Question 1
Which two addresses are valid address book entries? (Choose two.)
- A. 173.145.5.21/255.255.255.0
- B. 153.146.0.145/255.255.0.255
- C. 203.150.108.10/24
- D. 191.168.203.0/24
Answer:
bd
Comments
Question 2
Which two statements are correct about functional zones? (Choose two.)
- A. Functional zones must have a user-defined name.
- B. Functional zone cannot be referenced in security policies or pass transit traffic.
- C. Multiple types of functional zones can be defined by the user.
- D. Functional zones are used for out-of-band device management.
Answer:
bd
Comments
Question 3
You want to deploy a NAT solution.
In this scenario, which solution would provide a static translation without PAT?
- A. interface-based source NAT
- B. pool-based NAT with address shifting
- C. pool-based NAT with PAT
- D. pool-based NAT without PAT
Answer:
d
Comments
Question 4
Which two statements are correct about IKE security associations? (Choose two.)
- A. IKE security associations are established during IKE Phase 1 negotiations.
- B. IKE security associations are unidirectional.
- C. IKE security associations are established during IKE Phase 2 negotiations.
- D. IKE security associations are bidirectional.
Answer:
ad
Comments
Question 5
What are two Juniper ATP Cloud feed analysis components? (Choose two.)
- A. IDP signature feed
- B. C&C cloud feed
- C. infected host cloud feed
- D. US CERT threat feed
Answer:
b
Comments
Question 6
Click the Exhibit button.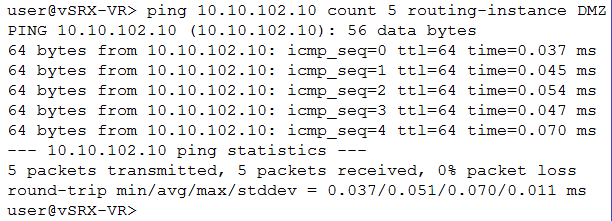
Referring to the exhibit, which two statements are correct about the ping command? (Choose two.)
- A. The DMZ routing-instance is the source.
- B. The 10.10.102.10 IP address is the source.
- C. The 10.10.102.10 IP address is the destination.
- D. The DMZ routing-instance is the destination.
Answer:
ac
Comments
Question 7
What must be enabled on an SRX Series device for the reporting engine to create reports?
- A. packet capture
- B. security logging
- C. system logging
- D. SNMP
Answer:
b
Comments
Question 8
You want to block executable files (*.exe) from being downloaded onto your network.
Which UTM feature would you use in this scenario?
- A. IPS
- B. Web filtering
- C. content filtering
- D. antivirus
Answer:
b
Comments
Question 9
Which two statements are correct about the default behavior on SRX Series devices? (Choose two.)
- A. The SRX Series device is in flow mode.
- B. The SRX Series device supports stateless firewalls filters.
- C. The SRX Series device is in packet mode.
- D. The SRX Series device does not support stateless firewall filters.
Answer:
ab
Comments
Question 10
When transit traffic matches a security policy, which three actions are available? (Choose three.)
- A. Allow
- B. Discard
- C. Deny
- D. Reject
- E. Permit
Answer:
cde
Comments
Page 1 out of 6
Viewing questions 1-10 out of 66
page 2