Question 1 Topic 4, Case Study 4Case Study Question View Case
You need to ensure that users can access VM0. The solution must meet the platform protection requirements.
What should you do?
- A. Move VM0 to Subnet1.
- B. On Firewall, configure a network traffic filtering rule.
- C. Assign RT1 to AzureFirewallSubnet.
- D. On Firewall, configure a DNAT rule.
Answer:
A
Explanation:
Azure Firewall has the following known issue:
Conflict with Azure Security Center (ASC) Just-in-Time (JIT) feature.
If a virtual machine is accessed using JIT, and is in a subnet with a user-defined route that points to Azure Firewall as a
default gateway, ASC JIT doesnt work. This is a result of asymmetric routing a packet comes in via the virtual machine
public IP (JIT opened the access), but the return path is via the firewall, which drops the packet because there is no
established session on the firewall.
Solution: To work around this issue, place the JIT virtual machines on a separate subnet that doesnt have a user-defined
route to the firewall.
Scenario: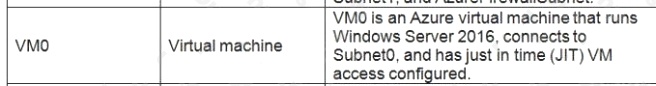
Following the implementation of the planned changes, the IT team must be able to connect to VM0 by using JIT VM access.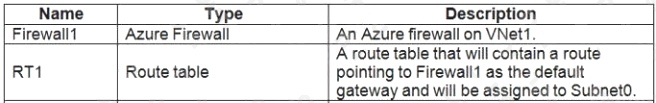
References: https://docs.microsoft.com/en-us/azure/firewall/overview
Comments
Question 2 Topic 4, Case Study 4Case Study Question View Case
HOTSPOT
You need to deploy Microsoft Antimalware to meet the platform protection requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:

Explanation:
Scenario: Microsoft Antimalware must be installed on the virtual machines in RG1. RG1 is a resource group that contains
Vnet1, VM0, and VM1.
Box 1: DeployIfNotExists
DeployIfNotExists executes a template deployment when the condition is met. Azure policy definition Antimalware
Incorrect Answers:
Append:
Append is used to add additional fields to the requested resource during creation or update. A common example is adding
tags on resources such as costCenter or specifying allowed IPs for a storage resource.
Deny:
Deny is used to prevent a resource request that doesn't match defined standards through a policy definition and fails the
request.
Box 2: The Create a Managed Identity setting
When Azure Policy runs the template in the deployIfNotExists policy definition, it does so using a managed identity. Azure
Policy creates a managed identity for each assignment, but must have details about what roles to grant the managed
identity.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects
Implement platform protection
Comments
Question 3 Topic 5, Case Study 5Case Study Question View Case
HOTSPOT
What is the membership of Group1 and Group2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: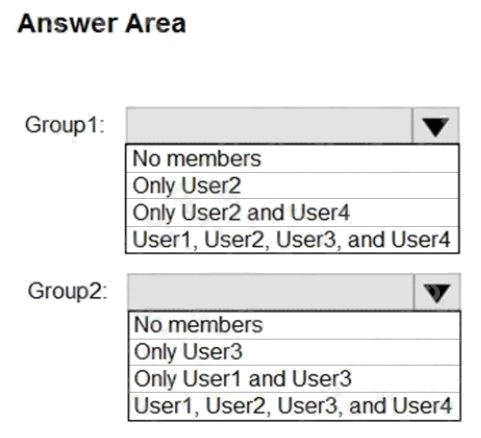
Answer:

Explanation:
Box 1: User1, User2, User3, User4
Contains "ON" is true for Montreal (User1), MONTREAL (User2), London (User 3), and Ontario (User4) as string and regex
operations are not case sensitive.
Box 2: Only User3
Match "*on" is only true for London (User3) as London is the only word that ends with on.
Scenario:
Contoso.com contains the users shown in the following table.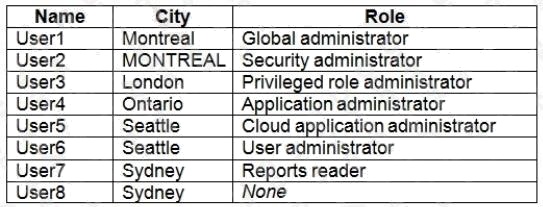
Contoso.com contains the security groups shown in the following table.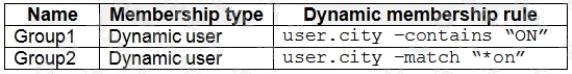
References:
https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/groups-dynamic-membership
Comments
Question 4 Topic 5, Case Study 5Case Study Question View Case
HOTSPOT
You are evaluating the security of the network communication between the virtual machines in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: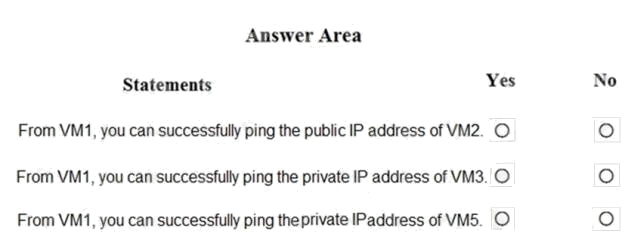
Answer:
Explanation:
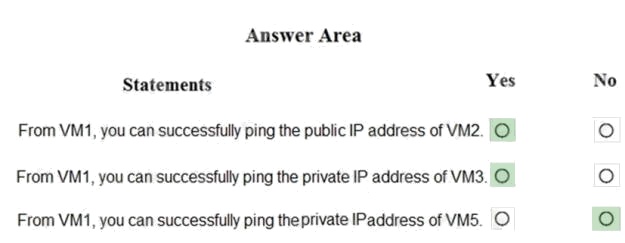
Box 1: Yes. All traffic is allowed out to the Internet so you can ping the public IP.
NSG1, NSG2, NSG3, and NSG4 have the outbound security rules shown in the following table.
Box 2: Yes. VM3 is on Subnet12. There is no NSG attached to Subnet12 so the traffic will be allowed by default.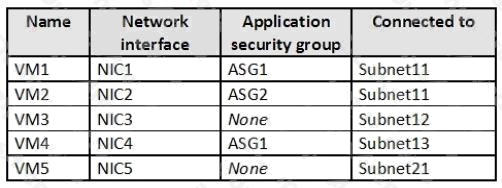
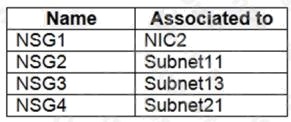
Box 3: No (because VM5 is in a separate VNet).
Note: Sub2 contains the virtual machines shown in the following table.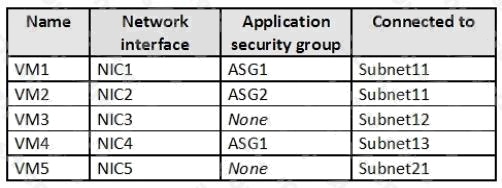
Comments
Question 5 Topic 5, Case Study 5Case Study Question View Case
HOTSPOT
You are evaluating the effect of the application security groups on the network communication between the virtual machines
in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: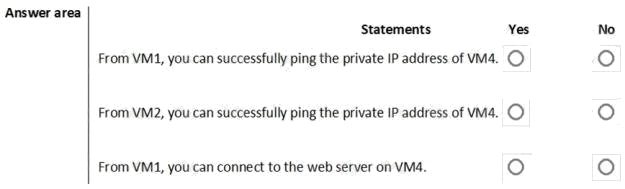
Answer:
Explanation:
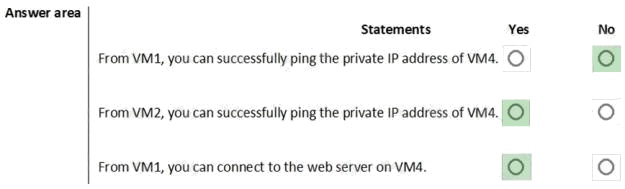
Box 1: No. VM4 is in Subnet13 which has NSG3 attached to it.
VM1 is in ASG1. NSG3 would only allow ICMP pings from ASG2 but not ASG1. Only TCP traffic is allowed from ASG1.
NSG3 has the inbound security rules shown in the following table.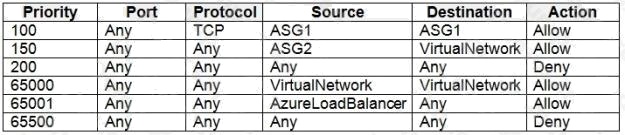
Box 2: Yes.
VM2 is in ASG2. Any protocol is allowed from ASG2 so ICMP ping would be allowed.
Box3. VM1 is in ASG1. TCP traffic is allowed from ASG1 so VM1 could connect to the web server as connections to the web
server would be on ports TCP 80 or TCP 443.
Comments
Question 6 Topic 5, Case Study 5Case Study Question View Case
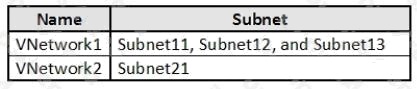
You need to meet the technical requirements for VNetwork1.
What should you do first?
- A. Create a new subnet on VNetwork1.
- B. Remove the NSGs from Subnet11 and Subnet13.
- C. Associate an NSG to Subnet12.
- D. Configure DDoS protection for VNetwork1.
Answer:
A
Explanation:
From scenario: Deploy Azure Firewall to VNetwork1 in Sub2.
Azure firewall needs a dedicated subnet named AzureFirewallSubnet.
References:
https://docs.microsoft.com/en-us/azure/firewall/tutorial-firewall-deploy-portal
Comments
Question 7 Topic 5, Case Study 5Case Study Question View Case
HOTSPOT
You are evaluating the security of VM1, VM2, and VM3 in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: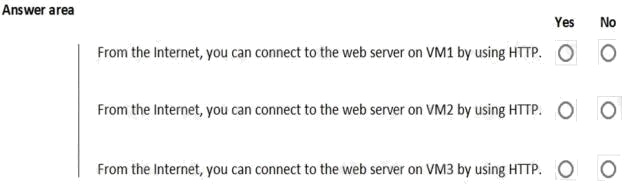
Answer:
Explanation:
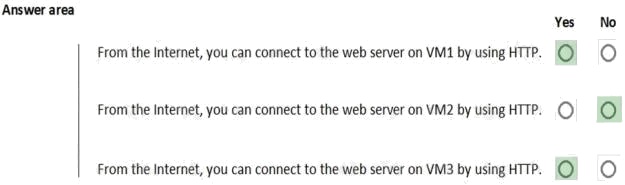
VM1: Yes. NSG2 applies to VM1 and this allows inbound traffic on port 80.
VM2: No. NSG2 and NSG1 apply to VM2. NSG2 allows the inbound traffic on port 80 but NSG1 does not allow it.
VM3: Yes. There are no NSGs applying to VM3 so all ports will be open.
Implement platform protection
Comments
Question 8 Topic 6, Case Study 6Case Study Question View Case
HOTSPOT
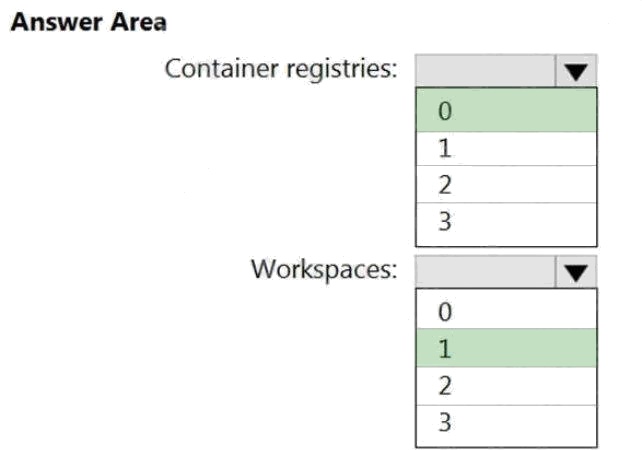
You need to configure support for Azure Sentinel notebooks to meet the technical requirements.
What is the minimum number of Azure container registries and Azure Machine Learning workspaces required?
Hot Area: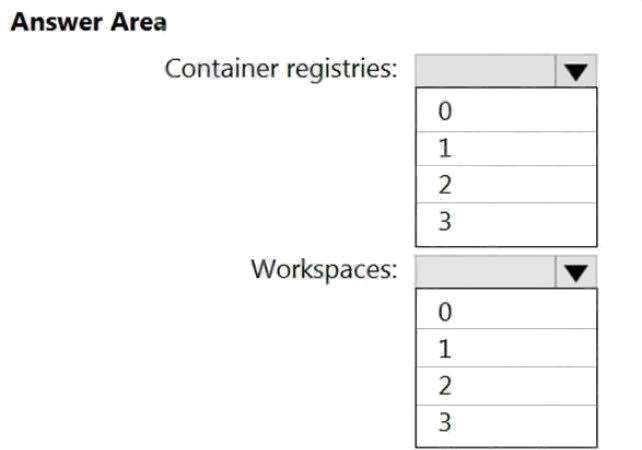
Answer:
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/notebooks
Comments
Question 9 Topic 6, Case Study 6Case Study Question View Case
From Azure Security Center, you need to deploy SecPol1.
What should you do first?
- A. Enable Azure Defender.
- B. Create an Azure Management group.
- C. Create an initiative.
- D. Configure continuous export.
Answer:
C
Explanation:
Reference:
https://github.com/MicrosoftDocs/azure-docs/blob/master/articles/security-center/custom-security-policies.md
https://zimmergren.net/create-custom-security-center-recommendation-with-azure-policy/
Comments
Question 10 Topic 7, Case Study 7Case Study Question View Case
HOTSPOT
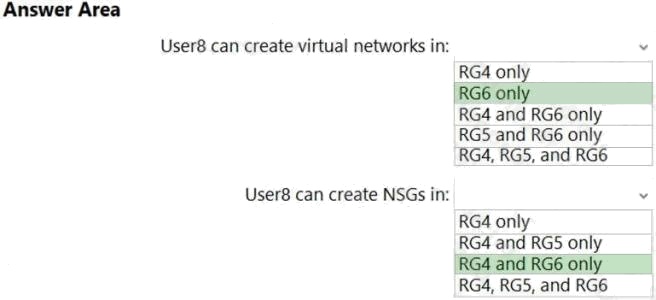
You assign User8 the Owner role for RG4, RG5, and RG6.
In which resource groups can User8 create virtual networks and NSGs? You must be able to connect virtual machines to
deployed virtual networks. To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
Explanation:
Box 1: RG6 only
The policy does not allow the creation of virtual networks/subnets in RG5. Only NSGs can be created in RG4.
Box 2: The policy does not allow the creation of NSGs in RG5.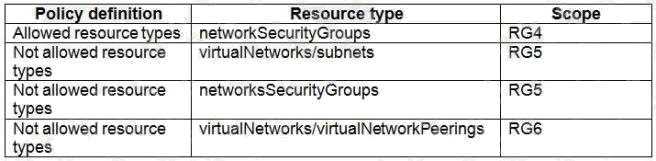
Reference: https://docs.microsoft.com/en-us/azure/governance/policy/overview
Comments
Page 1 out of 33
Viewing questions 1-10 out of 336
page 2