microsoft sc-100 practice test
Microsoft Cybersecurity Architect
Last exam update: Oct 15 ,2024
Question 1
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points.
You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend enabling just-in-time (JIT) VM access on all virtual machines.
Does this meet the goal?
- A. Yes
- B. No
Answer:
a
Secure management ports - Brute force attacks often target management ports. Use these recommendations to reduce your exposure with tools like just-in-time
VM access and network security groups.
Recommendations:
- Internet-facing virtual machines should be protected with network security groups
- Management ports of virtual machines should be protected with just-in-time network access control
- Management ports should be closed on your virtual machines
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/secure-score-security-controls
Question 2
You have Windows 11 devices and Microsoft 365 E5 licenses.
You need to recommend a solution to prevent users from accessing websites that contain adult content such as gambling sites.
What should you include in the recommendation?
- A. Compliance Manager
- B. Microsoft Defender for Cloud Apps
- C. Microsoft Endpoint Manager
- D. Microsoft Defender for Endpoint
Answer:
d
Web content filtering is part of the Web protection capabilities in Microsoft Defender for Endpoint. It enables your organization to track and regulate access to websites based on their content categories. Many of these websites, while not malicious, might be problematic because of compliance regulations, bandwidth usage, or other concerns.
Note: Turn on web content filtering
From the left-hand navigation in Microsoft 365 Defender portal, select Settings > Endpoints > General > Advanced Features. Scroll down until you see the entry for Web content filtering. Switch the toggle to On and Save preferences.
Configure web content filtering policies
Web content filtering policies specify which site categories are blocked on which device groups. To manage the policies, go to Settings > Endpoints > Web content filtering (under Rules).
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/web-content-filtering
Question 3
Your company has the virtual machine infrastructure shown in the following table.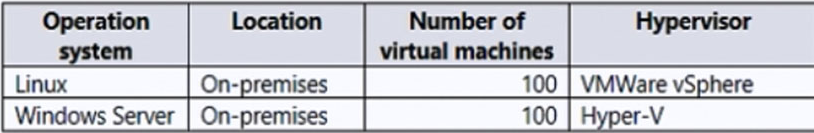
The company plans to use Microsoft Azure Backup Server (MABS) to back up the virtual machines to Azure.
You need to provide recommendations to increase the resiliency of the backup strategy to mitigate attacks such as ransomware.
What should you include in the recommendation?
- A. Use geo-redundant storage (GRS).
- B. Maintain multiple copies of the virtual machines.
- C. Encrypt the backups by using customer-managed keys (CMKS).
- D. Require PINs to disable backups.
Answer:
d
Azure Backup -
Checks have been added to make sure only valid users can perform various operations. These include adding an extra layer of authentication. As part of adding an extra layer of authentication for critical operations, you're prompted to enter a security PIN before modifying online backups.
Authentication to perform critical operations
As part of adding an extra layer of authentication for critical operations, you're prompted to enter a security PIN when you perform Stop Protection with Delete data and Change Passphrase operations.
Reference:
https://docs.microsoft.com/en-us/azure/security/fundamentals/backup-plan-to-protect-against-ransomware https://docs.microsoft.com/en-us/azure/backup/backup-azure-security-feature#prevent-attacks
Question 4
You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements.
Which two services should you leverage in the strategy? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. Azure AD Conditional Access
- B. access reviews in Azure AD
- C. Microsoft Defender for Cloud
- D. Microsoft Defender for Cloud Apps
- E. Microsoft Defender for Endpoint
Answer:
bd
Scenario: Litware identifies the following application security requirements:
Monitor and control access to Microsoft SharePoint Online and Exchange Online data in real time.
B: Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. User's access can be reviewed on a regular basis to make sure only the right people have continued access.
D: The Defender for Cloud Apps framework
Discover and control the use of Shadow IT: Identify the cloud apps, IaaS, and PaaS services used by your organization. Investigate usage patterns, assess the risk levels and business readiness of more than 25,000 SaaS apps against more than 80 risks. Start managing them to ensure security and compliance.
Protect your sensitive information anywhere in the cloud: Understand, classify, and protect the exposure of sensitive information at rest. Leverage out-of-the box policies and automated processes to apply controls in real time across all your cloud apps.
Etc.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview https://docs.microsoft.com/en-us/defender-cloud-apps/what-is-defender-for-cloud-apps
Question 5
You are designing a ransomware response plan that follows Microsoft Security Best Practices.
You need to recommend a solution to limit the scope of damage of ransomware attacks without being locked out.
What should you include in the recommendation?
- A. device compliance policies
- B. Privileged Access Workstations (PAWs)
- C. Customer Lockbox for Microsoft Azure
- D. emergency access accounts
Answer:
b
Question 6
Your company has on-premises Microsoft SQL Server databases.
The company plans to move the databases to Azure.
You need to recommend a secure architecture for the databases that will minimize operational requirements for patching and protect sensitive data by using dynamic data masking. The solution must minimize costs.
What should you include in the recommendation?
- A. Azure SQL Managed Instance
- B. Azure Synapse Analytics dedicated SQL pools
- C. Azure SQL Database
- D. SQL Server on Azure Virtual Machines
Answer:
a
Azure SQL Managed Instance is the intelligent, scalable cloud database service that combines the broadest SQL Server database engine compatibility with all the benefits of a fully managed and evergreen platform as a service. SQL Managed Instance has near 100% compatibility with the latest SQL Server (Enterprise
Edition) database engine, providing a native virtual network (VNet) implementation that addresses common security concerns, and a business model favorable for existing SQL Server customers. SQL Managed Instance allows existing SQL Server customers to lift and shift their on-premises applications to the cloud with minimal application and database changes. At the same time, SQL Managed Instance preserves all PaaS capabilities (automatic patching and version updates, automated backups, high availability) that drastically reduce management overhead and TCO.
Note: Azure SQL Database, Azure SQL Managed Instance, and Azure Synapse Analytics support dynamic data masking. Dynamic data masking limits sensitive data exposure by masking it to non-privileged users.
Incorrect:
Not D: SQL Server does not support dynamic data masking.
Reference:
https://docs.microsoft.com/en-us/azure/azure-sql/managed-instance/sql-managed-instance-paas-overview?view=azuresql https://docs.microsoft.com/en-us/azure/azure-sql/database/dynamic-data-masking-overview?view=azuresql
Question 7
You have an Azure AD tenant that syncs with an Active Directory Domain Services (AD DS) domain.
You have an on-premises datacenter that contains 100 servers. The servers run Windows Server and are backed up by using Microsoft Azure Backup Server (MABS).
You are designing a recovery solution for ransomware attacks. The solution follows Microsoft Security Best Practices.
You need to ensure that a compromised administrator account cannot be used to delete the backups.
What should you do?
- A. From Azure Backup, configure multi-user authorization by using Resource Guard.
- B. From Microsoft Azure Backup Setup, register MABS with a Recovery Services vault.
- C. From a Recovery Services vault, generate a security PIN for critical operations.
- D. From Azure AD Privileged Identity Management (PIM), create a role assignment for the Backup Contributor role.
Answer:
c
Question 8
HOTSPOT Your company has a Microsoft 365 ES subscription, an Azure subscription, on-premises applications, and Active Directory Domain Services (AD DS).
You need to recommend an identity security strategy that meets the following requirements:
Ensures that customers can use their Facebook credentials to authenticate to an Azure App Service website
Ensures that partner companies can access Microsoft SharePoint Online sites for the project to which they are assigned
The solution must minimize the need to deploy additional infrastructure components.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: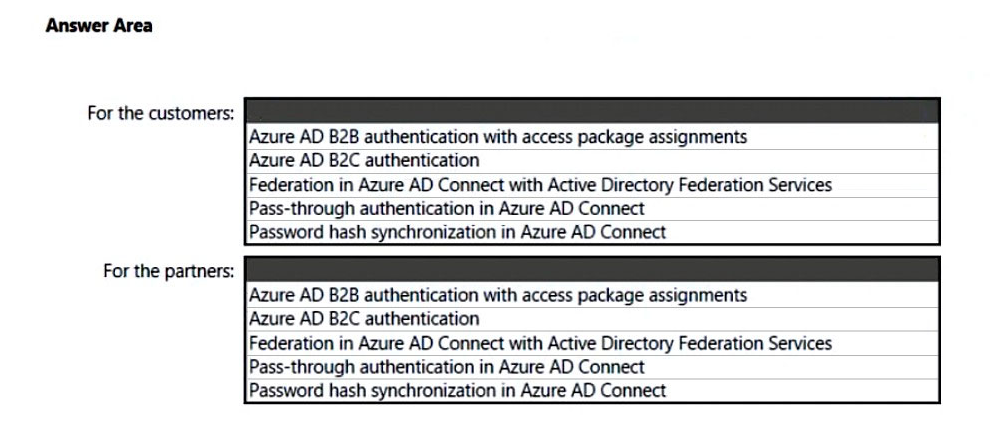
Answer:
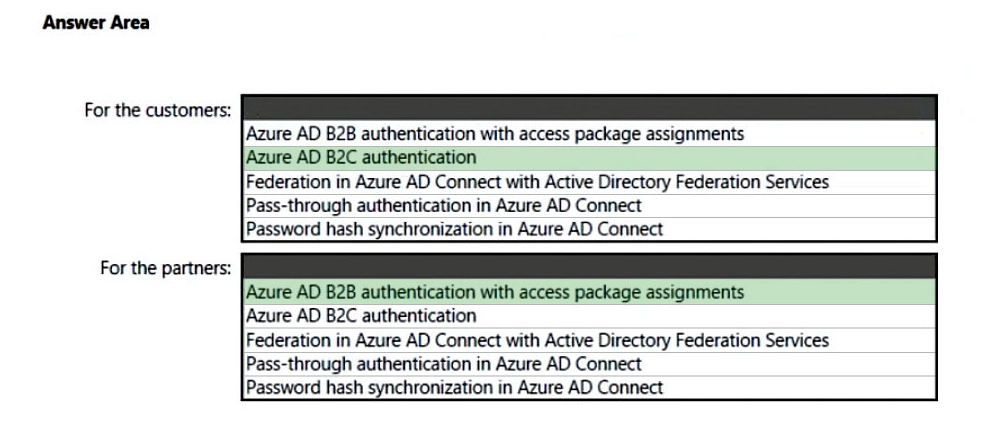
Box 1: Azure AD B2C authentication
Ensures that customers can use their Facebook credentials to authenticate to an Azure App Service website.
You can set up sign-up and sign-in with a Facebook account using Azure Active Directory B2C.
Box 2: Azure AD B2B authentication with access package assignments
Govern access for external users in Azure AD entitlement management
Azure AD entitlement management uses Azure AD business-to-business (B2B) to share access so you can collaborate with people outside your organization.
With Azure AD B2B, external users authenticate to their home directory, but have a representation in your directory. The representation in your directory enables the user to be assigned access to your resources.
Incorrect:
Not: Password hash synchronization in Azure AD connect
The partners are not integrated with AD DS.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory-b2c/identity-provider-facebook?pivots=b2c-user-flow https://docs.microsoft.com/en-us/azure/active-directory/governance/entitlement-management-external-users https://docs.microsoft.com/en-us/microsoft-365/enterprise/microsoft-365-integration
Question 9
Your company has a Microsoft 365 E5 subscription.
Users use Microsoft Teams, Exchange Online, SharePoint Online, and OneDrive for sharing and collaborating.
The company identifies protected health information (PHI) within stored documents and communications.
What should you recommend using to prevent the PHI from being shared outside the company?
- A. sensitivity label policies
- B. data loss prevention (DLP) policies
- C. insider risk management policies
- D. retention policies
Answer:
a
What sensitivity labels can do -
After a sensitivity label is applied to an email or document, any configured protection settings for that label are enforced on the content. You can configure a sensitivity label to:
* Protect content in containers such as sites and groups when you enable the capability to use sensitivity labels with Microsoft Teams, Microsoft 365 groups, and
SharePoint sites.
* Encrypt emails and documents to prevent unauthorized people from accessing this data. You can additionally choose which users or group have permissions to perform which actions and for how long. For example, you can choose to allow all users in your organization to modify a document while a specific group in another organization can only view it. Alternatively, instead of administrator-defined permissions, you can allow your users to assign permissions to the content when they apply the label.
* Mark the content when you use Office apps, by adding watermarks, headers, or footers to email or documents that have the label applied. Watermarks can be applied to documents but not email.
* Etc.
Note: Publish sensitivity labels by creating a label policy
1. From the Microsoft Purview compliance portal, select Solutions > Information protection > Label policies
2. On the Label policies page, select Publish label to start the Create policy configuration: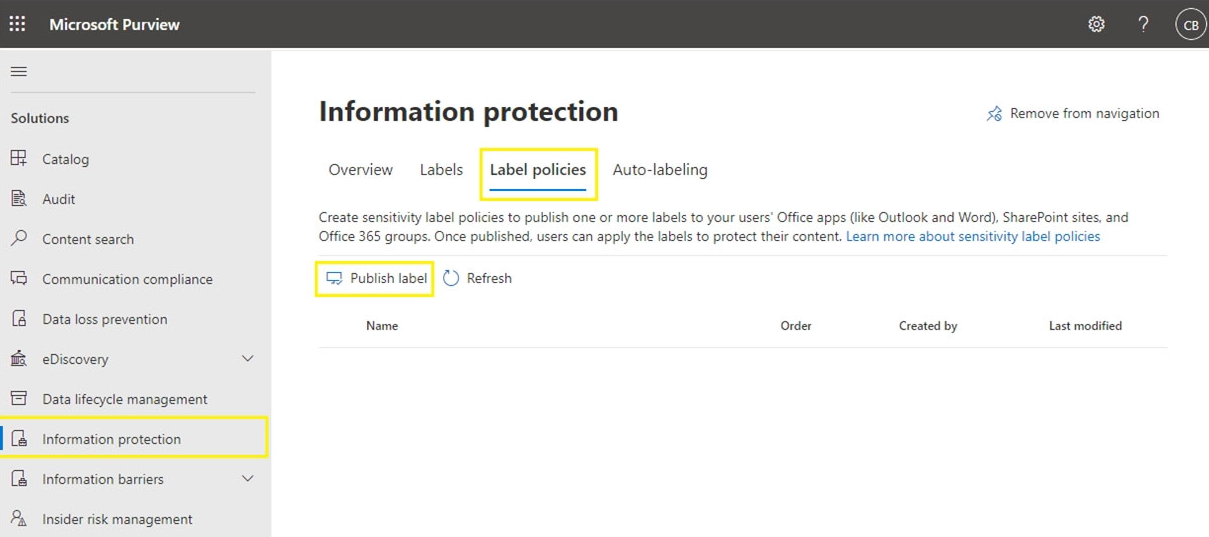
3. On the Choose sensitivity labels to publish page, select the Choose sensitivity labels to publish link. Select the labels that you want to make available in apps and to services, and then select Add.
4. Etc.
Incorrect:
Not B: In this scenario the company itself has identified the sensitive information. This means that sensitive labels are enough, and there is no need for Data loss prevention (DLP) polices.
Note: With DLP policies, you can identify, monitor, and automatically protect sensitive information across Office 365. Data loss prevention policies can use sensitivity labels and sensitive information types to identify sensitive information.
Note: Microsoft 365 includes many sensitive information types that are ready for you to use in DLP policies and for automatic classification with sensitivity and retention labels.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels https://docs.microsoft.com/en-us/security/compass/information-protection-and-storage-capabilities https://docs.microsoft.com/en-us/microsoft-365/compliance/create-sensitivity-labels?view=o365-worldwide#publish-sensitivity-labels-by-creating-a-label-policy
Question 10
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your on-premises network contains an e-commerce web app that was developed in Angular and Node,js. The web app uses a MongoDB database.
You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.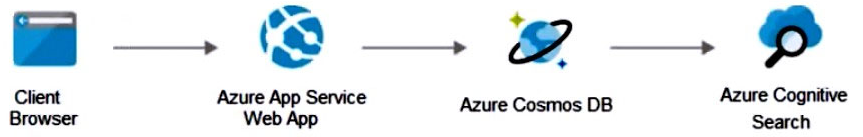
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model.
Solution: You recommend implementing Azure Key Vault to store credentials.
Does this meet the goal?
- A. Yes
- B. No
Answer:
b
Instead use solution: You recommend creating private endpoints for the web app and the database layer.
Note:
How to Use Azure Private Endpoints to Restrict Public Access to WebApps.
As an Azure administrator or architect, you are sometimes asked the question: How can we safely deploy internal business applications to Azure App Services?
These applications characteristically are:
Not accessible from the public internet.
Accessible from within the on-premises corporate network
Accessible via an authorized VPN client from outside the corporate network.
For such scenarios, we can use Azure Private Links, which enables private and secure access to Azure PaaS services over Azure Private Endpoints, along with the Site-to-Site VPN, Point-to-Site VPN, or the Express Route. Azure Private Endpoint is a read-only network interface service associated with the Azure PAAS
Services. It allows you to bring deployed sites into your virtual network, limiting access to them at the network level.
It uses one of the private IP addresses from your Azure VNet and associates it with the Azure App Services. These services are called Private Link resources.
They can be Azure Storage, Azure Cosmos DB, SQL, App Services Web App, your own / partner owned services, Azure Backups, Event Grids, Azure Service
Bus, or Azure Automations.
Reference:
https://www.varonis.com/blog/securing-access-azure-webapps