Question 1
HOTSPOT
You need to recommend a security methodology for a DevOps development process based on the Microsoft Cloud Adoption Framework for Azure.
During which stage of a continuous integration and continuous deployment (CI/CD) DevOps process should each security-related task be performed? To answer, select the appropriate options in the answer area.
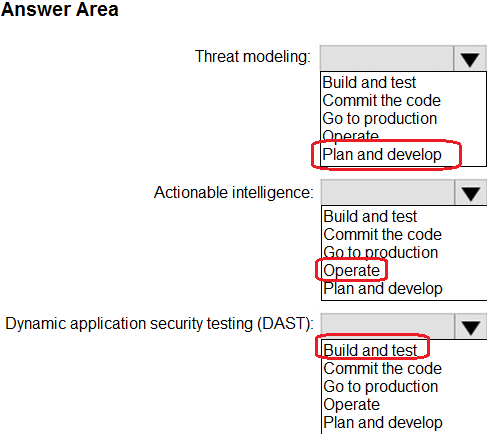
NOTE: Each correct selection is worth one point.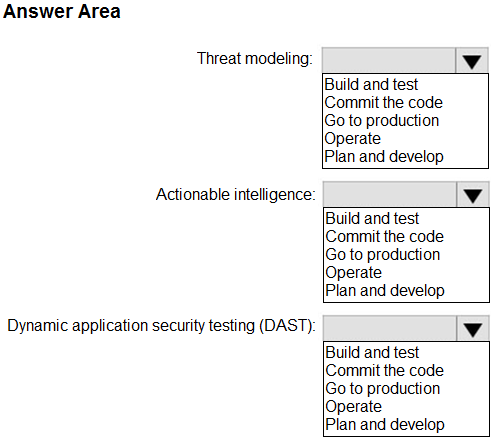
Answer:
Comments
Question 2
You need to recommend a solution to resolve the virtual machine issue.
What should you include in the recommendation?
- A. Enable the Qualys scanner in Defender for Cloud.
- B. Onboard the virtual machines to Microsoft Defender for Endpoint.
- C. Create a device compliance policy in Microsoft Endpoint Manager.
- D. Onboard the virtual machines to Azure Arc.
Answer:
b
Scenario: 20 virtual machines that are configured as application servers and are NOT onboarded to Microsoft Defender for Cloud.
Existing Environment. Problem Statements
The secure score in Defender for Cloud shows that all the virtual machines generate the following recommendation: Machines should have a vulnerability assessment solution.
All the virtual machines must be compliant in Defender for Cloud.
Note: Deploying Microsoft Defender for Endpoint is a two-step process.
Onboard devices to the service -
Configure capabilities of the service
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/deploy-vulnerability-assessment-vm
Comments
Question 3
You are evaluating an Azure environment for compliance.
You need to design an Azure Policy implementation that can be used to evaluate compliance without changing any resources.
Which effect should you use in Azure Policy?
- A. Deny
- B. Modify
- C. Append
- D. Disabled
Answer:
d
This effect is useful for testing situations or for when the policy definition has parameterized the effect. This flexibility makes it possible to disable a single assignment instead of disabling all of that policy's assignments.
An alternative to the Disabled effect is enforcementMode, which is set on the policy assignment. When enforcementMode is Disabled, resources are still evaluated.
Incorrect:
Not A: Deny is used to prevent a resource request that doesn't match defined standards through a policy definition and fails the request.
Not B: Modify evaluates before the request gets processed by a Resource Provider during the creation or updating of a resource. The Modify operations are applied to the request content when the if condition of the policy rule is met. Each Modify operation can specify a condition that determines when it's applied.
Operations with conditions that are evaluated to false are skipped.
Not C: Append is used to add additional fields to the requested resource during creation or update.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects
Comments
Question 4
HOTSPOT You need to recommend a SIEM and SOAR strategy that meets the hybrid requirements, the Microsoft Sentinel requirements, and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: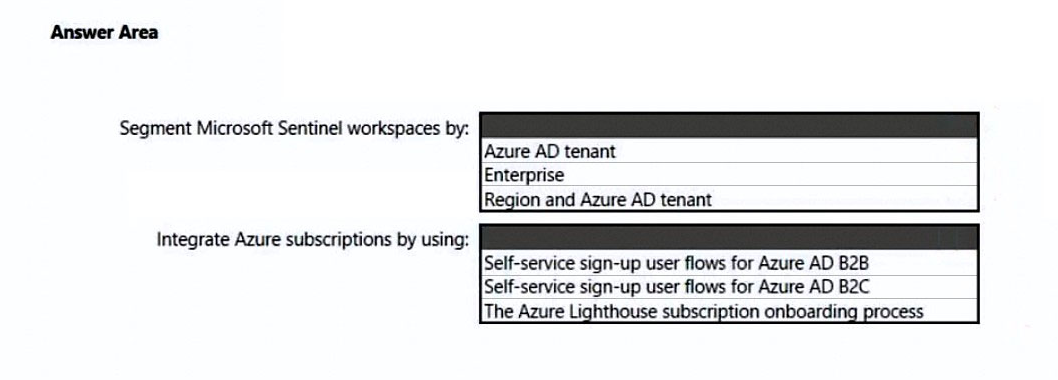
Answer:
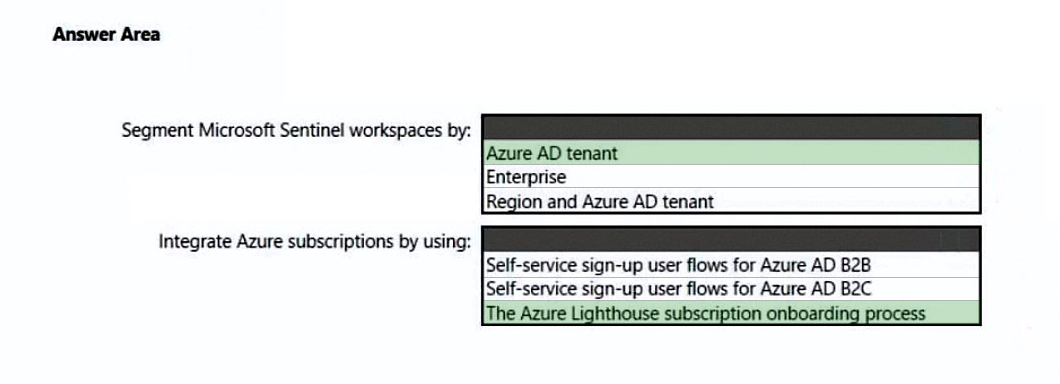
Box 1: Azure tenant -
Microsoft Sentinel multiple workspace architecture
There are cases where a single SOC (Security Operations Center) needs to centrally manage and monitor multiple Microsoft Sentinel workspaces, potentially across Azure Active Directory (Azure AD) tenants.
An MSSP Microsoft Sentinel Service.
A global SOC serving multiple subsidiaries, each having its own local SOC.
A SOC monitoring multiple Azure AD tenants within an organization.
To address these cases, Microsoft Sentinel offers multiple-workspace capabilities that enable central monitoring, configuration, and management, providing a single pane of glass across everything covered by the SOC. This diagram shows an example architecture for such use cases.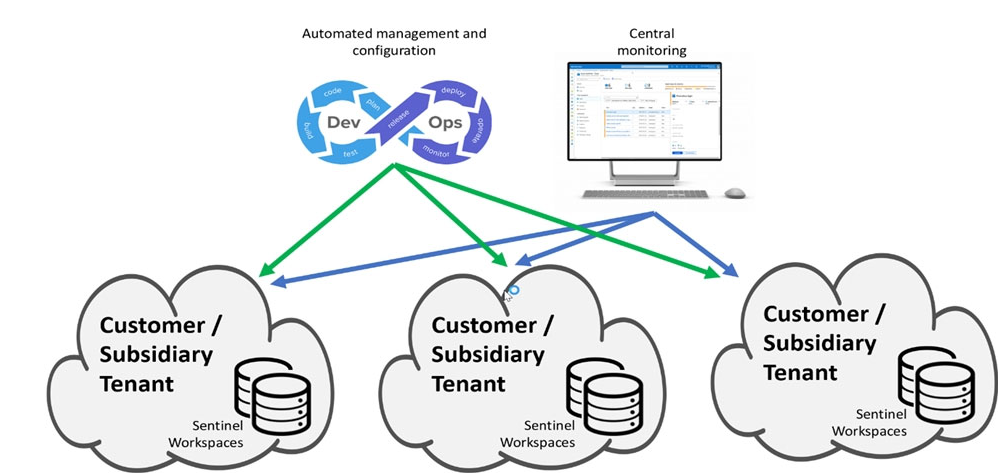
This model offers significant advantages over a fully centralized model in which all data is copied to a single workspace.
Scenario:
Requirements. Microsoft Sentinel Requirements
Litware plans to leverage the security information and event management (SIEM) and security orchestration automated response (SOAR) capabilities of Microsoft
Sentinel. The company wants to centralize Security Operations Center (SOC) by using Microsoft Sentinel.
Hybrid Requirements -
Litware identifies the following hybrid cloud requirements:
Provide centralized, cross-tenant subscription management without the overhead of maintaining guest accounts.
Box 2: Azure Lighthouse subscription onboarding process
You can use Azure Lighthouse to extend all cross-workspace activities across tenant boundaries, allowing users in your managing tenant to work on Microsoft
Sentinel workspaces across all tenants.
Azure Lighthouse enables you to see and manage Azure resources from different tenancies, in the one place, with the power of delegated administration. That tenancy may be a customer (for example, if you're a managed services provider with a support contract arrangement in place), or a separate Azure environment for legal or financial reasons (like franchisee groups or Enterprises with large brand groups).
Incorrect:
* not Azure AD B2B
Azure AD B2B uses guest account, which goes against the requirements in this scenario,
Note: Azure Active Directory (Azure AD) B2B collaboration is a feature within External Identities that lets you invite guest users to collaborate with your organization.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/extend-sentinel-across-workspaces-tenants https://docs.microsoft.com/en-us/azure/sentinel/best-practices-workspace-architecture https://techcommunity.microsoft.com/t5/itops-talk-blog/onboarding-to-azure-lighthouse-using-a-template/ba-p/1091786 https://docs.microsoft.com/en-us/azure/active-directory/external-identities/what-is-b2b
Comments
Question 5
You need to recommend a strategy for routing internet-bound traffic from the landing zones. The solution must meet the landing zone requirements.
What should you recommend as part of the landing zone deployment?
- A. local network gateways
- B. forced tunneling
- C. service chaining
Answer:
c
Service chaining.
Service chaining enables you to direct traffic from one virtual network to a virtual appliance or gateway in a peered network through user-defined routes.
You can deploy hub-and-spoke networks, where the hub virtual network hosts infrastructure components such as a network virtual appliance or VPN gateway. All the spoke virtual networks can then peer with the hub virtual network. Traffic flows through network virtual appliances or VPN gateways in the hub virtual network.
Virtual network peering enables the next hop in a user-defined route to be the IP address of a virtual machine in the peered virtual network, or a VPN gateway.
You can't route between virtual networks with a user-defined route that specifies an Azure ExpressRoute gateway as the next hop type.
Incorrect:
Not B: Forced tunneling lets you redirect or force all Internet-bound traffic back to your on-premises location via a Site-to-Site VPN tunnel for inspection and auditing. This is a critical security requirement for most enterprise IT policies. If you don't configure forced tunneling, Internet-bound traffic from your VMs in Azure always traverses from the Azure network infrastructure directly out to the Internet, without the option to allow you to inspect or audit the traffic. Unauthorized
Internet access can potentially lead to information disclosure or other types of security breaches.
ExpressRoute forced tunneling is not configured via this mechanism, but instead, is enabled by advertising a default route via the ExpressRoute BGP peering sessions.
Note:
Requirements. Planned Changes -
Litware plans to implement the following changes:
Design a landing zone strategy to refactor the existing Azure environment of Litware and deploy all future Azure workloads.
Requirements. Azure Landing Zone Requirements
Litware identifies the following landing zone requirements:
Route all internet-bound traffic from landing zones through Azure Firewall in a dedicated Azure subscription.
Provide a secure score scoped to the landing zone.
Ensure that the Azure virtual machines in each landing zone communicate with Azure App Service web apps in the same zone over the Microsoft backbone network, rather than over public endpoints.
Minimize the possibility of data exfiltration.
Maximize network bandwidth.
The landing zone architecture will include the dedicated subscription, which will serve as the hub for internet and hybrid connectivity. Each landing zone will have the following characteristics:
Be created in a dedicated subscription.
Use a DNS namespace of litware.com.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-peering-overview#service-chaining https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-forced-tunneling-rm
Comments
Question 6
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions that allow traffic from the Front Door service tags.
Does this meet the goal?
- A. Yes
- B. No
Answer:
b
Correct Solution: You recommend access restrictions based on HTTP headers that have the Front Door ID.
Restrict access to a specific Azure Front Door instance.
Traffic from Azure Front Door to your application originates from a well-known set of IP ranges defined in the AzureFrontDoor.Backend service tag. Using a service tag restriction rule, you can restrict traffic to only originate from Azure Front Door. To ensure traffic only originates from your specific instance, you will need to further filter the incoming requests based on the unique http header that Azure Front Door sends.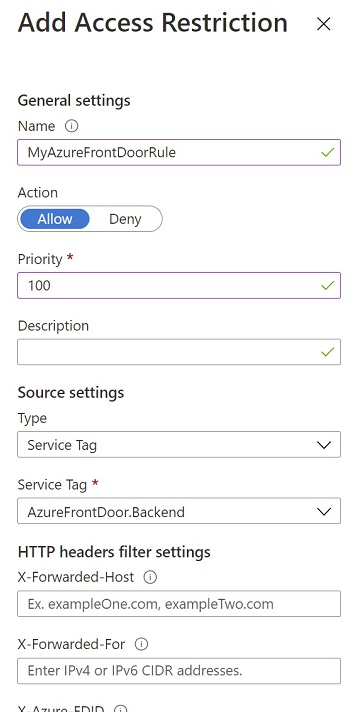
Reference:
https://docs.microsoft.com/en-us/azure/app-service/app-service-ip-restrictions#managing-access-restriction-rules
Comments
Question 7
HOTSPOT You need to recommend a solution to evaluate regulatory compliance across the entire managed environment. The solution must meet the regulatory compliance requirements and the business requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
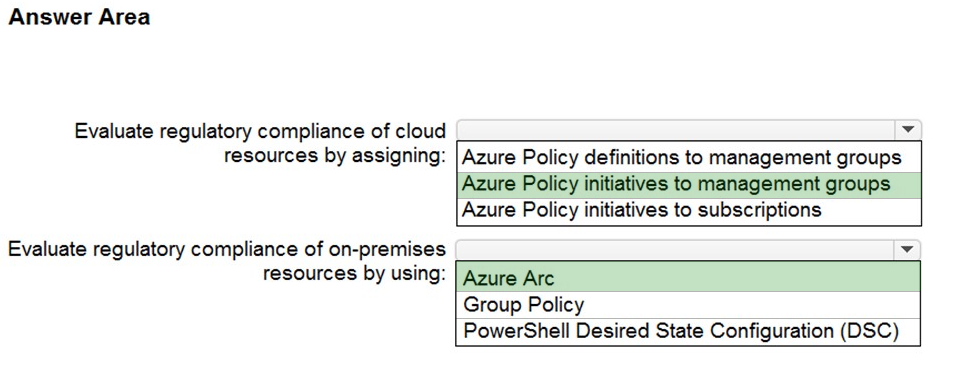
Box 1: Azure Policy initiatives to management groups
If your organization has many Azure subscriptions, you may need a way to efficiently manage access, policies, and compliance for those subscriptions.
Management groups provide a governance scope above subscriptions. You organize subscriptions into management groups the governance conditions you apply cascade by inheritance to all associated subscriptions.
If you plan to apply a policy definition to multiple subscriptions, the location must be a management group that contains the subscriptions you assign the policy to.
The same is true for an initiative definition.
With an initiative definition, you can group several policy definitions to achieve one overarching goal. An initiative evaluates resources within scope of the assignment for compliance to the included policies.
Incorrect:
Not: Azure Policy initiatives to subscriptions
Must use a management group as we have multiple subscriptions.
Scenario:
Requirements. Business Requirements
Litware identifies the following business requirements:
Minimize any additional on-premises infrastructure.
Minimize the operational costs associated with administrative overhead.
Box 2: Azure Arc -
With Azure Arc:
Meet governance and compliance standards for apps, infrastructure, and data with Azure Policy.
Take advantage of elastic scale, consistent on-premises and multicloud management, and cloud-style billing models.
Note: Azure Arc is a bridge that extends the Azure platform to help you build applications and services with the flexibility to run across datacenters, at the edge, and in multicloud environments. Develop cloud-native applications with a consistent development, operations, and security model. Azure Arc runs on both new and existing hardware, virtualization and Kubernetes platforms, IoT devices, and integrated systems.
Reference:
https://docs.microsoft.com/en-us/azure/governance/management-groups/overview https://azure.microsoft.com/en-us/services/azure-arc/#product-overview
Comments
Question 8
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You need to enforce ISO 27001:2013 standards for the subscription. The solution must ensure that noncompliant resources are remediated automatically.
What should you use?
- A. Azure Policy
- B. Azure Blueprints
- C. the regulatory compliance dashboard in Defender for Cloud
- D. Azure role-based access control (Azure RBAC)
Answer:
a
Control mapping of the ISO 27001 Shared Services blueprint sample
The following mappings are to the ISO 27001:2013 controls. Use the navigation on the right to jump directly to a specific control mapping. Many of the mapped controls are implemented with an Azure Policy initiative.
Open Policy in the Azure portal and select the Definitions page. Then, find and select the [Preview] Audit ISO 27001:2013 controls and deploy specific VM
Extensions to support audit requirements built-in policy initiative.
Note: Security Center can now auto provision the Azure Policy's Guest Configuration extension (in preview)
Azure Policy can audit settings inside a machine, both for machines running in Azure and Arc connected machines. The validation is performed by the Guest
Configuration extension and client.
With this update, you can now set Security Center to automatically provision this extension to all supported machines.
Enforcing a secure configuration, based on a specific recommendation, is offered in two modes:
Using the Deny effect of Azure Policy, you can stop unhealthy resources from being created
Using the Enforce option, you can take advantage of Azure Policy's DeployIfNotExist effect and automatically remediate non-compliant resources upon creation
Reference:
https://docs.microsoft.com/en-us/azure/governance/blueprints/samples/iso27001-shared/control-mapping https://docs.microsoft.com/en-us/azure/defender-for-cloud/release-notes-archive https://docs.microsoft.com/en-us/azure/defender-for-cloud/prevent-misconfigurations
Comments
Question 9
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud.
The company signs a contract with the United States government.
You need to review the current subscription for NIST 800-53 compliance.
What should you do first?
- A. From Defender for Cloud, enable Defender for Cloud plans.
- B. From Azure Policy, assign a built-in initiative that has a scope of the subscription.
- C. From Defender for Cloud, review the secure score recommendations.
- D. From Microsoft Defender for Cloud Apps, create an access policy for cloud applications.
Answer:
b
Comments
Question 10
Your company has an on-premises network, an Azure subscription, and a Microsoft 365 E5 subscription.
The company uses the following devices:
Computers that run either Windows 10 or Windows 11
Tablets and phones that run either Android or iOS
You need to recommend a solution to classify and encrypt sensitive Microsoft Office 365 data regardless of where the data is stored.
What should you include in the recommendation?
- A. eDiscovery
- B. Microsoft Information Protection
- C. Compliance Manager
- D. retention policies
Answer:
b
Protect your sensitive data with Microsoft Purview.
Implement capabilities from Microsoft Purview Information Protection (formerly Microsoft Information Protection) to help you discover, classify, and protect sensitive information wherever it lives or travels.
Note: You can use Microsoft Information Protection: Microsoft Purview for Auditing and Analytics in Outlook for iOS, Android, and Mac (DoD).
Incorrect:
Not A: Electronic discovery, or eDiscovery, is the process of identifying and delivering electronic information that can be used as evidence in legal cases. You can use eDiscovery tools in Microsoft Purview to search for content in Exchange Online, OneDrive for Business, SharePoint Online, Microsoft Teams, Microsoft 365
Groups, and Yammer teams. You can search mailboxes and sites in the same eDiscovery search, and then export the search results. You can use Microsoft
Purview eDiscovery (Standard) cases to identify, hold, and export content found in mailboxes and sites. If your organization has an Office 365 E5 or Microsoft 365
E5 subscription (or related E5 add-on subscriptions), you can further manage custodians and analyze content by using the feature-rich Microsoft Purview eDiscovery (Premium) solution in Microsoft 365.
Not C: What does compliance Manager do?
Compliance managers ensure that a business, its employees and its projects comply with all relevant regulations and specifications. This could include health and safety, environmental, legal or quality standards, as well as any ethical policies the company may have.
Not D: A retention policy (also called a 'schedule') is a key part of the lifecycle of a record. It describes how long a business needs to keep a piece of information
(record), where it's stored and how to dispose of the record when its time.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection https://docs.microsoft.com/en-us/microsoft-365/compliance/ediscovery?view=o365-worldwide
Comments
Page 1 out of 14
Viewing questions 1-10 out of 142
page 2