Question 1
Your company uses Storage Spaces Direct.
You need to view the available storage in a Storage Space Direct storage pool.
What should you use?
- A. System Configuration
- B. Resource Monitor
- C. the Get-StorageFileServer cmdlet
- D. Windows Admin Center
Answer:
d
Comments
Question 2
HOTSPOT You have three servers named Host1, Host2, and VM1 that run Windows Server. Host1 and Host2 have the Hyper-V server role installed. VM1 is a virtual machine hosted on Host1.
You configure VM1 to replicate to Host2 by using Hyper-V Replica.
Which types of failovers can you perform on VM1 on each host? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: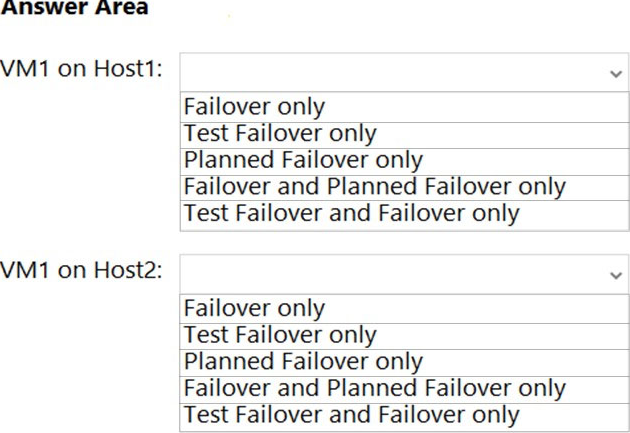
Answer:
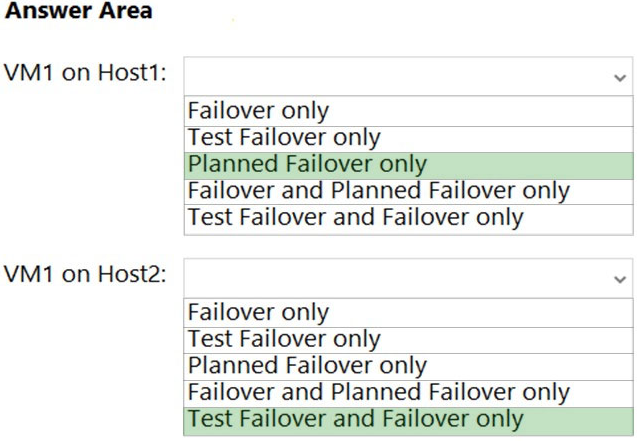
Comments
Question 3
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You have 50 Azure virtual machines that run Windows Server.
You need to ensure that any security exploits detected on the virtual machines are forwarded to Defender for Cloud.
Which extension should you enable on the virtual machines?
- A. Vulnerability assessment for machines
- B. Microsoft Dependency agent
- C. Log Analytics agent for Azure VMs
- D. Guest Configuration agent
Answer:
a
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/deploy-vulnerability-assessment-vm
Comments
Question 4
You have an Azure virtual machine named VM1 that runs Windows Server.
You plan to deploy a new line-of-business (LOB) application to VM1.
You need to ensure that the application can create child processes.
What should you configure on VM1?
- A. Microsoft Defender Credential Guard
- B. Microsoft Defender Application Control
- C. Microsoft Defender SmartScreen
- D. Exploit protection
Answer:
d
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/customize-exploit-protection?view=o365-worldwide
Comments
Question 5
HOTSPOT You need to implement alerts for the domain controllers. The solution must meet the technical requirements.
What should you do on the domain controllers, and what should you create on Azure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: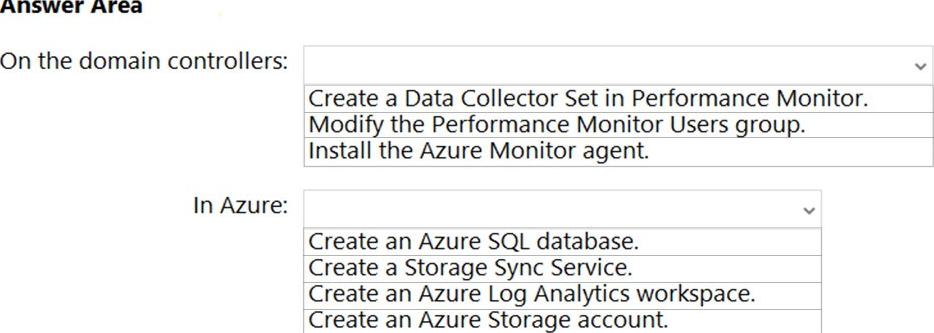
Answer:
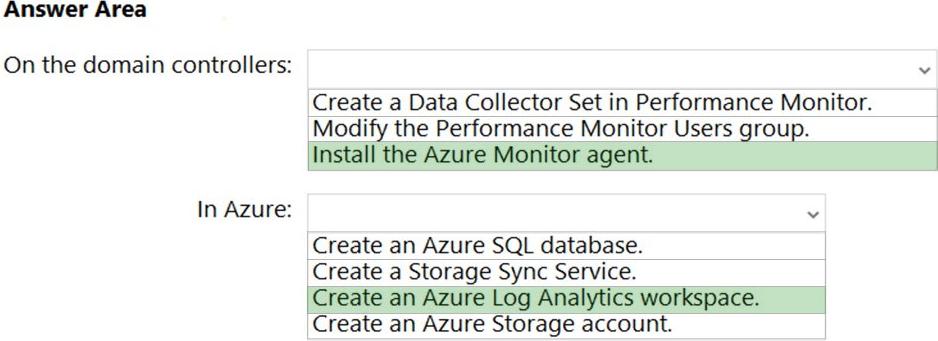
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/agents/azure-monitor-agent-overview?tabs=PowerShellWindows
Comments
Question 6
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises server named Server1 that runs Windows Server.
You have a Microsoft Sentinel instance.
You add the Windows Firewall data connector in Microsoft Sentinel.
You need to ensure that Microsoft Sentinel can collect Windows Firewall logs from Server1.
Solution: You install the Microsoft Integration Runtime on Server1.
Does this meet the goal?
- A. Yes
- B. No
Answer:
b
Comments
Question 7
Your network contains an Active Directory Domain Services (AD DS) domain. The domain contains two servers named Server1 and Server2 that run Windows
Server.
You need to ensure that you can use the Computer Management console to manage Server2. The solution must use the principle of least privilege.
Which two Windows Defender Firewall with Advanced Security rules should you enable on Server2? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. the COM+ Network Access (DCOM-In) rule
- B. all the rules in the Remote Event Log Management group
- C. the Windows Management Instrumentation (WMI-In) rule
- D. the COM+ Remote Administration (DCOM-In) rule
- E. the Windows Management Instrumentation (DCOM-In) rule
Answer:
ab
Reference:
https://docs.microsoft.com/en-us/windows-server/administration/server-manager/configure-remote-management-in-server-manager
Comments
Question 8
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises server named Server1 that runs Windows Server.
You have a Microsoft Sentinel instance.
You add the Windows Firewall data connector in Microsoft Sentinel.
You need to ensure that Microsoft Sentinel can collect Windows Firewall logs from Server1.
Solution: You install the Log Analytics agent on Server1.
Does this meet the goal?
- A. Yes
- B. No
Answer:
a
Comments
Question 9
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From App & browser control, you configure the Exploit protection settings.
Does this meet the goal?
- A. Yes
- B. No
Answer:
b
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/customize-controlled-folders?view=o365-worldwide
Comments
Question 10
You have an Azure subscription. The subscription contains a virtual machine named VM1 that runs Windows Server. The subscription contains the storage accounts shown in the following table.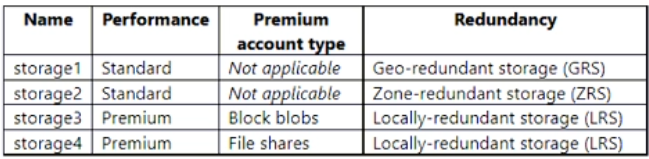
You plan to enable boot diagnostics for VM1.
You need to configure storage for the boot diagnostics logs and snapshots.
Which storage account should you use?
- A. storage1
- B. storage2
- C. storage3
- D. storage4
Answer:
c
Comments
Page 1 out of 14
Viewing questions 1-10 out of 145
page 2