Question 1
The president of your university asks you to set up a service website for students who live in dorms. The websites official
launch date is in two days, and you do not have the resources needed to set up the server infrastructure and develop the
system.
You need a cloud-based solution than can have the servers and storage available in two days. Which Microsoft cloud
solution achieves this goal?
- A. Microsoft Intune
- B. Microsoft Azure
- C. Achieve Directory
- D. Microsoft OneDrive
Answer:
B
Explanation:
Microsoft Azure is a cloud computing platform and infrastructure, created by Microsoft, for building, deploying and managing
applications and services through a global network of Microsoftmanaged datacenters.
Microsoft Azure services include: Websites: High density hosting of websites.
Reference: http://en.wikipedia.org/wiki/Microsoft_Azure#Services
Comments
Question 2
Which feature on Windows Phone 8.1 provides secure encryption of all user data stored locally on internal data partitions?
- A. Secure Boot
- B. Encrypted File System
- C. BitLocker
- D. TrueCrypt
Answer:
C
Explanation:
The Windows Phone OS supports using BitLocker technology to encrypt all user data stored locally on internal data
partitions.
Reference: Secure boot and device encryption overview https://dev.windowsphone.com/en-US/OEM/docs/Phone_Bring-Up/
Secure_boot_and_device_encryption_overview
Comments
Question 3
You are tracking hardware and software inventory on various devices.
You need to determine which devices can be managed by Microsoft Intune.
To communicate back to Microsoft Intune administration console, what is a requirement of each device?
- A. Microsoft Intune agent installed
- B. Windows Phone 8 devices
- C. an organizational unit that has all the Microsoft Intune device objects
- D. a security policy
Answer:
A
Explanation:
The devices need the Microsoft Intune client installed. This software is also known as Microsoft Intune agent.
Comments
Question 4
Which type of information about users does biometrics evaluate?
- A. phrases a user has memorized
- B. where a user is located
- C. physical characteristics of a user
- D. objects a user carries with him or her
Answer:
C
Explanation:
Biometrics refers to authentication techniques that rely on measurable physical characteristics that can be automatically
checked.
Note: There are several types of biometric identification schemes: face: the analysis of facial characteristics
fingerprint: the analysis of an individual's unique fingerprints
hand geometry: the analysis of the shape of the hand and the length of the fingers retina: the analysis of the capillary
vessels located at the back of the eye iris: the analysis of the colored ring that surrounds the eye's pupil signature: the
analysis of the way a person signs his name. vein: the analysis of pattern of veins in the back if the hand and the wrist voice:
the analysis of the tone, pitch, cadence and frequency of a person's voice.
Reference: http://www.webopedia.com/TERM/B/biometrics.html
Comments
Question 5
Your network is configured as an Active Directory Domain Services (AD DS) domain. The company has an Azure AD
premium subscription. You need to configure file access and storage to meet the following requirements:
Users can access files from any location with any managed devices without connecting to the corporate network.
Users can access local copies of files when they are not connected to the Internet. Files will sync automatically when

connected to the Internet.
What should you configure?
- A. Work Folders
- B. Offline folders
- C. Company Portal
- D. RemoteApp
Answer:
A
Explanation:
References: https://docs.microsoft.com/en-us/windows-server/storage/work-folders/work-folders-overview
Comments
Question 6
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: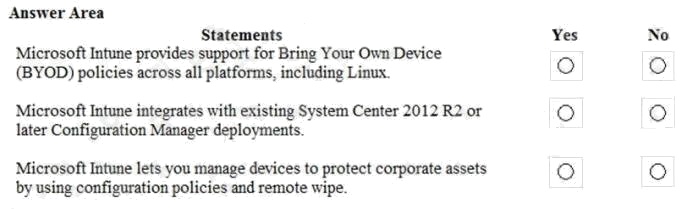
Answer:
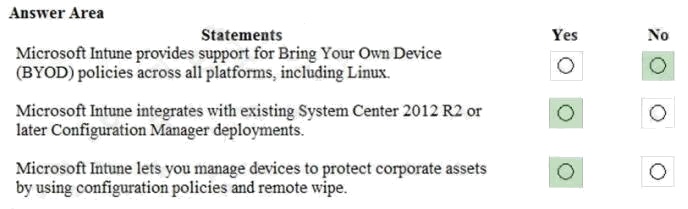
Comments
Question 7
Which two Windows 10 tools can be used to perform BitLocker encryption? (Choose two.)
- A. Manage-bde
- B. Disk Management
- C. Microsoft Management Console
- D. BitLocker control panel
Answer:
A D
Explanation:
References:
https://docs.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-basicdeployment
http://www.ilovefreesoftware.com/12/windows-10/enable-bitlocker-drive-encryption-windows10.html
Comments
Question 8
DRAG DROP
Match each type of malware to its definition.
To answer, drag the appropriate malware type from the column on the left to the definition on the right. Each malware type
may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
Answer:

Explanation:
References: https://www.malwarefox.com/malware-types/#tab-con-6
Comments
Question 9
DRAG DROP
Match each Microsoft Virtual desktop feature to its definition.
Instructions: To answer, drag the appropriate feature from the column of the left to its definition on the right. Each feature
may be used once, more than once, or not at all. Each correct match is worth one point.
Select and Place: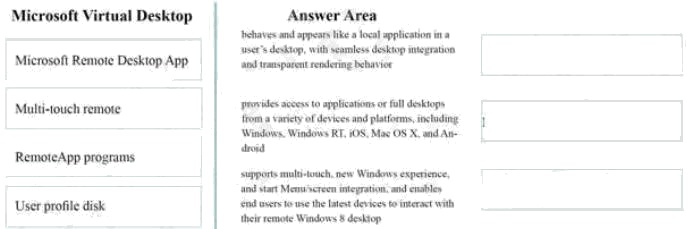
Answer:
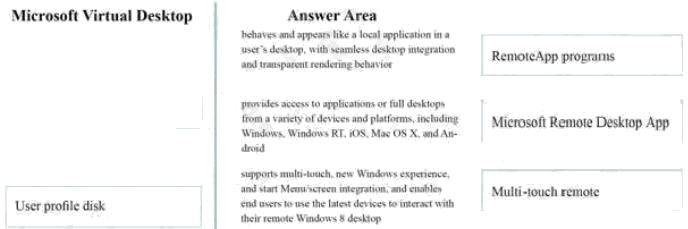
Explanation:
* RemoteApp programs
RemoteApp enables you to make programs that are accessed remotely through Remote Desktop Services appear as if they
are running on the end user's local computer. These programs are referred to as RemoteApp programs. Instead of being
presented to the user in the desktop of the Remote Desktop Session Host (RD Session Host) server, the RemoteApp
program is integrated with the client's desktop.
* Microsoft Remote Desktop App
Provides access to applications or full desktops from a variety of devices and platforms including Windows, Windows RT,
iOS, Mac OS X and Android
* Multi-touch remote
Supports multi-touch, new Windows experience, and Start menu/screen integration. Enables end users to use the latest
devices to interact with their remote Windows 8 desktops. The touch experience is fully remote, supporting Windows 8 touch
gestures such as pinch, zoom and rotate.
Reference: Microsoft Virtual Desktop Infrastructure, Rich user experience at a great value
http://download.misco.co.uk/misco/uk/pdf/Microsoft-Virtual-Desktop-Infrastructure.pdf Reference: Overview of RemoteApp
https://technet.microsoft.com/en-us/library/cc755055.aspx
Comments
Question 10
This question requires that you evaluate the underlined text to determine if it is correct. When BitLocker is enabled and and
protecting a local drive, Trusted Platform Module (TPM) provides "pre-start system integrity verification for system and
operating system drives". Instructions: Review the underlined text. If it makes the statement correct, select No change is
needed. If the statement is incorrect, select the answer choice than makes the statement correct.
- A. No change is needed
- B. 256-bit encryption that uses Advanced Encryption Standard (AES)
- C. a location that stores recovery keys for removable drives
- D. boot sector mapping for the startup process
Answer:
C
Explanation:
Computers that incorporate a TPM have the ability to create cryptographic keys and encrypt them so that they can be
decrypted only by the TPM. This process, often called "wrapping" or "binding" a key, can help protect the key from
disclosure. Each TPM has a root "wrapping" key, called the Storage Root Key (SRK), which is stored within the TPM itself.
The private portion of a key created in a TPM is never exposed to any other component, software, process, or person.
Reference: Windows Trusted Platform Module Management Step-by-Step Guide https://technet.microsoft.com/en-
us/library/cc749022%28v=ws.10%29.aspx
Comments
Page 1 out of 6
Viewing questions 1-10 out of 66
page 2