Question 1
How is voice traffic prioritized correctly on AOS-CX switches?
- A. By defining device profiles with QOS settings
- B. By placing it in the strict priority queue
- C. By implementing voice VLANs
- D. By implementing weighted fair queueing (WFQ)
Answer:
B
Comments
Question 2
An administrator is replacing the current access switches with AOS-CX switches. The access layer
switches
must authenticate user and networking devices connecting to them. Some devices support no form
of
authentication, and some support 802.1X. Some ports have a VoIP phone and a PC connected to the
same
port, where the PC is connected to the data port of the phone and the phone’s LAN port is connected
to the switch.
Which statement is correct about this situation?
- A. 802.1X must be configured to work in fallback mode
- B. Device fingerprinting is required for authentication
- C. The client-limit setting for port access needs to be changed
- D. Device mode should be implemented
Answer:
C
Explanation:
fallback mode if for the radius part; client limit is for multiple authent on one port (ie phone + pc)
From doc :
aaa port-access authenticator <port-list> client-limit <1-32>
Used after executing aaa port-access authenticator <port-list> to convert authentication from port-
based to user-based. Specifies user-based 802.1X authentication and the maximum number of
802.1X-authenticated client sessions allowed on each of the ports in <port-list>. If a port currently
has no authenticated client sessions, the next authenticated client session the port accepts
determines the untagged VLAN membership to which the port is assigned during the session. If
another client session begins later on the same port while an earlier session is active, the later
session will be on the same untagged VLAN membership as the earlier session.
Comments
Question 3
Examine the network exhibit.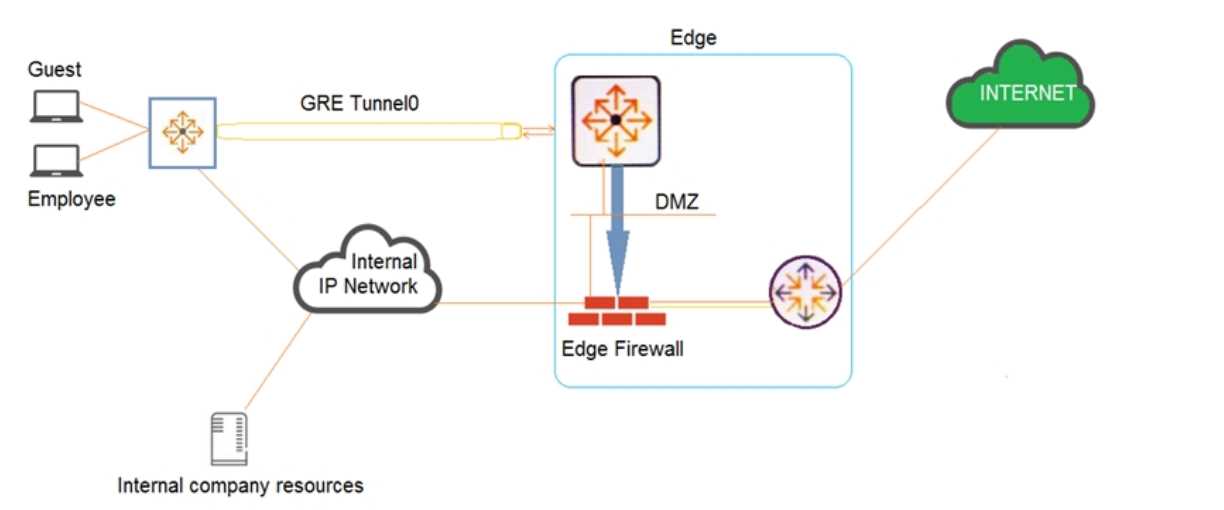
A company has a guest implementation for wireless and wired access. Wireless access is
implemented
through a third-party vendor. The company is concerned about wired guest traffic traversing the
same network as the employee traffic. The network administrator has established a GRE tunnel
between AOS-CX switches where guests are connected to a routing switch in the DMZ.
Which feature should the administrator implement to ensure that the guest traffic is tunneled to the
DMZ while the employee traffic is forwarded using OSPF?
- A. OSPF route maps using the “set metric” command
- B. Policy-based routing (PBR)
- C. User-based tunneling (UBT)
- D. Classifier policies
Answer:
B
Explanation:
Guest traffic can be routed with PBR to use GRE tunnels that terminate in the DMZ.
Comments
Question 4
An administrator has an AOS-CX switch configured with:
router ospf 1
area 0
area 1 stub no-summary
It is the only ABR for area 1. The switch has the appropriate adjacencies to routing switches in areas 0
and 1.
The current routes in each area are:
Area 0: 5 routes (LSA Type 1 and 2)
Area 1: 10 routes (LSA Type 1 and 2)
External routes: 2 (LSA Type 5)
Based on the above configuration, how many OSPF routes will routing switches see in Area 1?
- A. 15
- B. 6
- C. 11
- D. 12
Answer:
C
Comments
Question 5
A network administrator is managing a network that deploys a multicast service. The administrator
has
multiple streams successfully being routed by PIM-DM in the network. The administrator then adds a
new stream with a destination address of 239.0.0.1. However, clients who have not joined the
stream are receiving it.
What should the administrator do to fix this problem?
- A. Verify that IGMP is enabled between the switches connecting the multicast source and receivers
- B. Change the destination multicast address to 239.1.1.1
- C. Define the 239.0.0.1 stream on the rendezvous point (RP)
- D. Define the 239.0.0.1 stream on the PIM candidate bootstrap router
Answer:
B
Explanation:
MAC/IP overlap. 239.0.0.1 would be the same MAC for 224.0.0.1. 224.0.0.0/24 is always flooded
over every port.
Comments
Question 6
Which protocols are used by NetEdit to interact with third-party devices? (Choose two.)
- A. telnet
- B. SNMP
- C. SSH
- D. Restful API
- E. CDP
Answer:
B, C
Comments
Question 7
An administrator is implementing a downloadable user role solution involving AOS-CX switches. The
AAA
solution and the AOS-CX switches can successfully authenticate users; however, the role information
fails to
download to the switches. What policy should be added to an intermediate firewall to allow the
downloadable
role function to succeed?
- A. Allow TCP 443
- B. Allow UDP 1811
- C. Allow UDP 8211
- D. Allow TCP 22
Answer:
A
Explanation:
pg 681 from the Aruba guide - "When using DUR, the ClearPass HPE-CPPM-Role VSA is used in
combination with HTTPS to transfer the role to the switch." UDP 8211 (PAPI) is related to dynamic
segmentation and the communication to the MC not DUR.
Comments
Question 8
A network administrator is attempting to troubleshoot a connectivity issue between a group of users
and a
particular server. The administrator needs to examine the packets over a period of time from their
desktop;
however, the administrator is not directly connected to the AOS-CX switch involved with the traffic
flow.
What is correct regarding the ERSPAN session that needs to be established on an AOS-CX switch?
(Choose two.)
- A. On the source AOS-CX switch, the destination specified is the switch to which the administrator’s desktop is connected
- B. On the source AOS-CX switch, the destination specified is the administrator’s desktop
- C. The encapsulation protocol used is GRE
- D. The encapsulation protocol used is VXLAN
- E. The encapsulation protocol is UDP
Answer:
A, C
Explanation:
In AOS CX the remote mirroring is done using a tunnel interface, so the Mirror source and destination
must be configured on each Switch. On the source Switch, the source interface (from where the
traffic is mirrored) and destination interface (the tunnel interface to where the traffic is sent to). In
the destination Switch, the source interface (which would be the tunnel interface (receiving the
traffic from the source switch tunnel)) and the destination would be the client where Wireshark
enabled client is connected.
Comments
Question 9
What is correct regarding the operation of VSX and multicasting with PIM-SM routing configured?
- A. Each VSX peers runs PIM and builds its own group database. One of the VSX peers is elected as the designated router (DR) to forward multicast streams to a receiver VLAN
- B. Each VSX peers runs PIM and creates a shared group database. Both VSX peers can forward multicast streams to receivers in a VLAN, achieving load sharing
- C. Each VSX peers runs PIM and builds its own group database. Both VSX peers can forward multicast streams to receivers in a VLAN, achieving load sharing
- D. Each VSX peers runs PIM and creates a shared group database. One of the VSX peers is elected as the designated router (DR) to forward multicast streams to a receiver VLAN
Answer:
A
Explanation:
"both VSX switches as a PIM Designate Router (DR). One node is the actual DR, the other node is the
proxy DR." "Only the actual DR performs multicast routing and forward traffic destined to groups to
its downstream VLANs in the data-path."
https://www.arubanetworks.com/techdocs/AOS-
CX/10.07/HTML/5200-7888/Content/Chp_Pre_tra_loss/ip-mul-rou-10.htm
Comments
Question 10
An administrator wants to track what configuration changes were made on a switch. What should the
administrator implement to see the configuration changes on an AOS-CX switch?
- A. AAA authorization
- B. Network Analysis Engine (NAE)
- C. AAA authentication
- D. VSX synchronization logging
Answer:
B
Comments
Page 1 out of 12
Viewing questions 1-10 out of 127
page 2