isaca ccak practice test
Certificate of Cloud Auditing Knowledge
Last exam update: Jun 29 ,2025
Question 1
Which of the following is the common cause of misconfiguration in a cloud environment?
- A. Absence of effective change control
- B. Using multiple cloud service providers
- C. New cloud computing techniques
- D. Traditional change process mechanisms
Answer:
A
Explanation:
Reference: https://businessinsights.bitdefender.com/the-top-5-cloud-threats-that-smbs-need-to-address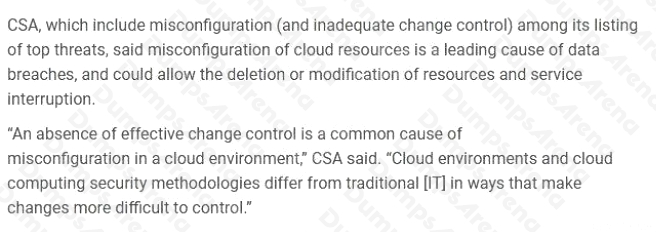
Question 2
Which of the following metrics are frequently immature?
- A. Metrics around Infrastructure as a Service (IaaS) storage and network environments
- B. Metrics around Platform as a Service (PaaS) development environments
- C. Metrics around Infrastructure as a Service (IaaS) computing environments
- D. Metrics around specific Software as a Service (SaaS) application services
Answer:
A
Question 3
Which of the following quantitative measures is KEY for an auditor to review when assessing the implementation of
continuous auditing of performance on a cloud system?
- A. Service Level Objective (SLO)
- B. Recovery Point Objectives (RPO)
- C. Service Level Agreement (SLA)
- D. Recovery Time Objectives (RTO)
Answer:
C
Question 4
Which of the following is MOST important to consider when developing an effective threat model during the introduction of a
new SaaS service into a customer organizations architecture? The threat model:
- A. recognizes the shared responsibility for risk management between the customer and the CSP.
- B. leverages SaaS threat models developed by peer organizations.
- C. is developed by an independent third-party with expertise in the organization’s industry sector.
- D. considers the loss of visibility and control from transitioning to the cloud.
Answer:
A
Question 5
As a developer building codes into a container in a DevSecOps environment, which of the following is the appropriate
place(s) to perform security tests?
- A. Within developer’s laptop
- B. Within the CI/CD server
- C. Within version repositories
- D. Within the CI/CD pipeline
Answer:
D
Question 6
An organization has an ISMS implemented, following ISO 27001 and Annex A controls. The CIO would like to migrate some
of the infrastructure to the cloud. Which of the following standards would BEST assist in identifying controls to consider for
this migration?
- A. ISO/IEC 27701
- B. ISO/IEC 22301
- C. ISO/IEC 27002
- D. ISO/IEC 27017
Answer:
D
Explanation:
ISO/IEC 27017 standard defines the requirements for an information security management system (ISMS). Note that the
entire organization is not necessarily affected by the standard, because it all depends on the scope of the ISMS. The scope
could be limited by the provider to one group within an organization, and there is no guarantee that any group outside of the
scope has appropriate ISMSs in place. It is up to the auditor to verify that the scope of the engagement is fit for purpose. As
the customer, you are responsible for determining whether the scope of the certification is relevant for your purposes.
Question 7
An organization deploying the Cloud Control Matrix (CCM) to perform a compliance assessment will encompass the use of
the Corporate Governance Relevance feature to filter out those controls:
- A. relating to policies, processes, laws, regulations, and institutions conditioning the way an organization is managed, directed, or controlled.
- B. that can be either of a management or of a legal nature, therefore requiring an approval from the Change Advisory Board.
- C. that require the prior approval from the Board of Directors to be funded (for either make or buy), implemented, and reported on.
- D. that can be either of an administrative or of a technical nature, therefore requiring an approval from the Change Advisory Board.
Answer:
A
Question 8
How should controls be designed by an organization?
- A. By the internal audit team
- B. Using the ISO27001 framework
- C. By the cloud provider
- D. Using the organization’s risk management framework
Answer:
A
Explanation:
Reference: https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2016/internal-control-key-to-delivering-
stakeholder-value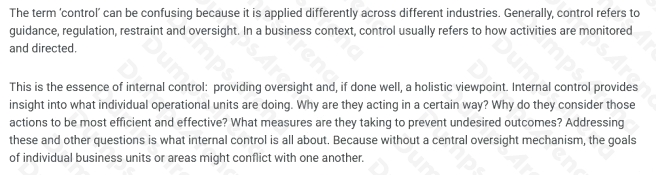
Question 9
Changes to which of the following will MOST likely influence the expansion or reduction of controls required to remediate the
risk arising from changes to an organizations SaaS vendor?
- A. Risk exceptions policy
- B. Contractual requirements
- C. Risk appetite
- D. Board oversight
Answer:
C
Explanation:
Reference: https://assets.kpmg/content/dam/kpmg/ch/pdf/key-risks-internal-audit-2018.pdf
Question 10
What data center and physical security measures should a cloud customer consider when assessing a cloud service
provider?
- A. Assess use of monitoring systems to control ingress and egress points of entry to the data center.
- B. Implement physical security perimeters to safeguard personnel, data and information systems.
- C. Conduct a due diligence to verify the cloud provider applies adequate physical security measures.
- D. Review internal policies and procedures for relocation of hardware and software to an offsite location.
Answer:
C
Explanation:
Reference: https://www.omg.org/cloud/deliverables/CSCC-Security-for-Cloud-Computing-10-Steps-to-Ensure-Success.pdf
Question 11
Prioritizing assurance activities for an organizations cloud services portfolio depends PRIMARILY on an organizations
ability to:
- A. schedule frequent reviews with high-risk cloud service providers.
- B. develop plans using a standardized risk-based approach.
- C. maintain a comprehensive cloud service inventory.
- D. collate views from various business functions using cloud services.
Answer:
A
Question 12
What is the advantage of using dynamic application security testing (DAST) over static application security testing (SAST)
methodology?
- A. Unlike SAST, DAST is a blackbox and programming language agnostic.
- B. DAST can dynamically integrate with most CI/CD tools.
- C. DAST delivers more false positives than SAST.
- D. DAST is slower but thorough.
Answer:
A
Explanation:
Reference: https://www.synopsys.com/blogs/software-security/sast-vs-dast-difference/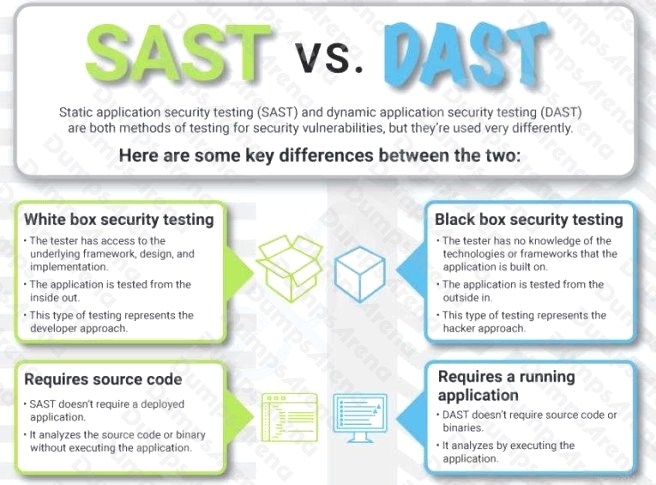
Question 13
What aspect of SaaS functionality and operations would the cloud customer be responsible for and should be audited?
- A. Access controls
- B. Vulnerability management
- C. Source code reviews
- D. Patching
Answer:
A
Explanation:
Reference: https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=919233
Question 14
When migrating to a cloud environment, which of the following should be the PRIMARY driver for the use of encryption?
- A. Cloud Service Provider encryption capabilities
- B. The presence of PII
- C. Organizational security policies
- D. Cost-benefit analysis
Answer:
A
Question 15
When a client’s business process changes, the CSP SLA should:
- A. be reviewed, but the SLA cannot be updated.
- B. not be reviewed, but the cloud contract should be cancelled immediately.
- C. not be reviewed as the SLA cannot be updated.
- D. be reviewed and updated if required.
Answer:
D
Explanation:
Reference: http://www.diva-portal.org/smash/get/diva2:1312384/FULLTEXT01.pdf