microsoft sc-900 practice test
microsoft security, compliance, and identity fundamentals
Last exam update: Jun 23 ,2025
Question 1
What are two reasons to deploy multiple virtual networks instead of using just one virtual network? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. to meet governance policies
- B. to connect multiple types of resources
- C. to separate the resources for budgeting
- D. to isolate the resources
Answer:
bd
Question 2
HOTSPOT Select the answer that correctly completes the sentence.
Hot Area: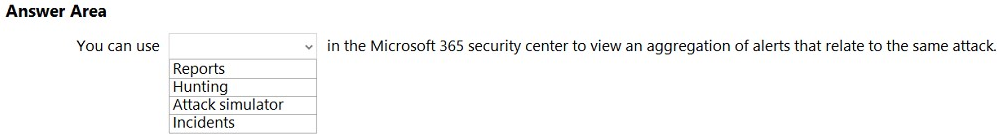
Answer:
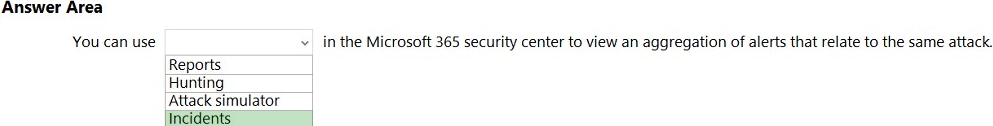
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/threat-analytics?view=o365-worldwide
Question 3
HOTSPOT Select the answer that correctly completes the sentence.
Hot Area: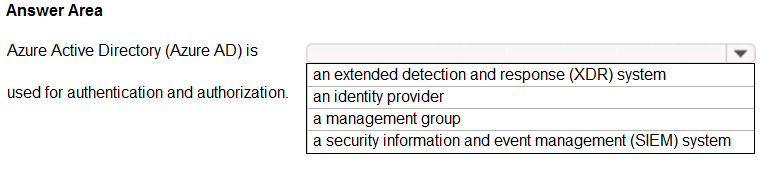
Answer:
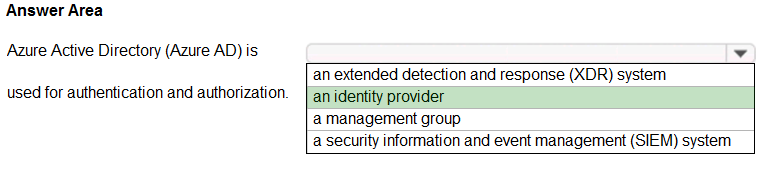
Azure Active Directory (Azure AD) is a cloud-based user identity and authentication service.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/enterprise/about-microsoft-365-identity?view=o365-worldwide
Question 4
You plan to implement a security strategy and place multiple layers of defense throughout a network infrastructure.
Which security methodology does this represent?
- A. threat modeling
- B. identity as the security perimeter
- C. defense in depth
- D. the shared responsibility model
Answer:
c
Reference:
https://docs.microsoft.com/en-us/learn/modules/secure-network-connectivity-azure/2-what-is-defense-in-depth
Question 5
DRAG DROP Match the Azure networking service to the appropriate description.
To answer, drag the appropriate service from the column on the left to its description on the right. Each service may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place: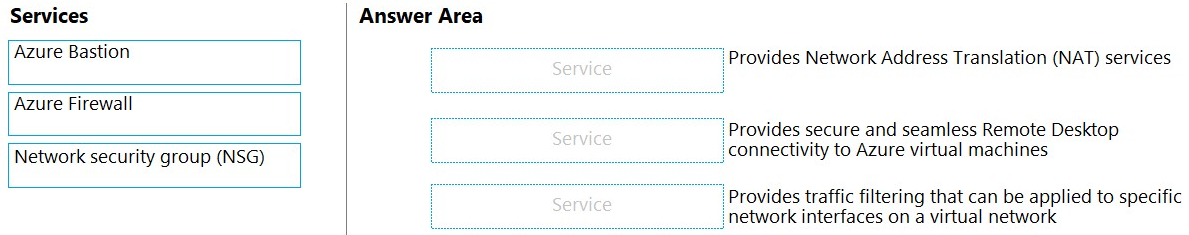
Answer:

Box 1: Azure Firewall -
Azure Firewall provide Source Network Address Translation and Destination Network Address Translation.
Box 2: Azure Bastion -
Azure Bastion provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS.
Box 3: Network security group (NSG)
You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network.
Reference:
https://docs.microsoft.com/en-us/azure/networking/fundamentals/networking-overview https://docs.microsoft.com/en-us/azure/bastion/bastion-overview https://docs.microsoft.com/en-us/azure/firewall/features https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
Question 6
What is a characteristic of a sensitivity label in Microsoft 365?
- A. encrypted
- B. restricted to predefined categories
- C. persistent
Answer:
c
Question 7
In a Core eDiscovery workflow, what should you do before you can search for content?
- A. Create an eDiscovery hold.
- B. Run Express Analysis.
- C. Configure attorney-client privilege detection.
- D. Export and download results.
Answer:
a
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-core-ediscovery?view=o365-worldwide
Question 8
Which Microsoft 365 compliance center feature can you use to identify all the documents on a Microsoft SharePoint Online site that contain a specific key word?
- A. Audit
- B. Compliance Manager
- C. Content Search
- D. Alerts
Answer:
c
The Content Search tool in the Security & Compliance Center can be used to quickly find email in Exchange mailboxes, documents in SharePoint sites and
OneDrive locations, and instant messaging conversations in Skype for Business.
The first step is to starting using the Content Search tool to choose content locations to search and configure a keyword query to search for specific items.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/search-for-content?view=o365-worldwide
Question 9
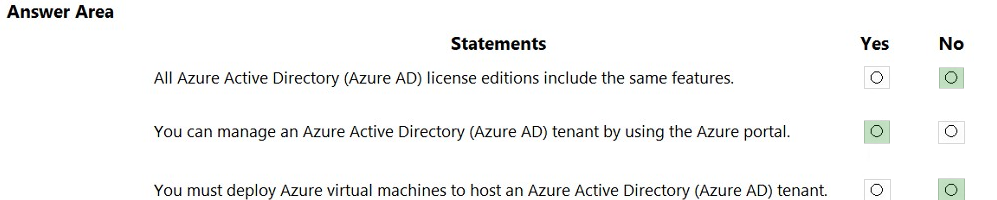
HOTSPOT For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
Question 10
HOTSPOT
Select the answer that correctly completes the sentence.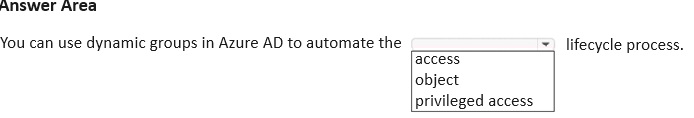
Answer: