Question 1
Refer to the CLI output below: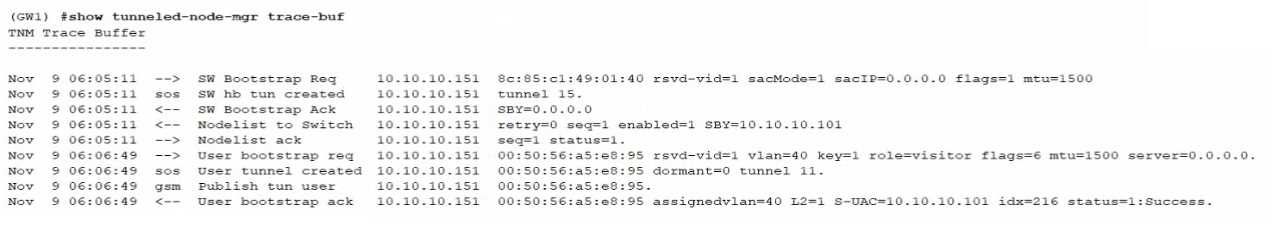
What statement about the output above is correct?
- A. The port-access role was configured with gateway-role visitor
- B. The secondary tunnel endpoint IP is 10.10-10.151.
- C. The client authenticated using dot1x.
- D. The UBT zone was configured to use a user-defined VRF
Answer:
B
Explanation:
The CLI output indicates a tunnel creation process, where "SW hw tun created" refers to the switch
hardware tunnel being created. The line mentioning "BYP-10.10.10.101 -> SW hw tun created to
10.10.10.151 tunnel 15." implies that a tunnel was established to the secondary tunnel endpoint
with the IP address 10.10.10.151. This is a common configuration for User-Based Tunneling (UBT)
setups where traffic is tunneled to a specific endpoint.
Comments
Question 2
Which statement is true given the following CLI output from a CX 6300?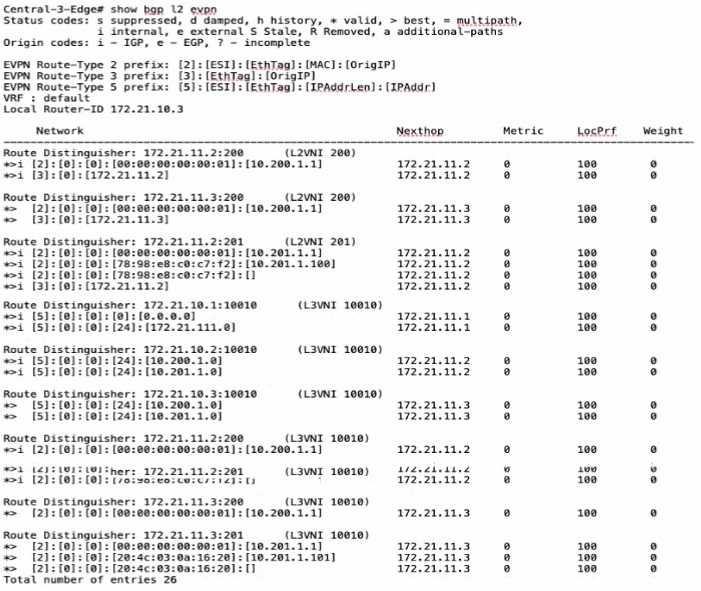
- A. The underlay loopback addresses are in the 172 21 11 x range.
- B. There are two anycast addresses m me overlay fabric.
- C. Duplicate MAC addresses were detected in the overlay fabric
- D. There are three active client overlay VLANs in the overlay fabric
Answer:
A
Explanation:
The CLI output displays EVPN routes and their corresponding next hops. The "Route Distinguisher"
entries followed by IP addresses in the 172.21.11.x range indicate these are loopback addresses used
by the underlay network. The underlay network provides the basic routing and forwarding plane for
the overlay network that EVPN is part of. These loopback addresses are crucial for the proper
functioning of the EVPN control plane.
Comments
Question 3
DRAG DROP
Your customer is requesting a 4-ciass LAN queuing model tor QoS. Following best practices, match
the PHB/DSCP values to the application types.
Answer:
None
Explanation:
Best Effort and Scavenger = DF (0)
Bulk and Transactional Data = AF21 (18)
Multimedia Streaming = AF31 (26)
Real-Time Interactive = EF (46)
Comments
Question 4
You configured" a bridged mode SSID with WPA3-Enterprise and EAP-TLS security. When you connect
an Active Directory joined client that has valid client certificates. ClearPass shows the following error.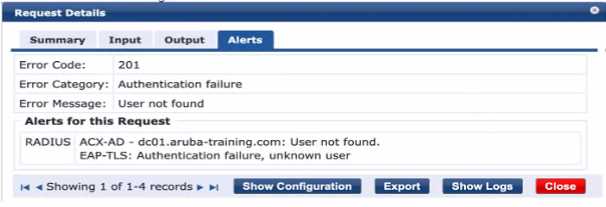
What is needed to resolve this issue?
- A. Enable authorization in your Authentication Method.
- B. Recreate the SSID m tunneled mode.
- C. Modify your ACX-AD authentication source to include the UPN in the search.
- D. Configure ClearPass to trust the client certificate.
Answer:
C
Explanation:
The error message "User not found" indicates that the authentication source, in this case, Active
Directory (AD), is not able to locate the user account based on the current search parameters. This
often occurs when the User Principal Name (UPN) that the client is using to authenticate is not
included in the search parameters of the AD authentication source within ClearPass. By modifying
the AD authentication source to include the UPN in the search, ClearPass will be able to correctly
locate the user account and proceed with the authentication using the valid client certificates.
Comments
Question 5
Refer to the exhibit.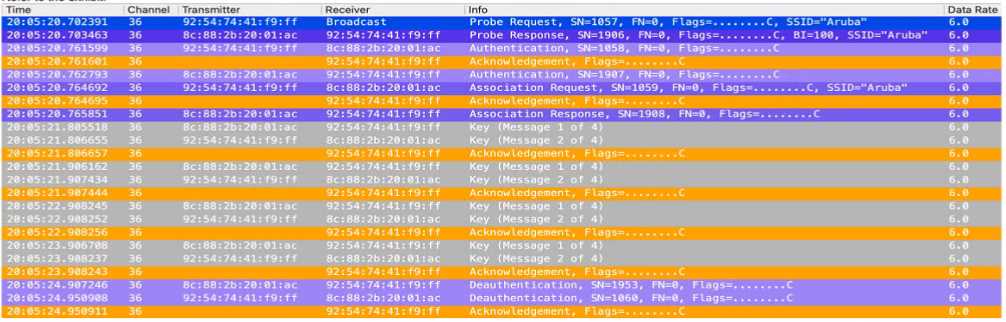
Which statement is true?
- A. The client performed passive scanning
- B. The client is using BSS Fast Transition
- C. The client is failing 802.1X authentication
- D. The client used an incorrect passphrase
Answer:
C
Explanation:
The exhibit shows a series of 802.1X authentication steps with multiple "Deauthentication" frames,
which indicate that the client is not successfully completing the authentication process. Since the
frames show repeated attempts at authentication followed by deauthentication, this suggests that
the client is failing the 802.1X authentication process, which is required for network access in a
WPA2/WPA3-Enterprise security environment.
Comments
Question 6
Exhibit.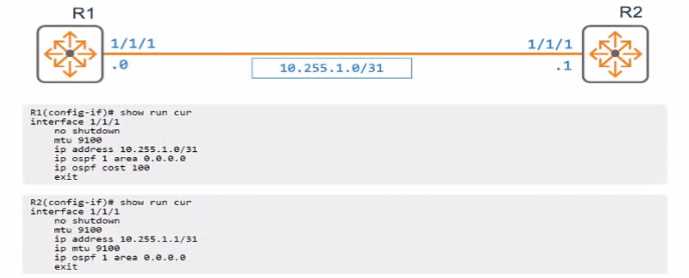
An engineer has applied the above configuration to R1 and R2 However the routers OSPF adjacency
never progresses past the "EXSTART-DR" slate as shown below.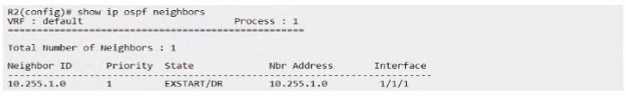
Which configuration action on either router will allow R1 and R2 to progress past the "EXSTART/DR"
state?
- A. Change R1 and R2 to a network type of point-to-point.
- B. Remove the layer 3 MTU configuration.
- C. Ensure the OSPF process is not configured with passive-interface default.
- D. Change the IP address and mask applied to interface 1/1/1.
Answer:
A
Explanation:
In OSPF, the "EXSTART/DR" state indicates that the routers are trying to establish an adjacency but
are unable to progress. This can happen if the OSPF network type is incorrectly configured for the
type of connection between the routers. Given that R1 and R2 are connected via a point-to-point link
(as suggested by the /31 subnet), setting the network type to point-to-point on both routers will
remove the need for DR/BDR election, which is unnecessary on a point-to-point link, and allow OSPF
to progress past the "EXSTART" state and form a full adjacency.
Comments
Question 7
Your customer asked for help to apply an ACL for wireless guest users with the following criteria:
• Wi-Fi guests are on VLAN 555
• allow internet access
• only allow access to public DNS servers
• deny access to all internal networks except for any DHCP server
These session ACLs are already present in the CLI of the mobility gateway group: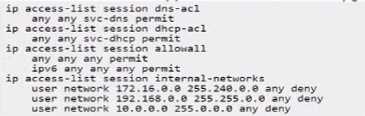
You have access to the CLl. Which user role meets all the criteria?
A)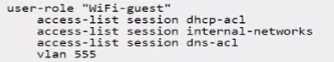
B)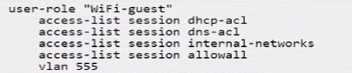
C)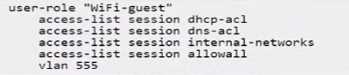
D)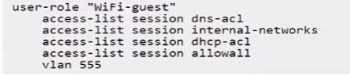
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
A
Explanation:
Based on the criteria provided for wireless guest users, the correct user role configuration must allow
internet access, only allow access to public DNS servers, deny access to all internal networks except
for any DHCP server, and place the Wi-Fi guests on VLAN 555. The ACLs must permit services
necessary for basic internet access (such as DNS and DHCP) and block access to internal networks.
Option A satisfies these criteria with the following configurations:
user-role "WiFi-guest": This defines the role for Wi-Fi guests.
access-list session dhcp-acl: This applies the access list that likely permits DHCP, which is necessary
for guests to obtain an IP address.
access-list session dns-acl: This applies the DNS access list, which likely restricts guests to using public
DNS servers.
access-list session internal-networks: This applies the internal networks access list, which denies
access to internal networks.
vlan 555: This sets the VLAN for Wi-Fi guests to 555.
Options B, C, and D are incorrect because they include access-list session allowall which would
permit all traffic, contradicting the requirement to deny access to all internal networks.
Comments
Question 8
Which command would allow you to verity receipt of a CoA message on an AOS 10 GW?
- A. packet-capture datapath udp 3799
- B. packet-capture controipath udp 3799
- C. packet-capture interprocess udp 3799
- D. tcpdump host-port 3799
Answer:
B
Explanation:
The Change of Authorization (CoA) messages are used in network access control scenarios and are
typically received by the network access server, in this case, an Aruba AOS 10 Gateway. The correct
command to verify the receipt of a CoA message is related to the control path traffic because CoA is
a control plane function.
Option B, packet-capture controlpath udp 3799, is the correct answer because it specifies capturing
control plane traffic on UDP port 3799, which is the standard port for CoA messages.
Options A, C, and D are incorrect because:
Option A captures data plane traffic, not control plane traffic.
Option C's packet-capture interprocess udp 3799 does not refer to a standard command for capturing
CoA messages.
Option D, tcpdump host-port 3799, does not specify the correct syntax for capturing traffic on Aruba
devices.
Comments
Question 9
The ACME company has an AOS-CX 6200 switch stack with an uplink oversubscription ratio of 9.6:1.
They are considering adding two more nodes to the stack without adding any additional uplinks due
to cabling constraints One of their architects has expressed concerns that their critical UDP traffic
from both wired and bridged AP clients will encounter packet drops. They have already applied the
following configuration:
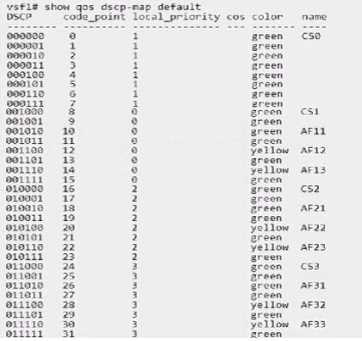
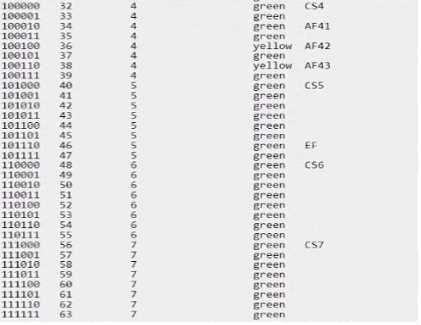
Which strategy will complement this solution to achieve their objective?
- A. edge mark lower priority TCP traffic with AF12
- B. edge mark critical UDP Traffic with CSS
- C. edge mark lower priority TCP traffic with AF11
- D. edge mark critical UDP traffic with AF42
Answer:
D
Explanation:
Given that the ACME company's concern is about UDP traffic potentially encountering packet drops
due to uplink oversubscription, they need a strategy that prioritizes critical UDP traffic to minimize
loss.
Option D, edge mark critical UDP traffic with AF42, is the correct answer. Assured Forwarding (AF)
classes provide a way to assign different levels of delivery assurance for IP packets. AF42 is typically
used for traffic that requires low latency and low loss, such as voice and video, which often use UDP.
Marking critical UDP traffic with AF42 will help ensure that this traffic is treated with higher priority
over the network.
Option A (edge mark lower priority TCP traffic with AF12) and Option C (edge mark lower priority
TCP traffic with AF11) suggest marking lower priority TCP traffic, which does not directly address the
concern for critical UDP traffic.
Option B (edge mark critical UDP Traffic with CS5) suggests using Class Selector 5 for critical UDP
traffic, which is also a valid approach but does not match the existing configuration that is focused on
Assured Forwarding (AF) classes.
Comments
Question 10
HOTSPOT
An administrator is creating a fabric with NetConductor in HPE Aruba Networking Central
Considering an EVPN VXLAN fabric, click on the most appropriate layer to be configured as a Rome-
Reflector Persona.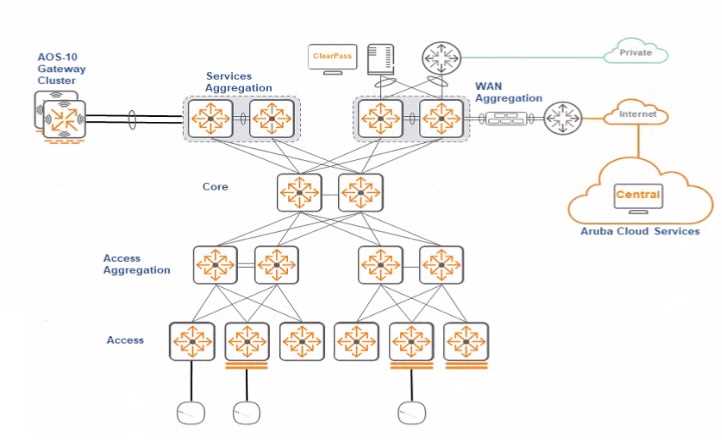
Answer:
None
Explanation:
In the context of an EVPN VXLAN fabric, the Route-Reflector Persona is most appropriately
configured at the Services Aggregation layer. This layer is responsible for interconnecting different
network services and typically includes more robust, higher-capacity devices capable of handling the
route-reflection functions for EVPN VXLAN.
In an Aruba Networks fabric, route reflectors are used to optimize the distribution of BGP routes. The
Services Aggregation layer, which is centrally located in the network topology, is best suited for this
role due to its high availability and ability to efficiently manage routes between the core and access
layers.
Therefore, if you were to click on the image provided, you would select the Services Aggregation
layer to configure the Route-Reflector Persona.
Comments
Page 1 out of 6
Viewing questions 1-10 out of 70
page 2