Question 1
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
Hot Area:
Answer:

Explanation:
* Dynamic Routing. A router with dynamically configured routing tables is known as a dynamic router. Dynamic routing
consists of routing tables that are built and maintained automatically through an ongoing communication between routers.*
Most of the dominant routing algorithms are dynamic routing algorithms, which adjust to changing network circumstances by
analyzing incoming routing update messages. If the message indicates that a network change has occurred, the routing
software recalculates routes and sends out new routing update messages. These messages permeate the network,
stimulating routers to rerun their algorithms and change their routing tables accordingly.
* When there are multiple routes to the same destination, a router must have a mechanism for calculating the best path. A
metric is a variable assigned to routes as a means of ranking them from best to worst or from most preferred to
leastpreferred.
Comments
Question 2
DRAG DROP
Match the VPN connection type to the corresponding definition.
To answer, drag the appropriate VPN term from the column on the left to its definition on the right. Each term may be used
once, more than once, or not at all. Each correct match is worth one point.
Select and Place: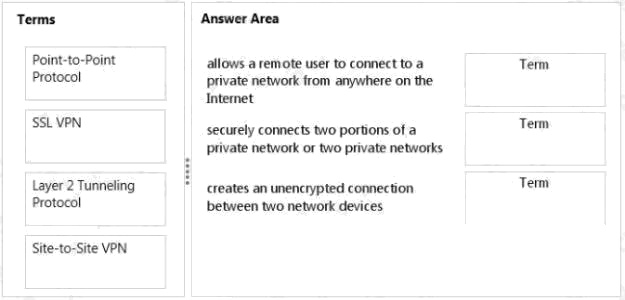
Answer:
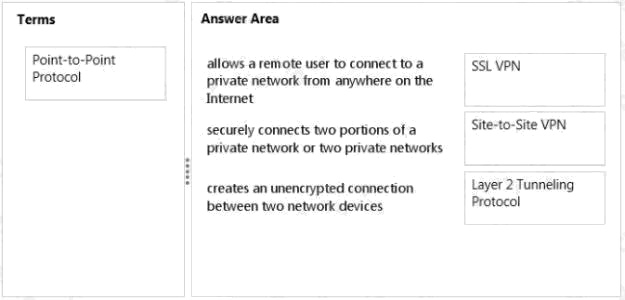
Explanation:
* An SSL VPN (Secure Sockets Layer virtual private network) is a form of VPN that can be used with a standard Web
browser. In contrast to the traditional Internet Protocol Security (IPsec) VPN, an SSL VPN does not require the installation
ofspecialized client software on the end user's computer. It's used to give remote users with access to Web applications,
client/server applications and internal network connections.
* A site-to-site VPN allows offices in multiple fixed locations to establish secure connections with each other over a public
network such as the Internet.
* Layer 2 Tunneling Protocol (L2TP) is a tunneling protocol used to support virtual private networks (VPNs) or as part of the
delivery of services by ISPs. It does not provide any encryption or confidentiality by itself.
Comments
Question 3
HOTSPOT
Your network uses routers configured with the RIP router protocol.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:

Explanation:
Routing Information Protocol (RIP) uses hop count as the metric to rate the value of different routes. The hop count is the
number of devices that can be traversed in a route. A directly connected network has a metric of zero; an unreachable
network has a metric of 16. This limited metric range makes RIP unsuitable for large networks.
The Routing Information Protocol (RIP) sends routing-update messages at regular intervals and when the network topology
changes. When a device receives a RIP routing update that includes changes to an entry, the device updates its routing
table to reflect the new route. The metric value for the path is increased by 1, and the sender is indicated as the next hop.
RIP devices maintain only the best route (the route with the lowest metric value) to a destination. After updating its routing
table, the device immediately begins transmitting RIP routing updates to inform other network devices of the change. These
updates are sent independently of the regularly scheduled updates that RIP devices send.
Summarizing routes in RIP Version 2 improves scalability and efficiency in large networks. Summarizing IP addresses
means that there is no entry for child routes (routes that are created for any combination of the individual IP addresses
contained within a summary address) in the RIP routing table, reducing the size of the table and allowing the router to handle
more routes.
It is a stable protocol that uses a distance-vector algorithm to calculate routes.
References:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/iproute_rip/configuration/15-mt/irr-15-mt-book/irr-cfg-info-prot.html
Comments
Question 4
Which protocol is a transport layer protocol?
- A. FTP
- B. IP
- C. UDP
- D. ASCII
Answer:
C
Explanation:
Transport layer protocols include: UDP, TCP
Comments
Question 5
The protocol that maps IP addresses to a Media Access Control (MAC) address is:
- A. Internet Message Access Protocol (IMAP).
- B. Dynamic Host Configuration Protocol (DHCP).
- C. Routing Information Protocol (RIP).
- D. User Datagram Protocol (UDP).
- E. Address Resolution Protocol (ARP).
Answer:
E
Explanation:
Address Resolution Protocol (ARP) is a protocol for mapping an Internet Protocol address (IP address) to a physical
machine address (MAC address) that is recognized in the local network.
Comments
Question 6
What is an example of a network device that associates a network address with a port?
- A. Switch
- B. Router
- C. Hub
- D. DSL modem
Answer:
B
Explanation:
A router is a Layer 3 gateway device, meaning that it connects two or more networks and that the router operates at the
network layer of the OSI model.
Incorrect:
not switch: Any switch that provides this 'basic' functionality, operates at the 2nd OSI layer also known as the Datalink Layer.
not hub: A network hub, or a repeater, is a simple network device that does not manage any of the traffic coming through it.
Any packet entering a port is flooded out or "repeated" on every other port, except for the port of entry.
Comments
Question 7
Which of the following is a public IP address?
- A. 10.156.89.1
- B. 68.24.78.221
- C. 172.16.152.48
- D. 192.168.25.101
Answer:
B
Explanation:
Incorrect:
The private address space specified in RFC 1918 is defined by the following three address blocks:
not D: 192.168.0.0/16
The 192.168.0.0/16 private network can be interpreted either as a block of 256 class C network IDs or as a 16-bit assignable
address space (16 host bits) that can be used for any subnetting scheme within the private organization. The 192.168.0.0/16
private network allows the following range of valid IP addresses: 192.168.0.1 to 192.168.255.254.
Not A:
10.0.0.0/8
The 10.0.0.0/8 private network is a class A network ID that allows the following range of valid IP addresses: 10.0.0.1 to
10.255.255.254. The 10.0.0.0/8 private network has 24 host bits that can be used for any subnetting scheme within the
private organization.
Not C:
172.16.0.0/12
The 172.16.0.0/12 private network can be interpreted either as a block of 16 class B network IDs or as a 20-bit assignable
address space (20 host bits) that can be used for any subnetting scheme within the private organization. The 172.16.0.0/12
private network allows the following range of valid IP addresses: 172.16.0.1 to 172.31.255.254. Reference: Technet, Public
and Private Addresses
Comments
Question 8
This question requires that you evaluate the underlined text to determine if it is correct.
According to the OSI model, encryption takes place on the "transport layer".
Select the correct answer if the underlined text does not make the statement correct. Select 'No change is needed" if the
underlined text makes the statement correct.
- A. Presentation
- B. Network
- C. Application
- D. No change is needed
Answer:
A
Explanation:
SSL or TLS encryption takes place at the presentation layer, Layer 6 of the OSI model.
Comments
Question 9
What is a similarity between Layer 2 and Layer 3 switches?
- A. Both provide a high level of security to the network.
- B. Both use logical addressing to forward transmissions.
- C. Both forward packets onto the network.
- D. Both allow the implementation of VLANs.
Answer:
D
Explanation:
A single layer-2 network may be partitioned to create multiple distinct broadcast domains, which are mutually isolated so that
packets can only pass between them via one or more routers; such a domain is referred to as a virtual local area network,
virtual LAN or VLAN.
LANs are layer 2 constructs, so they can be supported by both Layer 2 and Layer 3 switches.
Incorrect:
Not A: Layer 2 switches do not provide high level of security.
Not B: Another name for logical address is IP address. Only Layer 3 switches uses IP address. Layer 2 switches uses MAC
addresses. Not C: only Layer 3 switches forward packets on the network (like routers).
Comments
Question 10
This question requires that you evaluate the underlined text to determine if it is correct.
An Address Resolution Protocol (ARP) table is used to associate IP addresses with "host names".
Select the correct answer if the underlined text does not make the statement correct. Select 'No change is needed" if the
underlined text makes the statement correct.
- A. MAC addresses
- B. HomeGroup membership
- C. Preferred routers
- D. No change is needed
Answer:
A
Explanation:
Address Resolution Protocol (ARP) is a protocol for mapping an Internet Protocol address (IP address) to a physical
machine address (MAC address) that is recognized in the local network.
Comments
Page 1 out of 20
Viewing questions 1-10 out of 204
page 2