Question 1
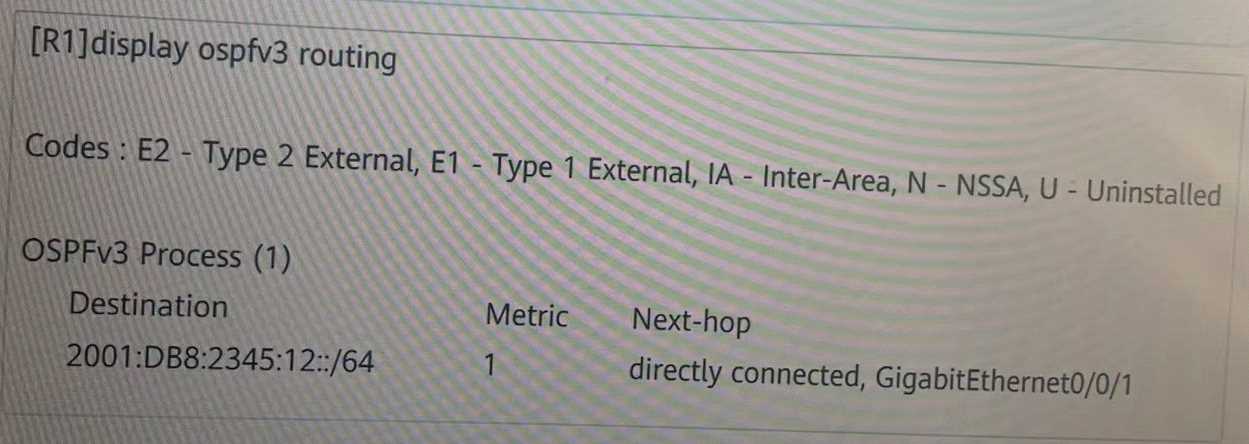
An engineer uses two routers to test IPv6 services, and runs 0SPFv3 to implement IPv6 network
interconnection. R1 is required to be able to access the loopback interface address of R2. The
engineer checked the OSPFv3 routing table entry of R1, as shown in the figure, and found that there
was no route to the loopback interface address of R2. Which of the following reasons could not be
the cause?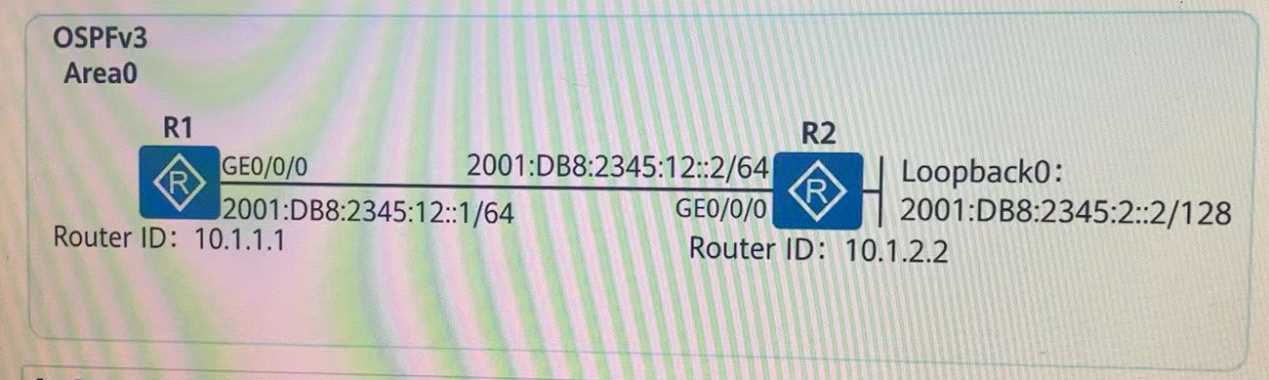
- A. R2 advertises the loopback interface into different OSPFv3 processes
- B. R2 does not have 0SPFv3 enabled on the loopback interface
- C. R2 does not use network to advertise loopback address in area 0
- D. R2 is not configured with the Router ID used in the OSPFv3 process
Answer:
B
Comments
Question 2
aboutOSPFWhich of the following statements is false?
- A. For a pair of additional 0hers on an Ethernet link, it is normal to stop clearing in the 2-72 state
- B. Stalling in ExStart state may be a bad match between neighbor routers
- C. stagnantINThe it state indicates that the router has received the neighbor'sHello message. butHell messagedoes not include this routerOSPF Router ID
- D. The two router databases are synchronized, SPFAn error occurred in the calculation, it must be because of the RouterID repeated
Answer:
A
Comments
Question 3
In the same environment, engineers A and B execute the tracert command. The destination
addresses are the same, but the paths are different. What are the possible reasons?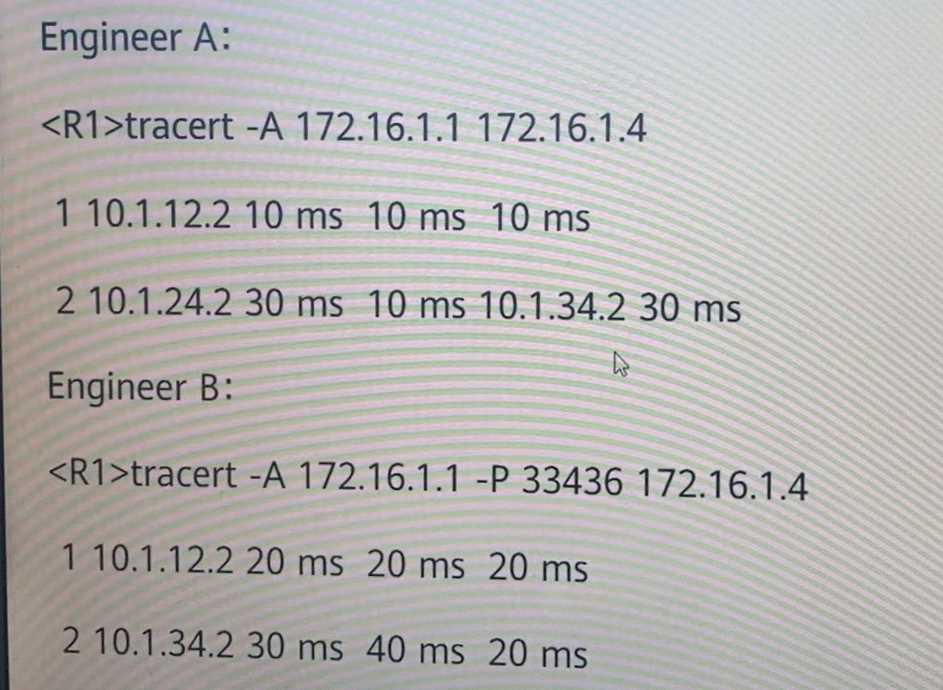
- A. The phenomenon is abnormal, the device has an operating system failure
- B. Engineer A's operation error
- C. Engineer B's operation error
- D. The destination port numbers of the UDR packets serving tracert are different, and the hashes reach different equivalent next hops.
Answer:
D
Comments
Question 4
Which of the following is included in the routine collection of basic equipment information?
- A. License information
- B. Patch information
- C. The software version the device is running
- D. Whether the configuration is saved
Answer:
A, B, C, D
Comments
Question 5
According to this picture, we can judge that R4 is on?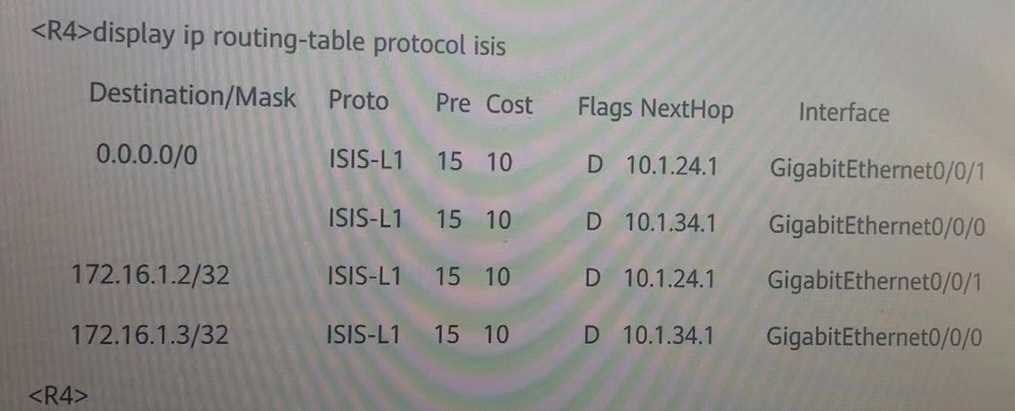
- A. 1 default route
- B. 2 equal-cost default routes
- C. 2 default routes with different costs
- D. 4 equivalent default routes
Answer:
B
Comments
Question 6
IGP converges faster than BGP, which may cause network traffic loss. By enabling the OSPF and BGP
linkage feature of the device, the device can keep the OSPF and BGP linkage during the set linkage
time.____The router makes the link metric value in the LSA advertised to be the maximum value, so
as to inform other OSPF devices not to use this router to forward data, so as to avoid traffic loss.
(Note: If English letters are involved, all uppercase)
Answer:
(STUB-
ROUTER)
Comments
Question 7
OSPF is deployed in a campus to achieve network interworking, and OSPF is also enabled on the
GEO/0/2 interface of R3. Area1 is deployed as an NSSA area, and the device addresses are shown in
the figure. An engineer configures a static route on R3 to access the loopback interface address of R4,
and imports the static route in the 0SPF process. At this point, in the Type5 LSA received by R1, the
forwarding address (FA) is____. (Note: Please fill in the IP address without mask)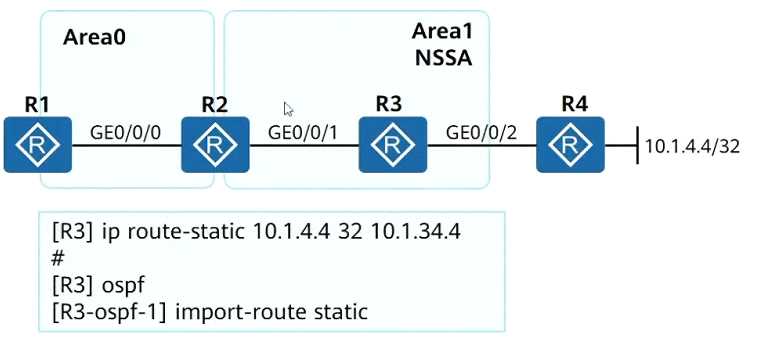
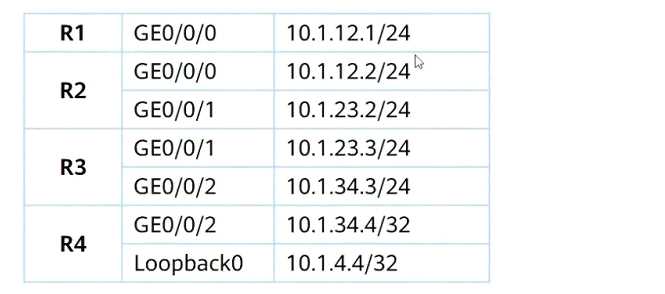
Answer:
(10.1.23.2)
Comments
Question 8
As shown in the figure, in a medium-sized network, BGP generally deploys dual RRs to improve R
reliability. When deploying dual RRs, the Cluster IDs of the two RRs are generally set to be the same.
The reason for this is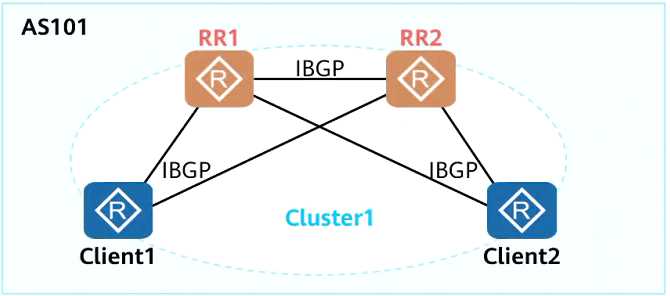
- A. Prevent RR from receiving too many routes and causing insufficient memory
- B. prevent suboptimal
- C. prevent loops
- D. Prevent the client from receiving too many routes and causing it to run out of memory
Answer:
A
Comments
Question 9
According to this picture, you can judge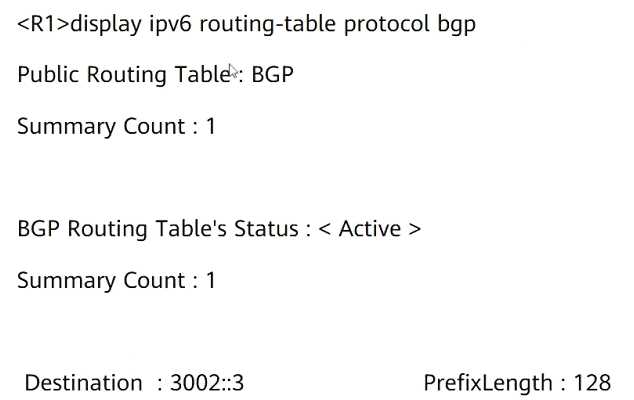
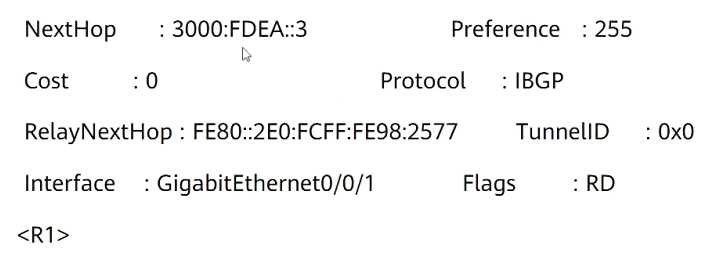
- A. The optimal outgoing interface for R1 to access room 3000: FDEA::3 is GigabitEtherneto/0/1
- B. R1 with 3000:FDEA::3 is IB6P neighbor
- C. R1 has a TCP connection with 3000:FDEA::3
- D. R1 learned route 3002 through IBGP::3/128
Answer:
B, D
Comments
Question 10
Link LSAs of OSPFv3 are propagated throughout the area.
- A. right
- B. wrong
Answer:
B
Comments
Page 1 out of 26
Viewing questions 1-10 out of 266
page 2