Question 1
Click the Exhibit button.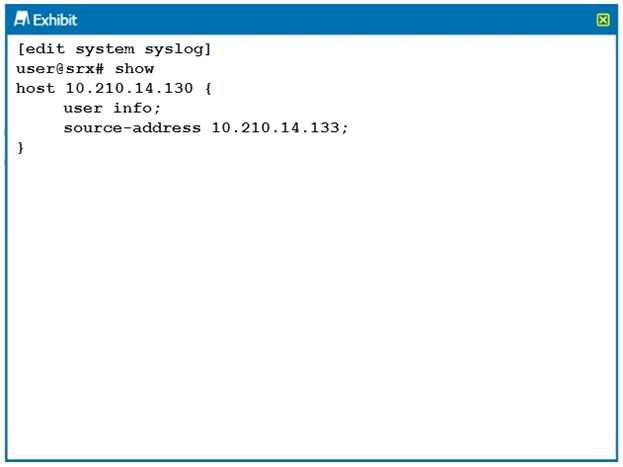
Referring to the configuration shown in the exhibit, which two statements are true? (Choose two.)
A. The log is being stored on the local Routing Engine.
B. The log is being sent to a remote server.
C. The syslog is configured for a user facility.
D. The syslog is configured for an info facility.
Answer:
BC
//www.juniper.net/documentation/en_US/junos/topics/reference/configuration-
statement/syslog-edit-system.html
Comments
Question 2
Your network uses a remote e-mail server that is used to send and receive e-mails for your users.
In this scenario, what should you do to protect users from receiving malicious files thorugh e-mail?
- A. Deploy Sky ATP IMAP e-mail protection
- B. Deploy Sky ATP MAPI e-mail protection
- C. Deploy Sky ATP SMTP e-mail protection
- D. Deploy Sky ATP POP3 e-mail protection
Answer:
C
Comments
Question 3
Which two statements are true about virtualized SRX Series devices? (Choose two.)
A. vSRX cannot be deployed in transparent mode.
B. cSRX can be deployed in routed mode.
C. cSRX cannot be deployed in routed mode.
D. vSRX can be deployed in transparent mode.
Answer:
BD
//www.juniper.net/documentation/en_US/csrx/information-products/pathway-pages/security-
csrx-contrail-guide-pwp.pdf
Comments
Question 4
A routing change occurs on an SRX Series device that involves choosing a new egress interface.
In this scenario, which statement is true for all affected current sessions?
A. The current session are torn dowm only if the policy-rematch option has been enabled.
B. The current sessions do not change.
C. The current sessions are torn down and go through first path processing based on the new route.
D. The current sessions might change based on the corresponding security policy.
Answer:
B
//forums.juniper.net/t5/ScreenOS-Firewalls-NOT-SRX/Affect-of-Route-change-on-Session/m-
p/27810#M11385
Comments
Question 5
What information does JIMS collect from domain event log sources? (Choose two.)
- A. For user login events, JIMS collects the username and group membership information.
- B. For device login events. JIMS collects the devide IP address and operating system version.
- C. For device login events, JIMS collects the device IP address and machine name information.
- D. For user login events, JIMS collects the login source IP address and username information.
Answer:
CD
Comments
Question 6
Which statement describes the AppTrack module in AppSecure?
A. The AppTrack module provides enforcement with the ability to block traffic, based on specific
applications.
B. The AppTrack module provides control by the routing of traffic, based on the application.
C. The AppTrack module identifies the applications that are present in network traffic.
D. The AppTrack module provides visibility and volumetric reporting of application usage on the
network.
Answer:
D
//www.juniper.net/documentation/en_US/junos/topics/topic-map/security-application-
tracking.html
Comments
Question 7
Click the Exhibit button.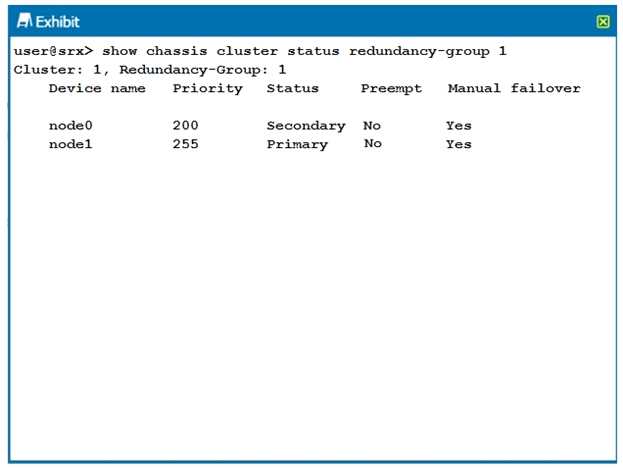
Which two statements describe the output shown in the exhibit? (Choose two.)
- A. Node 0 is passing traffic for redundancy group 1.
- B. Redundancy group 1 experienced an operational failure.
- C. Redundancy group 1 was administratively failed over.
- D. Node 1 is passing traffic for redundancy group1.
Answer:
CD
Comments
Question 8
Which statement is true about JATP incidents?
- A. Incidents have an associated threat number assigned to them.
- B. Incidents are sorted by category, followed by severity.
- C. Incidents consist of all the events associated with a single threat.
- D. Incidents are always automatically mitigated.
Answer:
A
Comments
Question 9
Click the Exhibit button.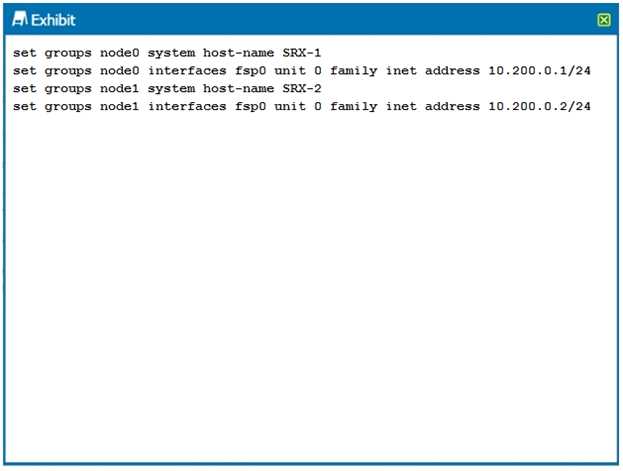
You are configuring an SRX chassis cluster with the node-specific hostname and management
address. Referring to the exhibit, which configuration completes this requirement?
A)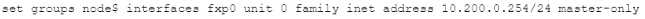
B)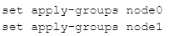
C)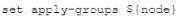
D)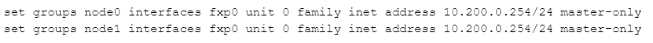
A. Option A
B. Option B
C. Option C
D. Option D
Answer:
C
//kb.juniper.net/InfoCenter/index?page=content&id=KB31080
Comments
Question 10
You must ensure that all encrypted traffic passing through your SRX device uses strong protocols and
ciphers.
Which feature should you implement to satisfy this requirement?
- A. SSL proxy
- B. AppSecure
- C. JIMS
- D. JATP
Answer:
A
Comments
Page 1 out of 9
Viewing questions 1-10 out of 91
page 2