microsoft az-220 practice test
Microsoft Azure IoT Developer
Note: Test Case questions are at the end of the exam
Last exam update: Jul 20 ,2024
Question 1 Topic 4, Mixed Questions
You have an Azure IoT hub that has a hostname of contoso-hub.azure-devices.net and an MCU-based IoT device named
Device1. Device1 does NOT support Azure IoT SDKs.
You plan to connect Device1 to the IoT hub by using the Message Queuing Telemetry Transport (MQTT) protocol and to
authenticate by using X.509 certificates.
You need to ensure that Device1 can authenticate to the IoT hub.
What should you do?
- A. Create an Azure key vault and enable the encryption of data at rest for the IoT hub by using a customer-managed key.
- B. Enable a hardware security module (HSM) on Device1.
- C. From the Azure portal, create an IoT Hub Device Provisioning Service (DPS) instance and add a certificate enrollment for Device1.
- D. Add the DigiCert Baltimore Root Certificate to Device1.
Answer:
D
Explanation:
The connection to Azure IoT Hub with MQTT is secured using TLS.
The Azure IoT Hub library requires the provisioning of the following certificates and a private key for a successful TLS
connection:
1. Baltimore CyberTrust Root certificate - Server certificate, used to verify the servers certificate while connecting.
2. Device certificate - generated by the procedures described in Creating Azure IoT Hub certificates , used by Azure IoT Hub
to authenticate the device.
3. Private key of the device. Reference:
https://developer.nordicsemi.com/nRF_Connect_SDK/doc/latest/nrf/include/net/azure_iot_hub.html
Question 2 Topic 4, Mixed Questions
DRAG DROP
You have an Azure IoT Edge solution.
You plan to deploy an Azure Security Center for IoT security agent. You need to configure the security agent to meet the
following requirements:
Connection events must be reported as high priority.
High priority events must be collected every seven minutes.
How should you configure the azureiotsecurity module twin? To answer, drag the appropriate values to the correct locations.
Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to
view content.
NOTE: Each correct selection is worth one point.
Select and Place: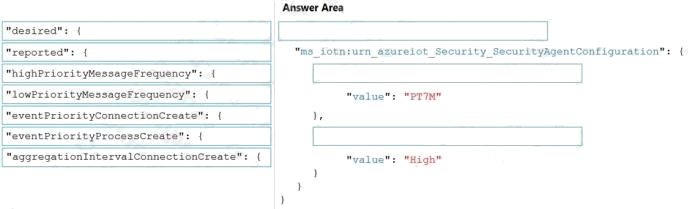
Answer:
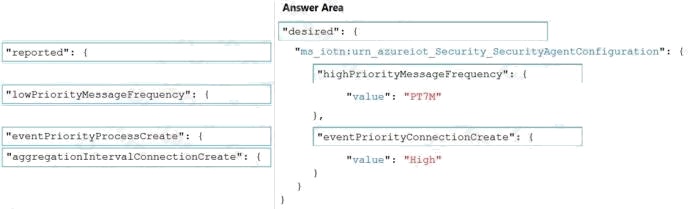
Explanation:
Box 1: "desired": {
To configure connection events as high priority and collect high priority events every 7 minutes, use the following
configuration.
"desired": {
"ms_iotn:urn_azureiot_Security_SecurityAgentConfiguration": {
"highPriorityMessageFrequency": {
"value": "PT7M"
},
"eventPriorityConnectionCreate": {
"value": "High"
}
Box 2: "highPriorityMessageFrequency ": {
Box 3: "eventPriorityConnectionCreate": {
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-iot/how-to-agent-configuration
Question 3 Topic 4, Mixed Questions
From the Device Provisioning Service, you create an enrollment as shown in the exhibit.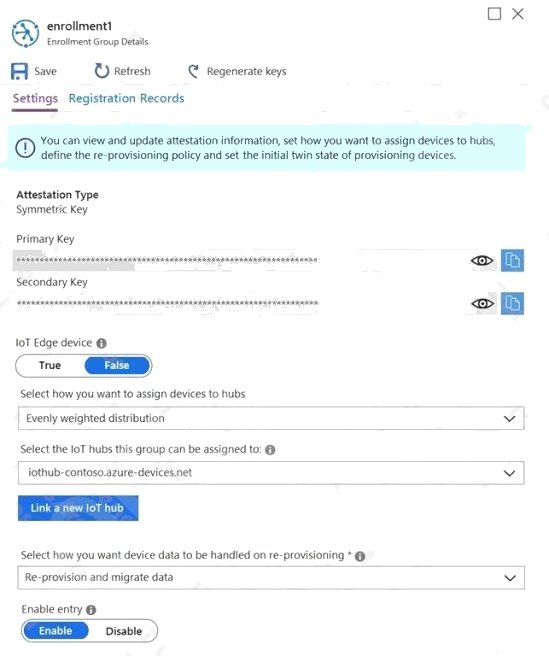
You need to deploy a new IoT device.
What should you use as the device identity during attestation?
- A. a self-signed X.509 certificate
- B. the random string of alphanumeric characters
- C. the HMAC-SHA256 hash of the device's registration ID
- D. the endorsement key of the device's Trusted Platform Module (TPM)
Answer:
C
Explanation:
Each device uses its derived device key with your unique registration ID to perform symmetric key attestation with the
enrollment during provisioning. To generate the device key, use the key you copied from your DPS enrollment to compute an
HMAC-SHA256 of the unique registration ID for the device and convert the result into Base64 format. Reference:
https://docs.microsoft.com/en-us/azure/iot-edge/how-to-auto-provision-symmetric-keys
Question 4 Topic 4, Mixed Questions
You have an Azure IoT hub that uses a Device Provisioning Service instance.
You have 1,000 legacy IoT devices that only support MAC address or serial number identities. The devices do NOT have a
security feature that can be used to securely identify the device or a hardware security module (HSM).
You plan to deploy the devices to a secure environment.
You need to configure the Device Provisioning Service instance to ensure that all the devices are identified securely before
they receive updates.
Which attestation mechanism should you choose?
- A. Trusted Platform Module (TPM) 1.2 attestation
- B. symmetric key attestation
- C. X.509 certificates
Answer:
B
Explanation:
A common problem with many legacy devices is that they often have an identity that is composed of a single piece of
information. This identity information is usually a MAC address or a serial number. Legacy devices may not have a
certificate, TPM, or any other security feature that can be used to securely identify the device. The Device Provisioning
Service for IoT hub includes symmetric key attestation. Symmetric key attestation can be used to identify a device based off
information like the MAC address or a serial number. Reference:
https://docs.microsoft.com/bs-latn-ba/azure/iot-dps/how-to-legacy-device-symm-key
Question 5 Topic 4, Mixed Questions
You use Azure Security Center in an Azure IoT solution.
You need to exclude some security events. The solution must minimize development effort.
What should you do?
- A. Create an Azure function to filter security messages.
- B. Add a configuration to the code of the physical IoT device.
- C. Add configuration details to the device twin object.
- D. Create an azureiotsecurity module twin and add configuration details to the module twin object.
Answer:
D
Explanation:
Properties related to every Azure Security Center for IoT security agent are located in the agent configuration object, within
the desired properties section, of the azureiotsecurity module.
To modify the configuration, create and modify this object inside the azureiotsecurity module twin identity.
Note: Azure Security Center for IoT's security agent twin configuration object is a JSON format object. The configuration
object is a set of controllable properties that you can define to control the behavior of the agent.
These configurations help you customize the agent for each scenario required. For example, automatically excluding some
events, or keeping power consumption to a minimal level are possible by configuring these properties. Reference:
https://docs.microsoft.com/en-us/azure/asc-for-iot/how-to-agent-configuration
Question 6 Topic 4, Mixed Questions
DRAG DROP
You have an Azure IoT hub named Hub1 and a root certification authority (CA) named CA1. Hub1 is configured to use X.509
certificate device authentication.
You and a custom manufacturing partner complete a proof of possession flow.
You plan to deploy IoT devices manufactured by the custom manufacturing partner. Each device will have a certificate
generated by an intermediate CA. The devices will authenticate by using device certificates signed by the partner.
You need to ensure that the custom devices can connect successfully to Hub1.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the
answer area and arrange them in the correct order.
Select and Place: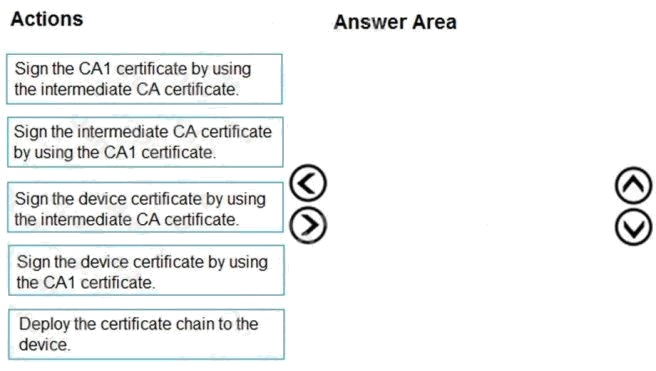
Answer:
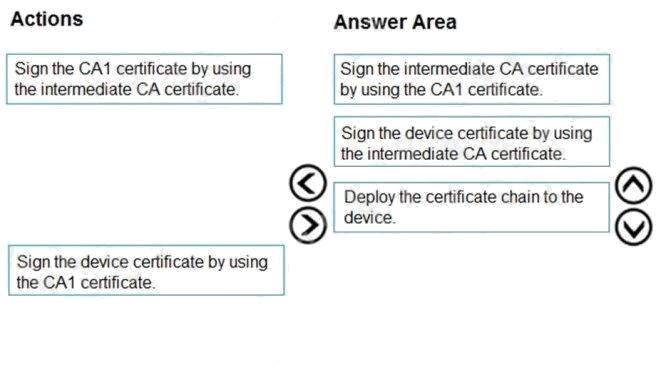
Explanation:
Box 1: Sign the intermediate CA certificate by using the CA1 certificate.
X.509 certificates are typically arranged in a certificate chain of trust in which each certificate in the chain is signed by the
private key of the next higher certificate, and so on, terminating in a self-signed root certificate. This arrangement establishes
a delegated chain of trust from the root certificate generated by a trusted root certificate authority (CA) down through each
intermediate CA to the end-entity "leaf" certificate installed on a device.
Box 2: Sign the device certificate by using the intermediate CA
An intermediate certificate is an X.509 certificate, which has been signed by the root certificate (or by another intermediate
certificate with the root certificate in its chain). The last intermediate certificate in a chain is used to sign the leaf certificate.
An intermediate certificate can also be referred to as an intermediate CA certificate.
Box 3: Deploy the certificate chain to the device.
The leaf certificate, or end-entity certificate, identifies the certificate holder. It has the root certificate in its certificate chain as
well as zero or more intermediate certificates. The leaf certificate is not used to sign any other certificates. It uniquely
identifies the device to the provisioning service and is sometimes referred to as the device certificate. During authentication,
the device uses the private key associated with this certificate to respond to a proof of possession challenge from the
service.
Reference:
https://docs.microsoft.com/en-us/azure/iot-dps/concepts-x509-attestation
Question 7 Topic 4, Mixed Questions
You have an Azure IoT solution that contains an Azure IoT hub and 100 IoT devices. The devices run Windows Server 2016.
You need to deploy the Azure Defender for IoT C#-based security agent to the devices.
What should you do first?
- A. On the devices, initialize Trusted Platform Module (TPM).
- B. From the IoT hub, create a system-assigned managed identity.
- C. From the IoT hub, create a security module for the devices.
- D. On the devices, set the PowerShell execution policy to Restricted.
Answer:
C
Explanation:
The IoT Edge security manager provides a safe framework for security service extensions through host-level modules. The
IoT Edge security manager include Ensure safe operation of client agents for services including Device Update for IoT
Hub and Azure Defender for IoT. Reference:
https://docs.microsoft.com/en-us/azure/iot-edge/iot-edge-security-manager
Question 8 Topic 4, Mixed Questions
You have an Azure subscription that contains an Azure IoT hub and two Azure IoT Edge devices named Device1 and
Device2.
You need to ensure that the IoT hub only accepts connections from Device1 and Device2.
What should you configure?
- A. a private endpoint connection
- B. Azure API Management
- C. Azure Active Directory (Azure AD) Identity Protection
- D. a gateway device
Answer:
A
Explanation:
Ingress connectivity to IoT Hub using Azure Private Link.
A private endpoint is a private IP address allocated inside a customer-owned VNet via which an Azure resource is reachable.
Through Azure Private Link, you can set up a private endpoint for your IoT hub to allow services inside your VNet to reach
IoT Hub without requiring traffic to be sent to IoT Hub's public endpoint. Similarly, your on-premises devices can use Virtual
Private Network (VPN) or ExpressRoute peering to gain connectivity to your VNet and your IoT Hub (via its private endpoint).
As a result, you can restrict or completely block off connectivity to your IoT hub's public endpoints by using IoT Hub IP filter
or the public network access toggle. This approach keeps connectivity to your Hub using the private endpoint for devices.
Reference:
https://docs.microsoft.com/en-us/azure/iot-hub/virtual-network-support
Question 9 Topic 4, Mixed Questions
You have an Azure IoT hub.
You need to enable Azure Defender for IoT on the IoT hub.
What should you do?
- A. From the Security settings of the IoT hub, select Secure your IoT solution.
- B. From the Diagnostics settings of the IoT hub, select Add diagnostic setting.
- C. From Defender, add a security policy.
- D. From Defender, configure security alerts.
Answer:
A
Explanation:
You can onboard Defender for IoT to an existing IoT Hub, where you can then monitor the device identity management,
device to cloud, and cloud to device communication patterns.
To onboard Defender for IoT to an existing IoT Hub:
1. Navigate to the IoT Hub.
2. Select the IoT Hub to be onboarded.
3. Select any option under the Security section.
4. ClickSecure your IoT solutionand complete the onboarding form.
The Secure your IoT solution button will only appear if the IoT Hub has not already been onboarded, or if while onboarding
you left the Defender for IoT toggle on Off.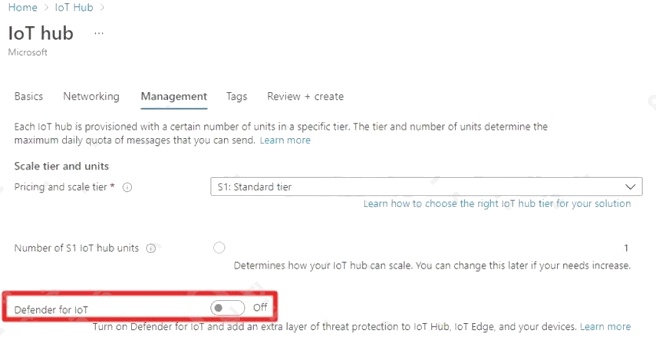
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-iot/device-builders/quickstart-onboard-iot-hub
Question 10 Topic 4, Mixed Questions
DRAG DROP
You have an Azure IoT solution that includes an Azure IoT hub.
You receive a root certification authority (CA) certificate from the security department at your company.
You need to configure the IoT hub to use the root CA certificate.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the
answer area and arrange them in the correct order.
Select and Place:
Answer:
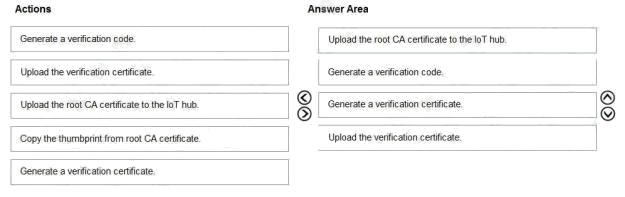
Explanation:
Reference: https://docs.microsoft.com/bs-latn-ba/azure/iot-hub/iot-hub-security-x509-get-started
Question 11 Topic 4, Mixed Questions
You have an Azure IoT solution that contains an Azure IoT hub.
You need to ensure that the IoT hub configuration is compliant with the Health Insurance Portability and Accountability Act
(HIPAA) audit logging requirements.
What should you use?
- A. Azure Advisor recommendations
- B. an Azure Policy definition
- C. Azure Monitor alerts
- D. an Azure Sentinel workspace
Answer:
B
Explanation:
Regulatory Compliance in Azure Policy provides Microsoft created and managed initiative definitions, known as built-ins, for
the compliance domains and security controls related to different compliance standards, including HIPAA auditing logging.
Reference:
https://docs.microsoft.com/en-us/azure/iot-hub/security-controls-policy
Question 12 Topic 4, Mixed Questions
You have an Azure IoT hub and 15,000 IoT devices that monitor temperature. The IoT hub has four partitions. Each IoT
device sends a 1-KB message every five seconds.
You plan to use Azure Stream Analytics to process the telemetry stream and generate an alert when temperatures exceed a
defined threshold.
You need to recommend the minimum number of streaming units to configure for Stream Analytics.
What should you recommend?
- A. 1
- B. 3
- C. 6
- D. 12
Answer:
D
Explanation:
15000/5 = 3K/s -> 3 Streaming Units (SU). 3 SU x 4 partitions -> 12 SU For reference: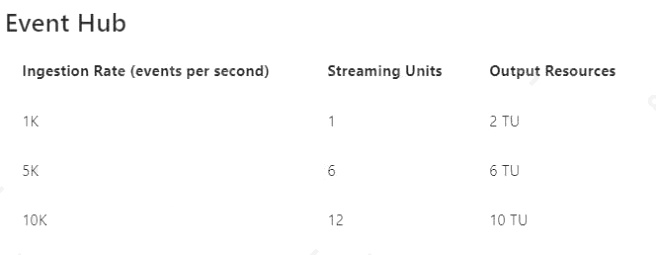
Reference:
https://docs.microsoft.com/en-us/azure/stream-analytics/stream-analytics-parallelization#calculate-the-maximum-streaming-
units-of-a-job
Question 13 Topic 4, Mixed Questions
You have an Azure IoT solution.
You need to test that the solution remains functional if IoT Hub is affected by a regional outage.
What should you do?
- A. From the IoT hub, set Allow public network access to Disabled.
- B. From the IoT hub, start a manual failover.
- C. From the Device Provisioning Service (DPS), unlink the IoT hub.
- D. From the IoT hub, select Disable fallback route.
Answer:
B
Explanation:
Manual failover is a feature of the IoT Hub service that allows customers to failover their hub's operations from a primary
region to the corresponding Azure geo-paired region. Manual failover can be done in the event of a regional disaster or an
extended service outage. You can also perform a planned failover to test your disaster recovery capabilities, although we
recommend using a test IoT hub rather than one running in production. Reference:
https://docs.microsoft.com/en-us/azure/iot-hub/tutorial-manual-failover
Question 14 Topic 4, Mixed Questions
You have an Azure IoT hub.
You need to check whether the IoT hub was affected by an outage.
What should you select in the Azure portal? To answer, select the appropriate option in the answer area.
NOTE: Each correct selection is worth one point.
- A. Resource health
- B. Metrics
- C. Alerts
- D. Diagnostic settings
Answer:
A
Explanation:
Azure Service Health service helps you monitor service-level events like outages.
You can check the health status of your IoT hub directly from the portal.
To see status and status history of your IoT hub using the portal, follow these steps:
1. In Azure portal, go to your IoT hub in Azure portal.
2. On the left pane, under Support + troubleshooting, select Resource Health.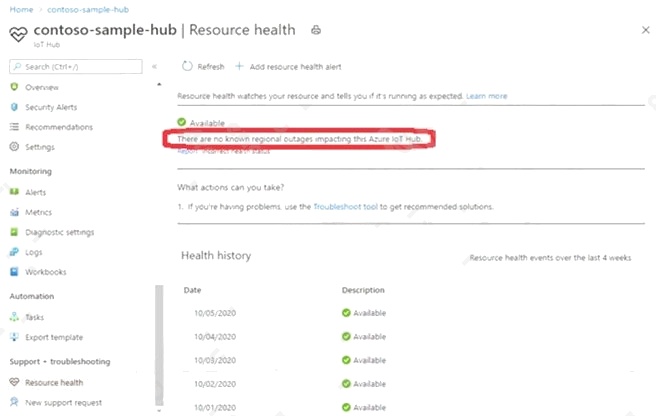
Reference:
https://docs.microsoft.com/en-us/azure/iot-hub/iot-hub-azure-service-health-integration
Question 15 Topic 4, Mixed Questions
DRAG DROP
You are troubleshooting device connections to and disconnections from an Azure IoT hub.
You configure diagnostic logging for the IoT hub to send to Log Analytics.
You need to generate a report that displays the device connection and disconnection events.
How should you complete the query? To answer, drag the appropriate values to the correct targets. Each value may be used
once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: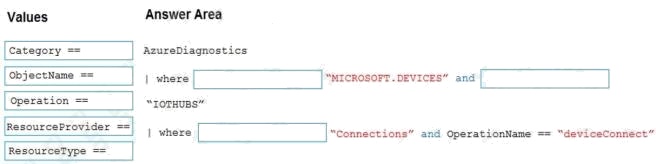
Answer:
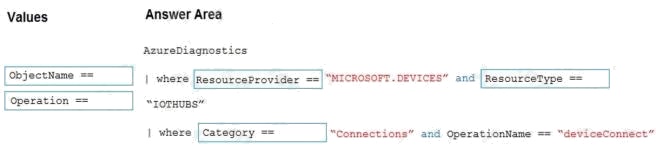
Explanation:
Box 1: ResourceProvider ==
Query to monitor your IoT hub connectivity Errors: Identify device connection errors.
AzureDiagnostics
| where ResourceProvider == "MICROSOFT.DEVICES" and ResourceType == "IOTHUBS"
| where Category == "Connections" and Level == "Error"
Box 2: ResourceType ==
Box 3: Category ==
Reference: https://docs.microsoft.com/en-us/azure/iot-hub/monitor-iot-hub