HP hpe6-a75 practice test
Aruba Certified Edge Professional Exam
Last exam update: Jun 27 ,2025
Question 1
Refer to the exhibit.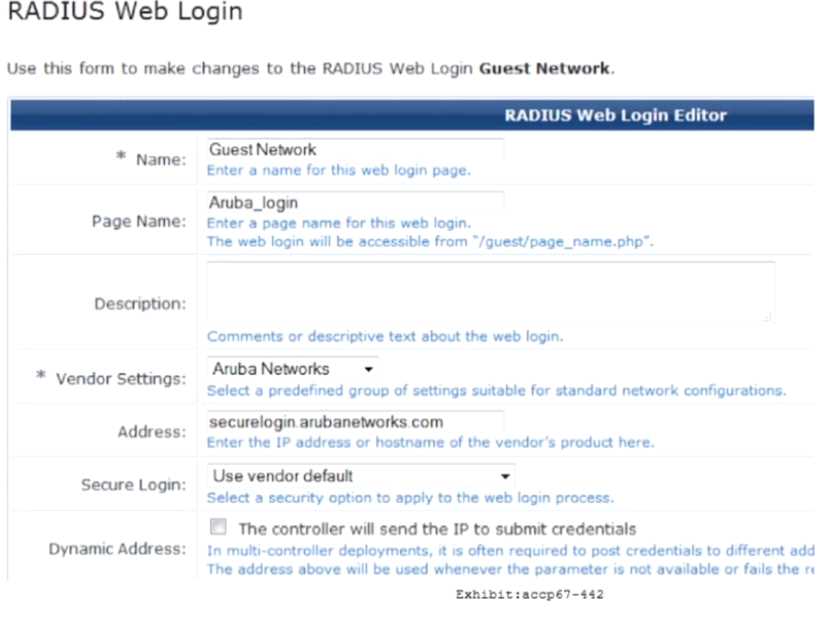
When configuring a Web Login Page in ClearPass Guest, the information shown is displayed. What is
the Address field value 'securelogin.arubanetworks.com' used for?
- A. for ClearPass to send a TACACS+ request to the NAD
- B. for appending to the Web Login URL, before the page name
- C. for the client to POST the user credentials to the NAD
- D. for ClearPass to send a RADIUS request to the NAD
- E. for appending to the Web Login URL, after the page name.
Answer:
C
Question 2
Refer to the exhibit.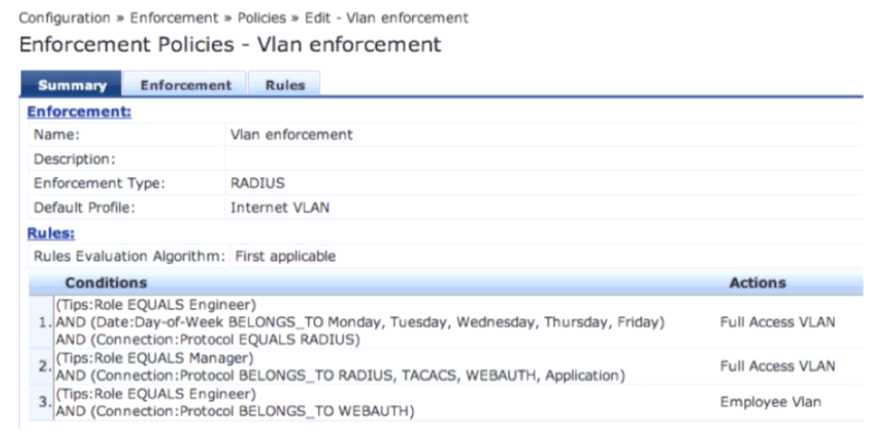
Based on the Policy configuration shown, which VLAN will be assigned when a user with ClearPass
role Engineer authenticates to the network successfully on Saturday using connection protocol
WEBAUTH?
- A. Deny Access
- B. Employee VLAN
- C. Internet VLAN
- D. Full Access VLAN
Answer:
B
Question 3
Refer to the exhibit.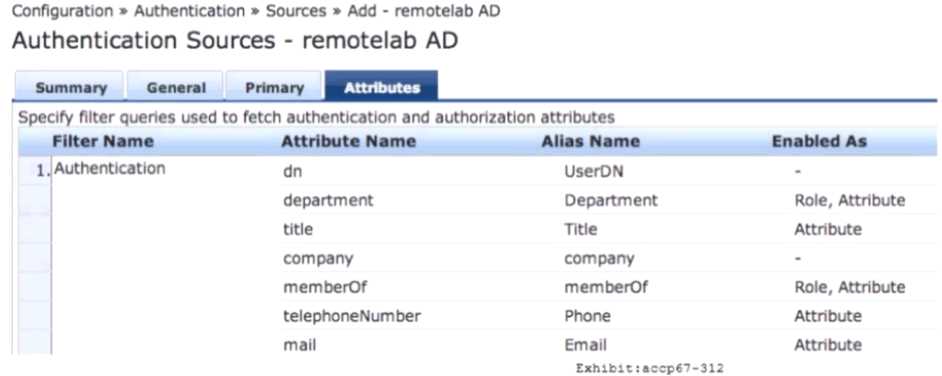
Based on the Attribute configuration shown, which statement accurately describes the status of
attribute values?
- A. Only the attribute values of department and memberOf can be used in role mapping policies.
- B. The attribute values of department, title, memberOf, telephoneNumber, and mail are directly applied as ClearPass.
- C. Only the attribute value of company can be used in role mapping policies, not the other attributes.
- D. The attribute values of department and memberOf are directly applied as ClearPass roles.
- E. Only the attribute values of title, telephoneNumber, and mail can be used in role mapping policies.
Answer:
D
Question 4
A customer wants to implement Virtual IP redundancy, such that in case of a ClearPass server
outage, 802.1x authentications will not be interrupted. The administrator has enabled a single
Virtual IP address on two ClearPass servers.
Which statements accurately describe next steps? (Select two.)
- A. The NAD should be configured with the primary node IP address for RADIUS authentication on the 802.1x network.
- B. A new Virtual IP address should be created for each NAD.
- C. Both the primary and secondary nodes will respond to authentication requests sent to the Virtual IP address when the primary node is active.
- D. The primary node will respond to authentication requests sent to the Virtual IP address when the primary node is active.
- E. The NAD should be configured with the Virtual IP address for RADIUS authentications on the 802.1x network.
Answer:
D,E
Question 5
Which statement is true about the Endpoint Profiler? (Select two.)
- A. The Endpoint Profiler uses DHCP fingerprinting for device categorization.
- B. Data obtained from the Endpoint Profiler can be used in Enforcement Policy.
- C. Endpoint Profiler requires a profiling license.
- D. The Endpoint Profiler requires the Onboard license to be enabled.
- E. The Endpoint Profiler can only categorize laptops and desktops.
Answer:
AB
Question 6
Refer to the exhibit.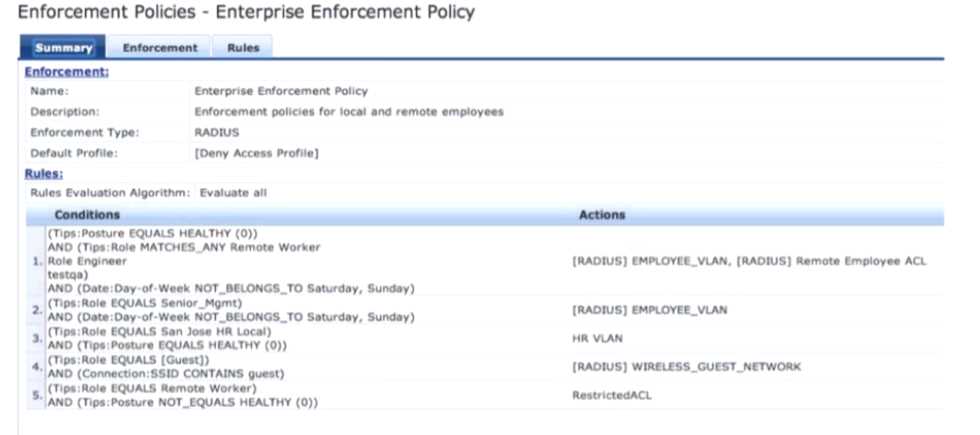
Based on the Enforcement Policy configuration, when a user with Role Engineer connects to the
network and the posture token assigned is Unknown, which Enforcement Profile will be applied?
- A. EMPLOYEE_VLAN
- B. RestrictedACL
- C. Deny Access Profile
- D. HR VLAN
- E. Remote Employee ACL
Answer:
C
Question 7
Refer to the exhibit.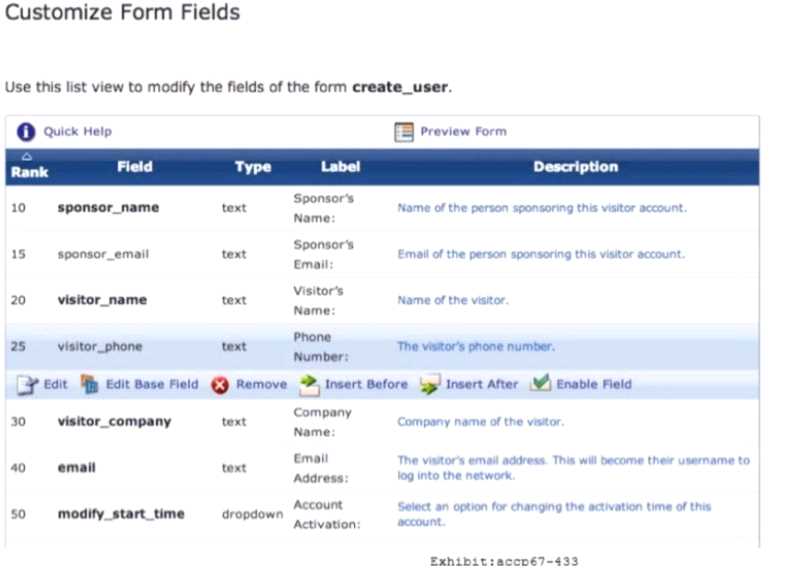
Based on the configuration of me create_user form shown, which statement accurately describes the
status?
- A. The email field will be visible to guest users when they access the web login page.
- B. The visitor_company field will be visible to operators creating the account.
- C. The visitor_company field will be visible to the guest users when they access the web login page.
- D. The visitor_phone field will be visible to the guest users in the web login page.
- E. The visitor_phone field will be visible to operators creating the account.
Answer:
A
Question 8
Refer to the exhibit.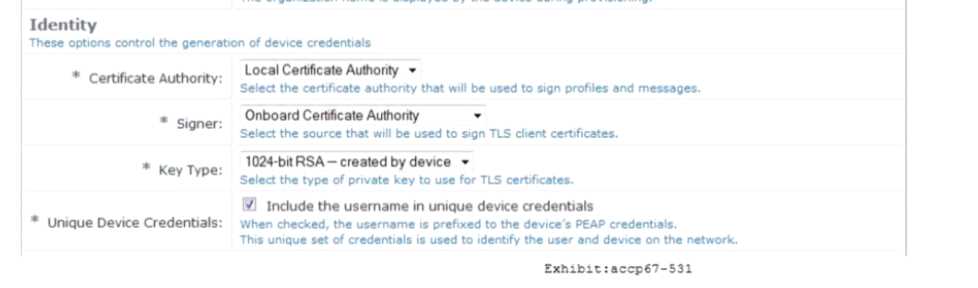
Based on the configuration for the client's certificate private key as shown, which statements
accurately describe the settings? (Select two.)
- A. More bits in the private key will increase security.
- B. The private key for TLS client certificates is not created.
- C. The private key is stored in the ClearPass server.
- D. More bits in the private key will reduce security.
- E. The private key is stored in the user device.
Answer:
AE
Question 9
Refer to the exhibit.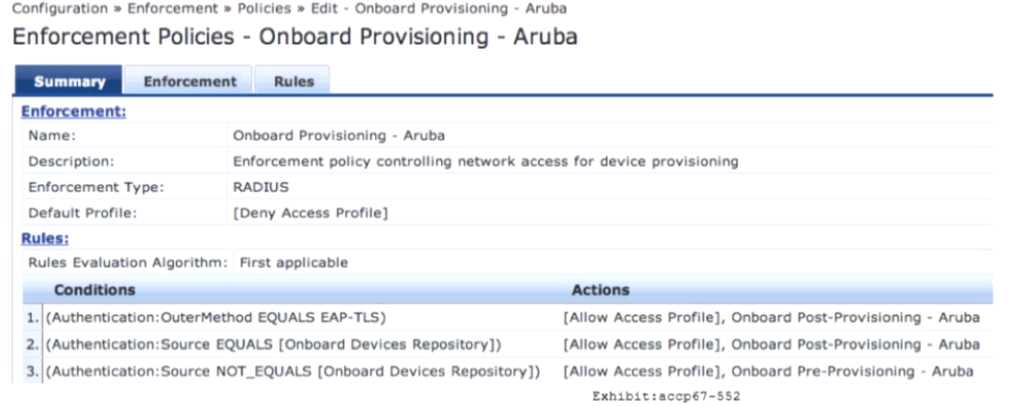
An employee connects a corporate laptop to the network and authenticates for the first time using
EAP-TLS. Based on the Enforcement Policy configuration shown, which Enforcement Profile wilt be
sent?
- A. Deny Access Profile
- B. Onboard Post-Provisioning - Aruba
- C. Onboard Device Repository
- D. Onboard Pre-Provisioning - Aruba
Answer:
D
Question 10
Refer to the exhibit.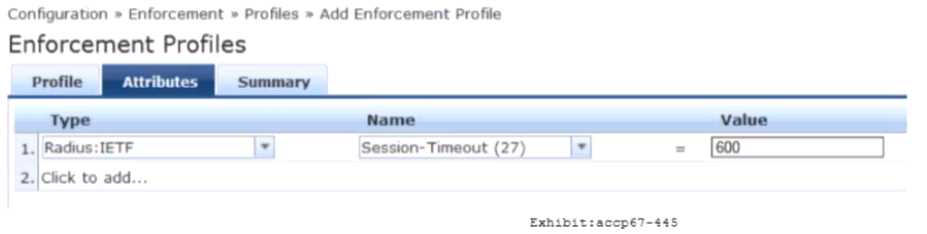
An Enforcement Profile has been created in the Policy Manager as shown. Which action will
ClearPass take based on this Enforcement Profile?
- A. ClearPass will count down 600 seconds and send a RADIUS CoA message to the user to end the users session after this time is up.
- B. ClearPass will send the Session-Timeout attribute in the RADIUS Access-Accept packet to the NAD and the NAD will end the users session after 600 seconds.
- C. ClearPass will count down 600 seconds and send a RADIUS CoA message to the NAD to end the users session after this time is up.
- D. ClearPass will send the Session-Timeout attribute in the RADIUS Access-Request packet to the NAD and the NAD will end the users session after 600 seconds.
- E. ClearPass will send the Session-Timeout attribute in the RADIUS Access-Accept packet to the User and the users session will be terminated after 600 seconds.
Answer:
B
Question 11
Refer to the exhibit.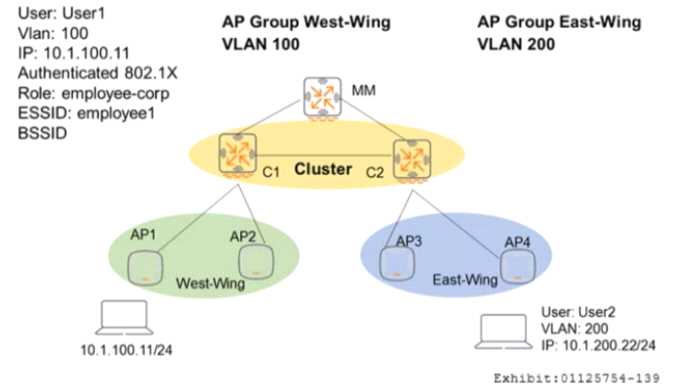
Controllers are configured m a cluster as shown in the exhibit. These are the network details.
A Mobility Master (MM) manages the cluster.
The cluster contains two controllers: C l and C2.
API and AP2 use CI as their Active AP Anchor Controller (A-AAC). with C2 as their Standby AAC (S-
AAC).
AP3 and AP4 use C2 as their A-AAC, with CI as their S-AAC.
User1 establishes a wireless connection via API, where the Active User Anchor Controller (A-UAC)
assigned is CI. with C2 as the standby. What happens when User I roams the wireless network and
eventually their session is handled by AP3?
- A. The AP3’s A-AAC switches to C1, and the user’s A-UAC remains on C1.
- B. The AP3’s A-AAC switches to C2, and the user’s A-UAC remains on C2.
- C. The AP3’s A-AAC switches to C1, and the user’s A-UAC remains on C2.
- D. The AP3’s A-AAC switches to C2, and the user’s A-UAC remains on C1.
Answer:
B
Question 12
Which ArubaOS CLl command can an administrator execute to determine if AP load balancing is
enabled in a cluster?
- A. show switches
- B. show lc-cluster group-membership
- C. show aaa cluster essid
- D. show ap active
Answer:
B
Question 13
An administrator needs to authenticate users connected to an ArubaOS Switch where the switch
authenticates the user, assigns the firewall policies to the user, and processes some of the users'
traffic. Which connection method should the administrator configure on the ArubaOS-Switch?
- A. Per-user tunneled node
- B. Split-tunneled mode
- C. Per-port tunneled node
- D. VLAN tunneled mode
Answer:
C
Question 14
Which protocol do Mobility Controllers (MCs) use to detect a failed Mobility Master (MM)?
- A. VRRP
- B. SNMP
- C. PAPI
- D. IPSec
Answer:
B
Question 15
in a VPN that uses certificate-based authentication, which component must be configured on the
Mobility Master (MM) to allow a RAP to successfully connect to a Mobility Controller (MC)
- A. RAP VPN username and password
- B. WLAN and new RAP group
- C. RAP IPSec pre-shared key
- D. RAP whitelist
Answer:
D