Question 1
Which three types of peer devices are supported for CoS-based IPsec VPNs? (Choose three.)
- A. branch SRX Series device
- B. third-party device
- C. cSRX
- D. high-end SRX Series device
- E. vSRX
Answer:
ADE
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/secuirty-cos-based-ipsec-vpns.html
Comments
Question 2
You are asked to configure a new SRX Series CPE device at a remote office. The device must
participate in forwarding MPLS and IPsec traffic.
Which two statements are true regarding this implementation? (Choose two.)
- A. Host inbound traffic must not be processed by the flow module
- B. Host inbound traffic must be processed by the flow module
- C. The SRX Series device can process both MPLS and IPsec with default traffic handling
- D. A firewall filter must be configured to enable packet mode forwarding
Answer:
BD
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-packet-based-forwarding.html
Comments
Question 3
Which three roles or protocols are required when configuring an ADVPN? (Choose three.)
- A. OSPF
- B. shortcut partner
- C. shortcut suggester
- D. IKEv1
- E. BGP
Answer:
ABC
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-auto-discovery-vpns.html
Comments
Question 4
You must troubleshoot ongoing problems with IPsec tunnels and security policy processing. Your
network consists of SRX340s and SRX5600s.
In this scenario, which two statements are true? (Choose two.)
- A. IPsec logs are written to the kmd log file by default
- B. IKE logs are written to the messages log file by default
- C. You must enable data plane logging on the SRX340 devices to generate security policy logs
- D. You must enable data plane logging on the SRX5600 devices to generate security policy logs
Answer:
AD
Comments
Question 5
Click the Exhibit button.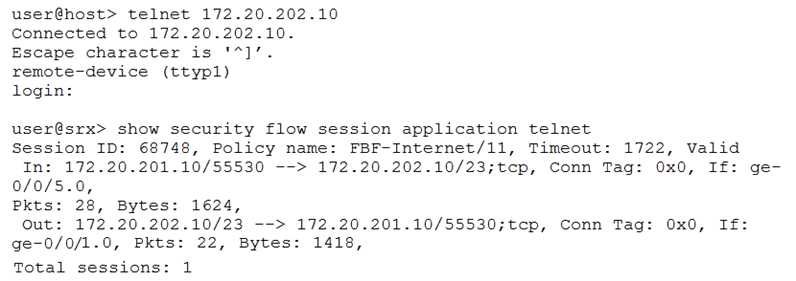
You are implementing a new branch site and want to ensure Internet traffic is sent directly to your
ISP and other traffic is sent to your company headquarters. You have configured filter-based
forwarding to accomplish this objective. You verify proper functionality using the outputs shown in
the exhibit.
Which two statements are true in this scenario? (Choose two.)
- A. The session utilizes one routing instance
- B. The ge-0/0/5 and ge-0/0/1 interfaces must reside in a single security zone
- C. The ge-0/0/5 and ge-0/0/1 interfaces can reside in different security zones
- D. The session utilizes two routing instances
Answer:
AC
Comments
Question 6
Click the Exhibit button.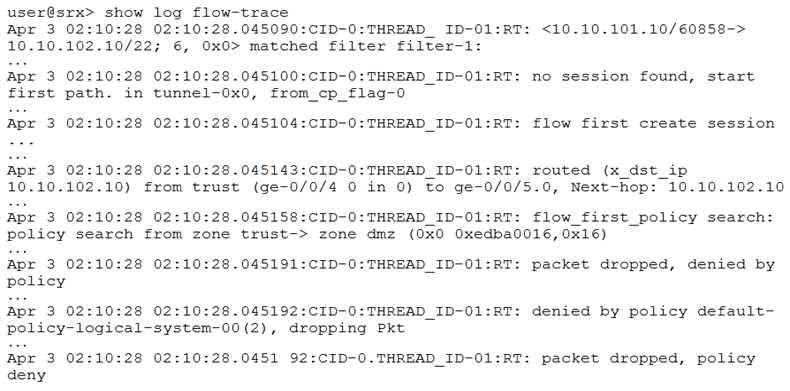
The exhibit shows a snippet of a security flow trace. A user cannot open an SSH session to a server.
Which action will solve the problem?
- A. Create a security policy that matches the traffic parameters
- B. Edit the source NAT to correct the translated address
- C. Create a route entry to direct traffic into the configured tunnel
- D. Create a route to the desired server
Answer:
A
Comments
Question 7
Click the Exhibit button.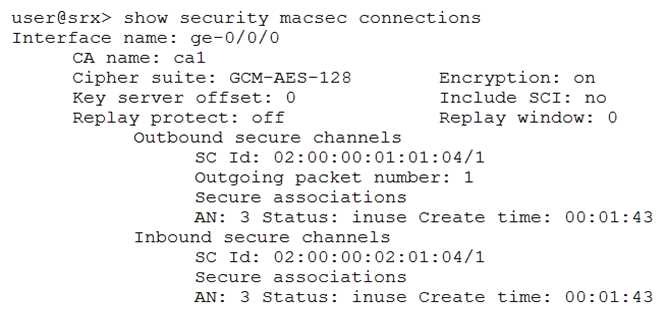
Referring to the exhibit, which two statements are true? (Choose two.)
- A. Data is transmitted across the link in plaintext
- B. The link is not protected against man-in-the-middle attacks
- C. The link is protected against man-in-the-middle attacks
- D. Data is transmitted across the link in cyphertext
Answer:
BD
Comments
Question 8
You are asked to secure your network against TOR network traffic.
Which two Juniper products would accomplish this task? (Choose two.)
- A. Contrail Edge
- B. Contrail Insights
- C. Juniper Sky ATP
- D. Juniper ATP Appliance
Answer:
CD
Comments
Question 9
You are asked to implement the session cache feature on an SRX5400.
In this scenario, what information does a session cache entry record? (Choose two.)
- A. The type of processing to do for ingress traffic
- B. The type of processing to do for egress traffic
- C. To which SPU the traffic of the session should be forwarded
- D. To which NPU the traffic of the session should be forwarded
Answer:
BC
Explanation:
Reference:
<
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-packet-based-forwarding.html
>
A session cache entry records:
To which SPU the traffic of the conversion should be forwarded
To which egress port the traffic of the conversion should be forwarded in Express Path mode
What processing to do for egress traffic, for example, NAT translation in Express Path mode
Comments
Question 10
Which feature of Sky ATP is deployed with Policy Enforcer?
- A. zero-day threat mitigation
- B. software image snapshot support
- C. device inventory management
- D. service redundancy daemon configuration support
Answer:
A
Comments
Page 1 out of 8
Viewing questions 1-10 out of 88
page 2