router use different egress interfaces on downstream routers.
- C. A different hash seed is used on downstream routers to ensure that flows are randomly distributed across all eligible router interfaces.
- D. When one of the next-hops fail, only flows currently egressing to that next-hop are impacted.
Answer:
D
Explanation:
In resilient ECMP load balancing, when a next-hop fails, only the flows that were using that specific
next-hop are affected and need to be redistributed, minimizing disruption to other flows.
Comments
Question 5
Examine the exhibit. Which of the following statements is TRUE?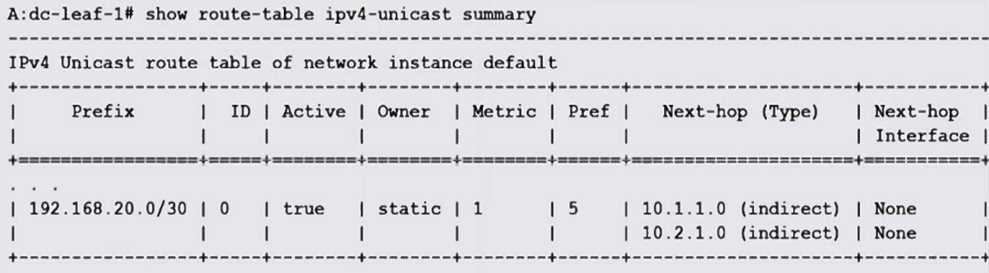
- A. A recursive lookup is performed to resolve 10.2.1.0 to use 10.1.1.0.
- B. A recursive lookup is performed to resolve 10.1.1.0 to use 10.2.1.0.
- C. The next-hop group for this static route is configured with two next-hops.
- D. The next-hop selected for this route will be based on the preference value configured for each next-hop.
Answer:
C
Explanation:
The static route shows two next-hop IP addresses (10.1.1.0 and 10.2.1.0) listed, indicating that a
next-hop group with multiple next-hops is configured for load balancing or redundancy.
Comments
Question 6
A static route is configured in two steps in Nokia’s SR Linux. Which of the following items CANNOT be
configured in the static-routes container?
- A. blackhole
- B. IPv4 destination prefix
- C. Preference value
- D. Next-hop group
Answer:
A
Explanation:
The static-routes container in Nokia SR Linux does not support configuring a blackhole route directly;
it is used to configure destination prefixes, preference values, and next-hop groups for static routing.
Comments
Question 7
Which of the following statements about next-hop groups is TRUE?
- A. The next-hop for a next-hop-group must be a local IP address.
- B. Multiple static routes can use the same next-hop-group.
- C. CMP destination unreachable message is always sent when blackhole is specified in the next-hop- group.
- D. A next-hop-group can only specify one next-hop for forwarding
Answer:
B
Explanation:
Multiple static routes can share the same next-hop group, enabling efficient reuse of next-hop
definitions for load balancing or redundancy.
Comments
Question 8
Which of the following is NOT how prefixes are typically learned and advertised in a leaf and spine
data center?
- A. Spine routers advertise learned prefixes to leaf routers directly using eBGP.
- B. Spine routers learn prefixes from leaf routers directly using eBGP.
- C. Each leaf router advertises the prefixes of its own locally connected servers.
- D. Each leaf router learns the prefixes of remote servers from other leaf routers directly using eBGP.
Answer:
D
Explanation:
Leaf routers do not learn prefixes from other leaf routers directly using eBGP; instead, leaf routers
learn remote prefixes via spine routers. The spine acts as the route reflector or intermediary
between leaf routers.
Comments
Question 9
Which of the following statements about using BFD with BGP is FALSE?
- A. It can help rapidly detect link failures.
- B. The BFD endpoints agree on the send/receive rate of control packets.
- C. BGP is notified if several BFD control packets are missed.
- D. Using BFD can speed up the BGP advertisement interval.
Answer:
D
Explanation:
BFD helps detect link failures rapidly and notifies BGP to trigger route updates quickly, but it does not
speed up the BGP advertisement interval itself. BGP advertisement intervals are controlled by BGP
timers, not by BFD.
Comments
Question 10
Which of the following statements about the VXLAN tunneling in data centers is FALSE?
- A. VXLAN tunnel endpoints can be on hypervisors, leaf routers, or datacenter gateways.
- B. EVPN routes are exchanged between VXLAN tunnel endpoints.
- C. Each VXLAN tunnel endpoint is automatically assigned with a unique VNI value.
- D. VLXAN tunneling is used to provide Layer 2 connectivity between workloads over a common underlay network.
Answer:
C
Explanation:
VXLAN tunnel endpoints (VTEPs) are configured with VNI (VXLAN Network Identifier) values, but
these VNIs are not automatically assigned; they must be explicitly configured to define Layer 2
segments.
Comments
Page 1 out of 3
Viewing questions 1-10 out of 35
page 2