Question 1
What type of Unified Modelling Language (UML) diagram is used to show dependencies between
logical groupings in a system?
- A. Package diagram
- B. Deployment diagram
- C. Class diagram
- D. Use case diagram
Answer:
A
Comments
Question 2
IDS alerts at Service Industries are received by email. A typical day process over 300 emails with
fewer than 50 requiring action. A recent attack was successful and went unnoticed due to the
number of generated alerts. What should be done to prevent this from recurring?
- A. Tune the IDS rules to decrease false positives.
- B. Increase the number of staff responsible for processing IDS alerts.
- C. Change the alert method from email to text message.
- D. Configure the IDS alerts to only alert on high priority systems.
Answer:
A
Comments
Question 3
Janice is auditing the perimeter of the network at Sugar Water InC. According to documentation,
external SMTP traffic is only allowed to and from 10.10.10.25. Which of the following actions would
demonstrate the rules are configured incorrectly?
- A. Receive spam from a known bad domain
- B. Receive mail at Sugar Water Inc. account using Outlook as a mail client
- C. Successfully deliver mail from another host inside the network directly to an external contact
- D. Successfully deliver mail from web client using another host inside the network to an external contact.
Answer:
C
Comments
Question 4
Which of the following should be used to test antivirus software?
- A. FIPS 140-2
- B. Code Red
- C. Heartbleed
- D. EICAR
Answer:
D
Comments
Question 5
Which of the following is necessary to automate a control for Inventory and Control of Hardware
Assets?
- A. A method of device scanning
- B. A centralized time server
- C. An up-to-date hardening guide
- D. An inventory of unauthorized assets
Answer:
A
Comments
Question 6
Which of the following CIS Controls is used to manage the security lifecycle by validating that the
documented controls are in place?
- A. Controlled Use of Administrative Privilege
- B. Account Monitoring and Control
- C. Data Protection
- D. Penetration Tests and Red Team Exercises
Answer:
D
Comments
Question 7
When evaluating the Wireless Access Control CIS Control, which of the following systems needs to be
tested?
- A. Log management system
- B. 802.1x authentication systems
- C. Data classification and access baselines
- D. PII data scanner
Answer:
B
Comments
Question 8
As part of an effort to implement a control on E-mail and Web Protections, an organization is
monitoring their webserver traffic. Which event should they receive an alert on?
- A. The number of website hits is higher that the daily average
- B. The logfiles of the webserver are rotated and archived
- C. The website does not respond to a SYN packet for 30 minutes
- D. The website issues a RST to a client after the connection is idle
Answer:
C
Comments
Question 9
Which of the following items would be used reactively for incident response?
- A. A schedule for creating and storing backup
- B. A phone tree used to contact necessary personnel
- C. A script used to verify patches are installed on systems
- D. An IPS rule that prevents web access from international locations
Answer:
B
Comments
Question 10
Below is a screenshot from a deployed next-generation firewall. These configuration settings would
be a defensive measure for which CIS Control?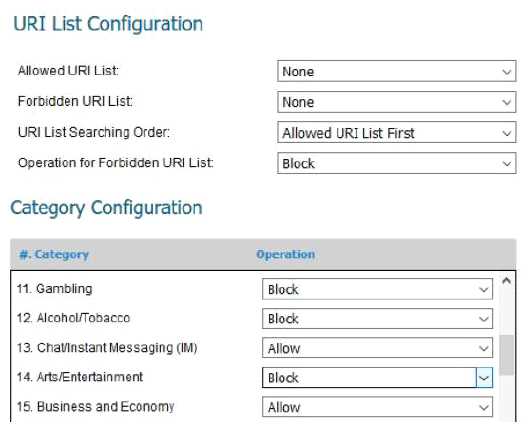
- A. Controlled Access Based on the Need to Know
- B. Limitation and Control of Network Ports, Protocols and Services
- C. Email and Web Browser Protections
- D. Secure Configuration for Network Devices, such as Firewalls, Routers and Switches.
Answer:
C
Comments
Page 1 out of 9
Viewing questions 1-10 out of 93
page 2