Question 1
Which of the following message types does RSVP use to set up an LSP? (Choose two)
- A. Path message
- B. iLER message
- C. Resv message
- D. LSP setup call request
- E. eLER message
Answer:
A, C
Comments
Question 2
Assume that, on the Alcatel-Lucent 7750 SR, an LSP is configured with one-to-one FRR and node
protection. Which of the following statements are FALSE? (Choose two)
- A. Each PLR signals a detour LSP that avoids the downstream node. If the downstream node cannot be avoided, a detour LSP that avoids the downstream link is signaled.
- B. The detour LSP can take one or more hops before merging back on the protected LSP.
- C. The merge point of the protected LSP must be the next-next-hop node
- D. The ingress router will set the local protection desired flag in the session attribute object of the path message to inform all routers along the protected LSP path to establish detour LSPs.
- E. The label recording desired flag must be set in the session attribute object in order for the PLR to know what label to swap when using the detour LSP.
Answer:
C, E
Comments
Question 3
Click on the exhibit button below.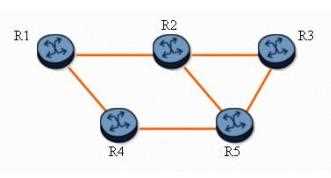
With fast reroute enabled, and given the following:
The protected LSP path is R1-R2-R3.
All links are of equal cost.
Which of the following statements is true? (Choose two)
- A. Router R1 is the LSP originator and is also a PLR.
- B. With one-to-one link or node protection, the detour LSP path is R1-R4-R5-R2-R3.
- C. With one-to-one link or node protection, the detour LSP path is R1-R4-R5-R3.
- D. If the R2-R3 link fails, router R3 becomes a PLR
- E. None of the nodes can be protected with FRR.
Answer:
A, C
Comments
Question 4
Which of the following statements regarding LSP path configuration are true? (Choose three)
- A. The path must include at least one hop.
- B. The path may be used multiple times in a single LSP.
- C. The path may comprise loose hop entries only.
- D. The path must define the LSP's tail end.
- E. The path may be used for multiple LSPs.
Answer:
C, E
Comments
Question 5
Click on the exhibit button below.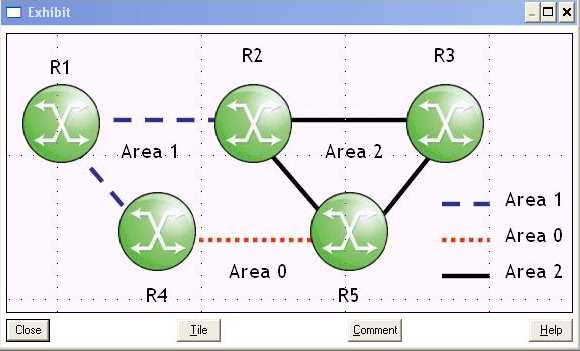
Consider the following:
Routers R1 and R4 are in Area 1.
Routers R4 and R5 in Area 0.
Routers R5 and R3 are in Area 2.
To support LDP-over-RSVP tunnels between routers R1 and R3 over path R1-R4-R5-R3, with which
routers will router R5 require targeted sessions? (Choose two)
- A. Router R1
- B. Router R4
- C. Router R2
- D. Router R3
Answer:
B, D
Comments
Question 6
Which of the following statements best describes downstream unsolicited label distribution?
- A. An LER may answer requests for label mappings immediately, without waiting for a label mapping from the next-hop.
- B. An LER may advertise label mappings to all peers for which it might be a next-hop for a given FEC.
- C. An LER propagates a label mapping downstream for a FEC. only if it has a label mapping for the FEC next-hop.
- D. An LER will only distribute a label for a FEC when it has been requested to do so.
Answer:
B
Comments
Question 7
In MPLS, labels are distributed in the opposite direction of the data flow.
- A. TRUE
- B. FALSE
Answer:
A
Comments
Question 8
Click on the exhibit button below.
Given the configuration below, what is the system ID of the destination node?
- A. 10.32.1.2
- B. 10.1.478
- C. 1048.1.1
- D. Cannot tell from this configuration
- E. 10.1.2.2
Answer:
B
Comments
Question 9
Which of the following is defined by the following statement? All label mappings received from all
peer LSRs are saved.
- A. Conservative label retention
- B. Liberal label retention.
- C. Downstream on demand.
- D. Downstream unsolicited.
Answer:
B
Comments
Question 10
What is the common usage of the MPLS EXP bits?
- A. Each implementation can use them as they see fit.
- B. They are used to carry the Ethertype value.
- C. They are used to carry the TTL value.
- D. They are used to carry QoS classification.
- E. They are used to carry fragmentation flag information
Answer:
D
Comments
Page 1 out of 24
Viewing questions 1-10 out of 249
page 2