microsoft 98-366 practice test
Networking Fundamentals
Last exam update: Jul 20 ,2024
Question 1
This question requires that you evaluate the underlined text to determine if it is correct.
The four IEEE standards, 802.11a, b, g, and n, are collectively known as "mobile ad hoc" networks.
Select the correct answer if the underlined text does not make the statement correct. Select 'No change is needed" if the
underlined text makes the statement correct.
- A. WiMAX
- B. Bluetooth
- C. WiFi
- D. No change is needed
Answer:
C
Explanation:
IEEE 802.11 is a set of media access control (MAC) and physical layer (PHY) specifications for implementing wireless local
area network (WLAN) computer communication in the 2.4, 3.6, 5, and 60 GHz frequency bands. They are created and
maintained by the IEEE LAN/MAN Standards Committee (IEEE 802). The base version of the standard was released in
1997, and has had subsequent amendments. The standard and amendments provide the basis for wireless network
products using the Wi-Fi brand.
Question 2
What happens when an 802.11b node starts broadcasting within the range of an 802.llg access point?
- A. The access point will transmit, but the node will be unable to receive.
- B. A connection will be established.
- C. Both the node and the access point will be unable to transmit.
- D. The node will transmit, but the access point will be unable to receive.
Answer:
B
Explanation:
802.11g hardware is fully backward compatible with 802.11b hardware.
Question 3
What happens when an 802.11b node starts broadcasting within the range of an 802.llg access point?
- A. The access point will transmit, but the node will be unable to receive.
- B. A connection will be established.
- C. Both the node and the access point will be unable to transmit.
- D. The node will transmit, but the access point will be unable to receive.
Answer:
B
Explanation:
802.11g hardware is fully backward compatible with 802.11b hardware.
Question 4
Which of the following uses pointer records and A records?
- A. IDS
- B. DNS Server
- C. NAT Server
- D. IPS
Answer:
B
Explanation:
DNS records include:
* A
Address record
* PTR
Pointer record
Question 5
Tracert is used to:
- A. Manage routing tables dynamically.
- B. Manage session-oriented connections between nodes.
- C. Report the route taken by packets across an IP network.
- D. Report the shortest route between different networks.
Answer:
C
Explanation:
In computing, traceroute (treacert) is a computer network diagnostic tool for displaying the route (path) and measuring transit
delays of packets across an Internet Protocol (IP) network.
Question 6
What type of record does DNS use to find a mail service?
- A. Service (SRV) DNS record
- B. Canonical (CNAME) DNS record
- C. Mail Exchanger (MX) DNS record
- D. Host (A) DNS record
Answer:
C
Explanation:
A mail exchanger record (MX record) is a type of resource record in the Domain Name System that specifies a mail server
responsible for accepting email messages on behalf of a recipient's domain, and a preference value used to prioritize mail
delivery if multiple mail servers are available. The set of MX records of a domain name specifies how email should be routed
with the Simple Mail Transfer Protocol (SMTP).
Question 7
A network that separates an organization's private network from a public network is a/an:
- A. Firewall
- B. Extranet
- C. Perimeter
- D. Internet
Answer:
C
Explanation:
A network perimeter is the boundary between the private and locally managed-and-owned side of a network and the public
and usually provider-managed side of a network.
Question 8
This question requires that you evaluate the underlined text to determine if it is correct.
An ICMP ping message is sent at the application layer of the OSI model.
Review the underlined text. If it makes the statement correct, select No change is needed. If the statement is incorrect,
select the answer choice that makes the statement correct.
- A. network
- B. transport
- C. data-link
- D. No change is needed
Answer:
A
Question 9
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
Hot Area: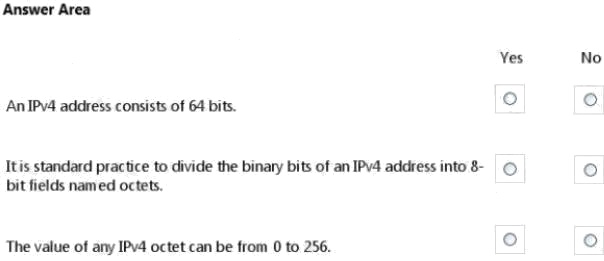
Answer:
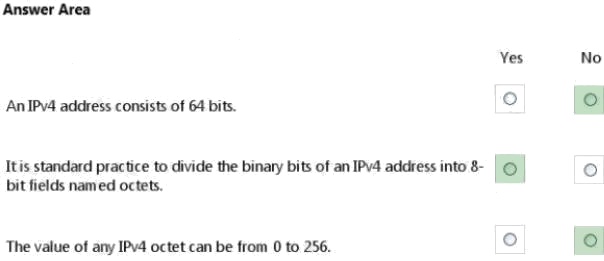
Explanation:
* No.
IPv4 uses a 32-bit address scheme.
* Yes.
IPv4 addresses may be written in any notation expressing a 32-bit integer value, but for human convenience, they are most
often written in the dot-decimal notation, which consists of four octets of the address expressed individually in decimal and
separated by periods.
* No.
Each octet has a value between 0 and 255.
Question 10
Which of these addresses is a multicast address?
- A. 127.0.0.1
- B. 169.254.0.1
- C. 192.168.0.1
- D. 224.0.0.1
Answer:
D
Explanation:
The full range of multicast addresses is from 224.0.0.0 to 239.255.255.255.
Question 11
Security is a concern on wireless networks due to:
- A. The radio broadcast access method.
- B. Spread spectrum issues.
- C. Frequency modulation issues.
- D. The potential for cross-talk.
Answer:
A
Question 12
Which wireless communication problem is caused by electromagnetic waves?
- A. Fading
- B. Attenuation
- C. Interference
- D. Diffraction
Answer:
C
Explanation:
Because the air is shared by all transmitters, transmissions by any device at the same frequency as an access point's radio
can cause interference. Because 802.11 wireless networks operate in unlicensed bands used by many technologies, such
as microwave ovens, video surveillance cameras, cordless phones, they are subject to interference.
Question 13
Teredo tunneling is a protocol that:
- A. Translates Internet Protocol version 4 (IPv4) to Internet Protocol version 6 (IPv6).
- B. Allows IPv6 connectivity through IPv4 devices.
- C. Provides VPN security.
- D. Dynamically allocates IPv6 addresses.
Answer:
B
Explanation:
Teredo alleviates this problem by encapsulating IPv6 packets within UDP/IPv4 datagrams, which most NATs can forward
properly. Thus, IPv6-aware hosts behind NATs can be used as Teredo tunnel endpoints even when they don't have a
dedicated public IPv4 address.
Question 14
A Layer 2 device that connects multiple computers within a network is a:
- A. Repeater
- B. Switch
- C. Router
- D. Packet
Answer:
B
Explanation:
Layer 2 switching uses the media access control address (MAC address) from the host's network interface cards (NICs) to
decide where to forward frames.
Question 15
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
Hot Area: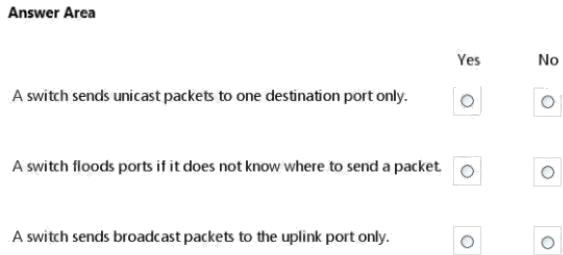
Answer:
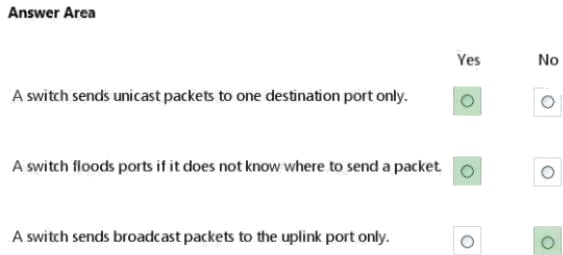
Explanation:
* Yes. Unicast
Unicast is a one-to one connection between the client and the server.
* Yes. No.
As part of the learning process, a switch will flood (broadcast) the single frame out all of its other ports when it cannot find
the destination MAC address in the switchs lookup table.