Question 1
David works as the Security Manager for ABC Inc. He has been assigned a project to detect the
attacks over multiple connections and sessions and to count the number of scanned ports in a
defined time period.
Which of the following rulebases will he use to accomplish the task?
- A. SYN Protector rulebase
- B. Exempt rulebase
- C. Traffic Anomalies rulebase
- D. Network Honeyport rulebase
Answer:
C
Comments
Question 2
Which of the following terms is used to represent IPv6 addresses?
- A. Colon-dot
- B. Dot notation
- C. Hexadecimal-dot notation
- D. Colon-hexadecimal
Answer:
D
Comments
Question 3
You work as a Security Administrator for ABC Inc. You have implemented and configured a web
application security scanner in the company's network. It helps in the automated review of the web
applications with the defined purpose of discovering security vulnerabilities. In order to perform this
task, the web application security scanner examines a number of vulnerabilities.
What are these vulnerabilities?
Each correct answer represents a complete solution. (Choose three.)
- A. Input/Output validation
- B. Denials of service against the TCP/IP stack
- C. Server configuration mistakes/errors/version
- D. Specific application problems
Answer:
A,C,D
Comments
Question 4
Which of the following information must the fragments carry for the destination host to reassemble
them back to the original unfragmented state?
Each correct answer represents a complete solution. (Choose all that apply.)
- A. Offset field
- B. MF flag
- C. Length of the data
- D. IP identification number
- E. IP address
- F. MAC address
Answer:
A,B,C,D
Comments
Question 5
Which of the following types of IP actions are supported by an IDP rulebase? (Choose three.)
- A. Initiate rules of the rulebase
- B. Notify
- C. Drop/block session
- D. Close connection
Answer:
B,C,D
Comments
Question 6
You work as a Network Administrator for ABC Inc. You want to configure Snort as an IDS for your
company's wireless network, but you are concerned that Snort does not support all types of traffic.
What traffic does Snort support?
Each correct answer represents a complete solution. (Choose all that apply.)
- A. ICMP
- B. UDP
- C. TCP
- D. IP
Answer:
A,B,C,D
Comments
Question 7
Which of the following parts of IP header is used to specify the correct place of the fragment in the
original un-fragmented datagram?
- A. Fragment offset
- B. TTL
- C. Source address
- D. Fragment ID
Answer:
A
Comments
Question 8
An attacker changes the address of a sub-routine in such a manner that it begins to point to the
address of the malicious code. As a result, when the function has been exited, the application can be
forced to shift to the malicious code. The image given below explains this phenomenon: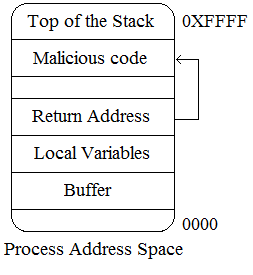
Which of the following tools can be used as a countermeasure to such an attack?
- A. SmashGuard
- B. Obiwan
- C. Kismet
- D. Absinthe
Answer:
A
Comments
Question 9
Which of the following forms on NAT maps multiple unregistered IP addresses to a single registered
IP address by using different ports?
- A. Overclocking
- B. Dynamic NAT
- C. Overloading
- D. Static NAT
Answer:
C
Comments
Question 10
Which of the following tools is used to detect wireless LANs using the 802.11b, 802.11a, and 802.11g
WLAN standards on the Windows platform?
- A. Snort
- B. NetStumbler
- C. AiroPeek
- D. Cain
Answer:
B
Comments
Page 1 out of 28
Viewing questions 1-10 out of 285
page 2