Question 1
The certificate of a secure public Web server on the Internet should be:
- A. Issued by a public certificate authority (CA)
- B. Signed by using a 4096-bit key
- C. Signed by using a 1024-bit key
- D. Issued by an enterprise certificate authority (CA)
Answer:
A
Comments
Question 2
A user who receives a large number of emails selling prescription medicine is probably receiving pharming mail.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the
underlined text makes the statement correct.
- A. Malware
- B. Spoofed mail
- C. Spam
- D. No change is needed.
Answer:
C
Comments
Question 3
The WPA2 PreShared Key (PSK) is created by using a passphrase (password) and salting it with the WPS PIN.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the
underlined text makes the statement correct.
- A. Service Set Identifier (SSID)
- B. Admin password
- C. WEP key
- D. No change is needed
Answer:
A
Comments
Question 4
You have an application that uses IPsec to secure communications between an Internet client and a server on the internal
network.
To which network security service must the IPsec client connect?
- A. SFTP
- B. SSH
- C. VPN
- D. RADIUS
Answer:
C
Comments
Question 5
Media Access Control (MAC) filtering enables you to:
- A. limit access to a network based on the client computer’s network adapter.
- B. set access permissions to a shared folder.
- C. prevent communications between specific IP addresses.
- D. restrict communications to a specific website.
Answer:
A
Comments
Question 6
DRAG DROP
Certain potentially harmful file types should be filtered as attachments of incoming email messages.
Match the file extension that should be filtered with its description.
Instructions: To answer, drag the appropriate file extension from the column on the left to its description on the right. Each
file extension may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to
view content.
Note: For each correct selection is worth one point.
Select and Place: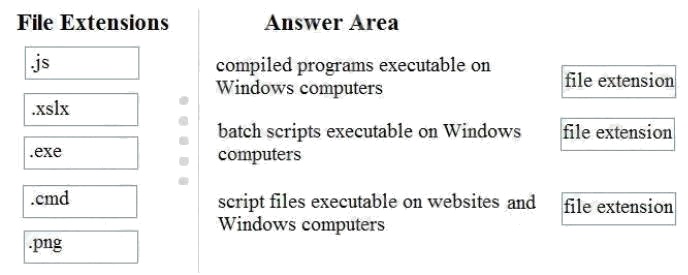
Answer:
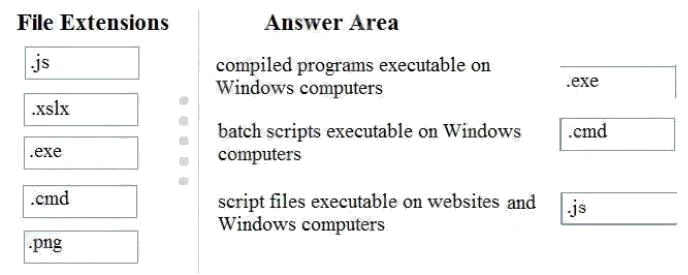
Comments
Question 7
Setting a database to run on a cluster of servers is an example of applying:
- A. accessibility
- B. availability
- C. confidentially
- D. integrity
Answer:
A
Comments
Question 8
Encrypting a hard disk is an example of ensuring:
- A. security be default
- B. confidentially
- C. integrity
- D. least privilege
Answer:
B
Comments
Question 9
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
Hot Area: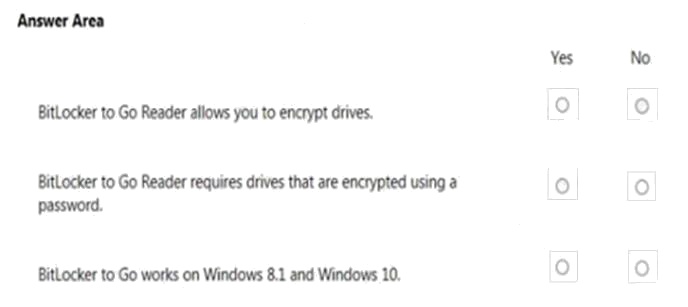
Answer:
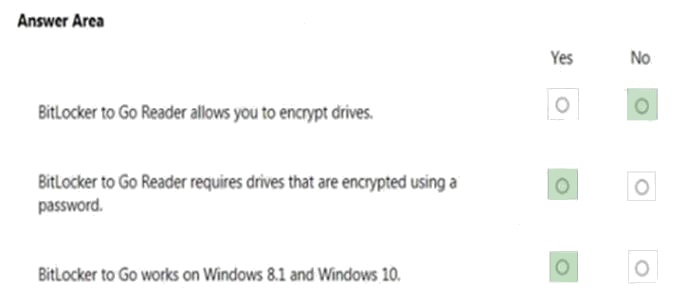
Comments
Question 10
You have an application that communicates by using plain text. You want to secure communications between the application
and a server at the network layer.
What should you implement?
- A. TLS
- B. SFTP
- C. SSH
- D. IPsec
Answer:
D
Explanation:
Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts the packets of data sent
over an Internet Protocol network. It operates at the network (layer 3 in the OSI model)
Incorrect Answers:
A, C: TLS and SSH are cryptographic protocols designed to provide communications security over a network. They operate
at the application layer, or layer 7 of the OSI model.
B: SFTP provides file access, file transfer, and file management over a reliable data stream. It operates at the application
layer, or layer 7 of the OSI model.
References: https://en.wikipedia.org/wiki/IPsec https://en.wikipedia.org/wiki/Transport_Layer_Security
https://en.wikipedia.org/wiki/SSH_File_Transfer_Protocol
Comments
Page 1 out of 16
Viewing questions 1-10 out of 168
page 2