microsoft 98-367 practice test
Security fundamentals
Last exam update: Jun 27 ,2025
Question 1
Your password is 1Vu*cI!8sT.
Which attack method is your password vulnerable to?
- A. Rainbow table
- B. Brute force
- C. Spidering
- D. Dictionary
Answer:
A
Question 2
Shredding documents helps prevent:
- A. Man-in-the-middle attacks
- B. Social engineering
- C. File corruption
- D. Remote code execution
- E. Social networking
Answer:
B
Explanation:
Reference: http://technet.microsoft.com/en-us/library/cc875841.aspx
Question 3
Malicious software designed to collect personally identifiable information is referred to as :
- A. spyware
- B. a cookie
- C. a network sniffer
- D. freeware
Answer:
A
Question 4
The name of a particular wireless LAN that is broadcast on a network is referred to as a:
- A. MAC address
- B. Basis Service Set (BSS)
- C. Wireless Access Point (WAP)
- D. Service Set Identifier (SSID)
Answer:
D
Question 5
HOTSPOT You are at school and logged in to a Windows 7 computer using a standard user account.
You need to change some of the properties of a desktop icon for an assignment. Your instructor provides you with an
administrator username and password and asks you to do two tasks.
When you open the Need Admin Access Properties window, you see the following image: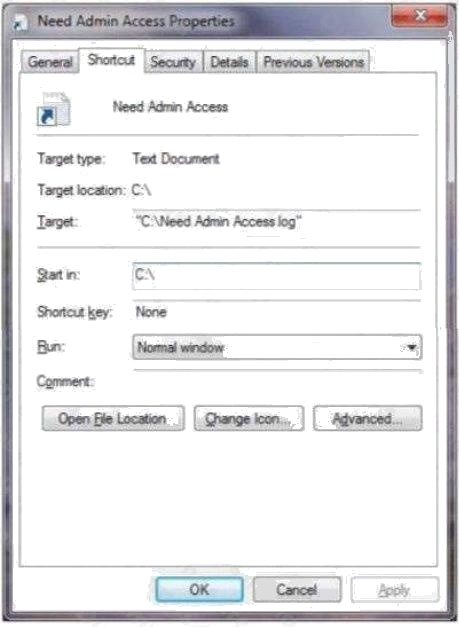
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one
point.
Hot Area: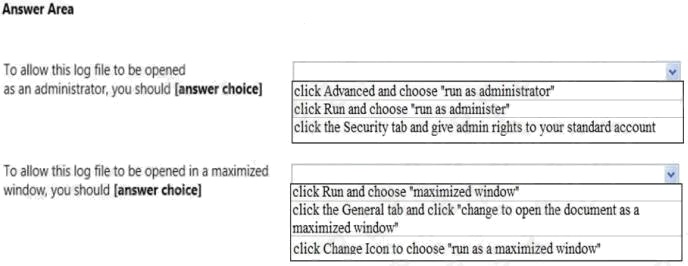
Answer:
Question 6
Which enables you to change the permissions on a folder?
- A. Take ownership
- B. Extended attributes
- C. Auditing
- D. Modify
Answer:
D
Question 7
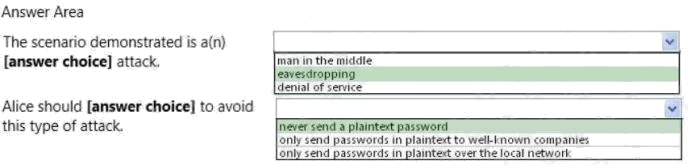
HOTSPOT
Alice sends her password to the game server in plaintext. Chuck is able to observe her password as shown in the following
image: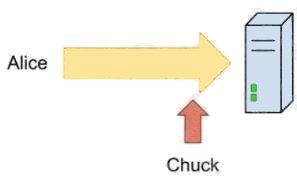
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one
point.
Hot Area: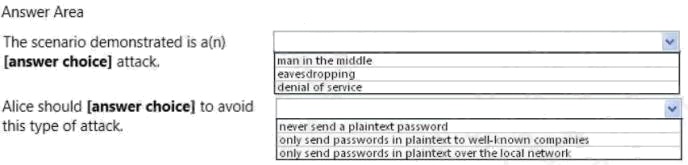
Answer:
Question 8
Password history policies are used to prevent:
- A. Brute force attacks
- B. Users from sharing passwords
- C. Social engineering
- D. Passwords from being reused immediately
Answer:
D
Explanation:
This security setting determines the number of unique new passwords that have to be associated with a user account before
an old password can be reused. The value must be between 0 and 24 passwords.
This policy enables administrators to enhance security by ensuring that old passwords are not reused continually.
Reference: http://technet.microsoft.com/en-us/library/cc758950(v=ws.10).aspx
Question 9
The reason for implementing Service Set IDentifier (SSID) masking is to:
- A. enforce a more secure password policy
- B. hide a wireless network name from unknown computers
- C. hide a network share from unauthorized users
- D. disable autologon
Answer:
B
Question 10
You are an intern at Wide World Importers and help manage 1000 workstations. All the workstations are members of an
Active Domain.
You need to push out an internal certificate to Internet Explorer on all workstations.
What is the quickest method to do this?
- A. Local policy
- B. Logon script
- C. Windows Update
- D. Group policy
Answer:
A
Question 11
What is an example of non-propagating malicious code?
- A. A back door
- B. A hoax
- C. A Trojan horse
- D. A worm
Answer:
A
Question 12
HOTSPOT
You are configuring the network settings of computers in your schools computer lab.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: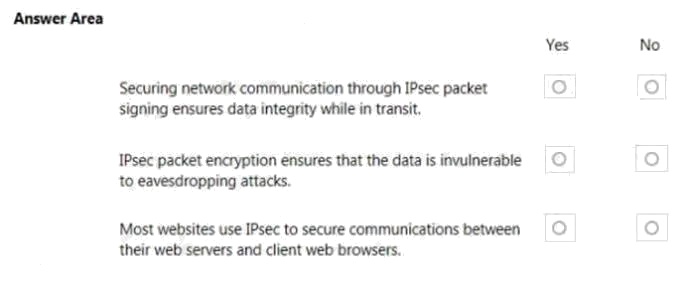
Answer:
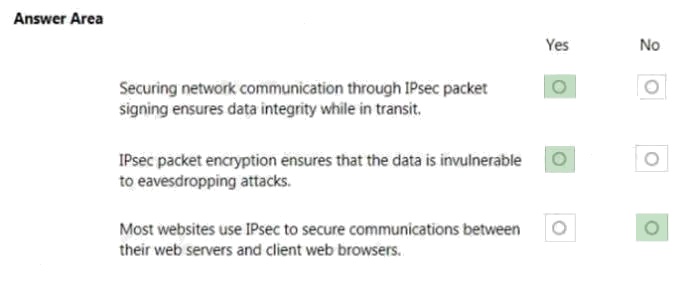
Explanation:
Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts the packets of data sent
over an Internet Protocol network.
References:
https://en.wikipedia.org/wiki/IPsec
Question 13
What are two examples of physical site security? (Choose two.)
- A. keeping machines in locked offices
- B. sending backups to a remote location
- C. enforcing multi-factor authentication
- D. using BitLocker encryption on drives
Answer:
A B
Question 14
You want to prevent external users from acquiring information about your network. You should implement a:
- A. router
- B. layer-3 switch
- C. firewall
- D. proxy server
Answer:
C
Question 15
You manage 50 Windows workstations in a computer lab. All workstations belong to the lab Active Directory domain.
You need to implement several audit policies on each workstation in the shortest time possible.
What should you do?
- A. Enable logging on each computer
- B. Create a domain Group Policy
- C. Turn on the Audit Policy on the domain controller
- D. Enable Audit object access
Answer:
B
Explanation:
References: https://docs.microsoft.com/en-us/windows-server/networking/branchcache/deploy/use-grouppolicy-to-configure-
domain-member-client-computers