Question 1
Which of the following is a standard Unix command that would most likely be used to copy raw file
system data for later forensic analysis?
- A. dd
- B. backup
- C. cp
- D. gzip
Answer:
A
Comments
Question 2
Which of the following is NOT a recommended best practice for securing Terminal Services and
Remote Desktop?
- A. Require TLS authentication and data encryption whenever possible.
- B. Make sure to allow all TCP 3389 traffic through the external firewall.
- C. Group Policy should be used to lock down the virtual desktops of thin-client users.
- D. Consider using IPSec or a VPN in addition to the RDP encryption if you are concerned about future RDP vulnerabilities.
Answer:
B
Comments
Question 3
When an IIS filename extension is mapped, what does this mean?
- A. Files with the mapped extensions cannot be interpreted by the web server.
- B. The file and all the data from the browser's request are handed off to the mapped interpreter.
- C. The files with the mapped extensions are interpreted by CMD.EXE.
- D. The files with the mapped extensions are interpreted by the web browser.
Answer:
B
Comments
Question 4
Which Linux file lists every process that starts at boot time?
- A. inetd
- B. netsrv
- C. initd
- D. inittab
Answer:
D
Comments
Question 5
When trace route fails to get a timely response for a packet after three tries, which action will it take?
- A. It will print '* * *' for the attempts and increase the maximum hop count by one.
- B. It will exit gracefully, and indicate to the user that the destination is unreachable.
- C. It will increase the timeout for the hop and resend the packets.
- D. It will print '* * *' for the attempts, increment the TTL and try again until the maximum hop count.
Answer:
D
Comments
Question 6
You are examining an IP packet with a header of 40 bytes in length and the value at byte 0 of the
packet header is 6. Which of the following describes this packet?
- A. This is an IPv4 packet; the protocol encapsulated in the payload is unspecified.
- B. This is an IPv4 packet with a TCP payload.
- C. This is an IPv6 packet; the protocol encapsulated in the payload is unspecified.
- D. This is an IPv6 packet with a TCP payload.
Answer:
C
Comments
Question 7
Which of the following is a valid password for a system with the default "Password must meet
complexity requirements" setting enabled as part of the GPO Password policy requirements?
- A. The Cat Chased its Tail AII Night
- B. disk ACCESS failed
- C. SETI@HOME
- D. SaNS2006
Answer:
D
Comments
Question 8
At what point in the Incident Handling process should an organization determine its approach to
notifying law enforcement?
- A. When performing analysis
- B. When preparing policy
- C. When recovering from the incident
- D. When reacting to an incident
Answer:
D
Comments
Question 9
Which of the following is TRUE regarding the ability of attackers to eavesdrop on wireless
communications?
- A. Eavesdropping attacks cannot be performed through concrete walls.
- B. Eavesdropping attacks can take place from miles away.
- C. Eavesdropping attacks are easily detected on wireless networks.
- D. Eavesdropping attacks require expensive devices.
Answer:
B
Comments
Question 10
An employee is currently logged into the corporate web server, without permission. You log into the
web server as 'admin" and look for the employee's username: "dmaul" using the "who" command.
This is what you get back: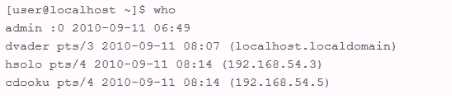
- A. The contents of the /var/log/messages file has been altered
- B. The contents of the bash history file has been altered
- C. The contents of the utmp file has been altered
- D. The contents of the http logs have been altered
Answer:
B
Comments
Page 1 out of 38
Viewing questions 1-10 out of 385
page 2