Question 1
Which of the following is required in addition to the Apple ID of the custodian to access IOS backup
files that are stored in ICloud?
A. iTunes password
B. Device passcode
C. Manifest.plist
D. Keychain-backup.plist
Answer:
B
Explanation
Comments
Question 2
In 2015, Apple’s iTunes store was found to be hosting several malicious applications that were
infected as a result of hacked version of the developer toolkit used to create applications. Which
Apple developer suite was targeted?
A. Xcode
B. ADB
C. Momentics IDE
D. Xamarin
Answer:
A
Explanation
Reference:
http://money.cnn.com/2015/09/21/technology/apple-xcode-hack/index.html
Comments
Question 3
An Android device user is known to use Facebook to communicate with other parties under
examination.
There is no evidence of the Facebook application on the phone. If there was Facebook usage where
would an examiner expect to find these artifacts?
A. com.android.chrome/app_chrome/Default/Local Storage
B. dmappmgr.db
C. /data/system/packages.xml
D. AndroidManifest.xml
Answer:
B
Explanation
Reference:
https://www.ctsforensics.com/assets/news/35550_Web-update.pdf
Comments
Question 4
Physical Analyzer provides a function to narrow down a search based on a timestamp, a type, a party
or date.
What is the name of this advanced searching capability?
A. Watchlist Editor
B. Tags
C. Timeline
D. Event of Interest
Answer:
C
Explanation
Explanation: Physical Analyzer offers the Timeline feature to narrow down what happened on the
smartphone during a specific time, type, party, etc. This is commonly used to narrow down time
periods. Data that is manually carved will not be shown here. There is also an option to create a
custom timeline specification.
Comments
Question 5
The files pictured below from a BlackBerry OS10 file system have a unique file extension.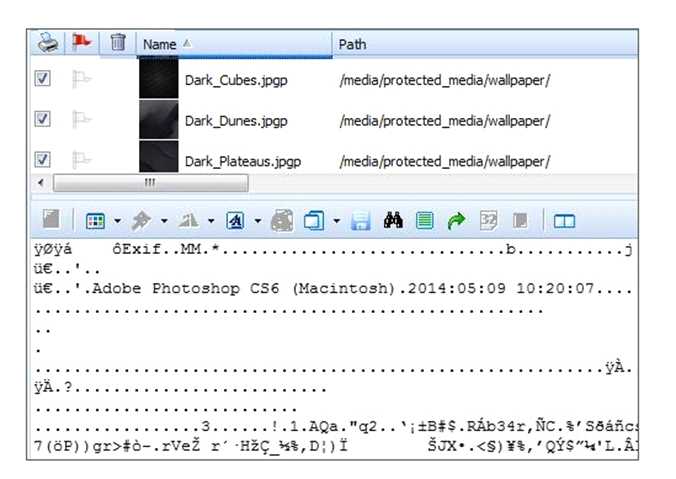
What can be concluded about these files?
A. Files are protected by the file system, so changing the file system makes them less accessible
B. Files are encrypted to prevent them from being viewed without the decryption key
C. Files are encoded for secure transmitting of data
D. Files are located on a media card so they contain a unique file extension
Answer:
A
Explanation
Reference:
https://forums.crackberry.com/blackberry-q10-f272/protected-media-911023/
Comments
Question 6
Exhibit: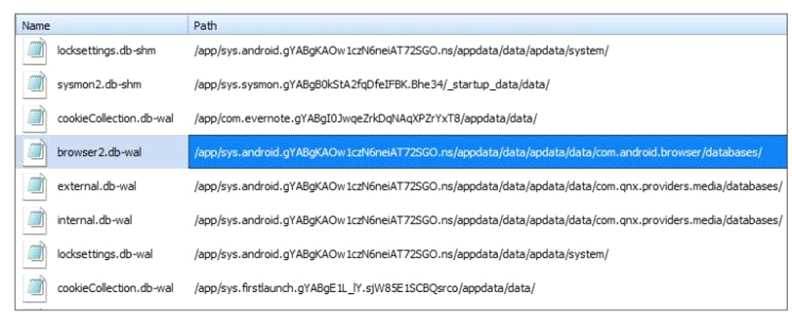
Where can an analyst find data to provide additional artifacts to support the evidence in the
highlighted file?
- A. internal.db-wal
- B. browser2.db
- C. sysmon2.db-shm
- D. external.db
Answer:
A
Comments
Question 7
Which of the following is a unique 56 bit number assigned to a CDMA handset?
A. Mobile Station International Subscriber Directory Number (MSISDN)
B. Electronic Serial Number (ESN)
C. International Mobile Equipment Identifier (IMEI)
D. Mobile Equipment ID (MEID)
Answer:
D
Explanation
Explanation: The Mobile Equipment ID (MEID), also found under the battery cover, is a 56 bit number
which
replaced the ESN due to the limited number of 32 bit ESN numbers. The MEID is listed in hex, where
the first byte is a regional code, next three bytes are a manufacturer code, and remaining three bytes
are a
manufacturer-assigned serial number.
Reference:
https://sites.google.com/site/bbayles/index/cdma_hardware_id
Comments
Question 8
Which of the following files provides the most accurate reflection of the device’s date/timestamp
related to the
last device wipe?
A. /private/var/mobile/Library/AddressBook/AddressBook.sqlitedb
B. /private/var/mobile/Applications/com.apple.mobilesafari/Library/history.db
C. /private/var/mobile/Applications/com.viber/Library/Prefernces/com.viber.plist
D. /private/var/mobile/Applications/net.whatsapp.WhatsApp/Library/pw.dat
Answer:
A
Explanation
Comments
Question 9
Which of the following is the term for the SMS malware that sends text messages to a premium
number
generating large service bills for the user of the targeted device?
A. Trojan
B. Adware
C. Potentially unwanted applications
D. Click bait
Answer:
A
Explanation
Reference:
https://pdfs.semanticscholar.org/7f33/9156f47345bd102c9b05f45f9bfe4c182720.pdf
Comments
Question 10
When examining the iOS device shown below the tool indicates that there are 4 chat messages
recovered from the device.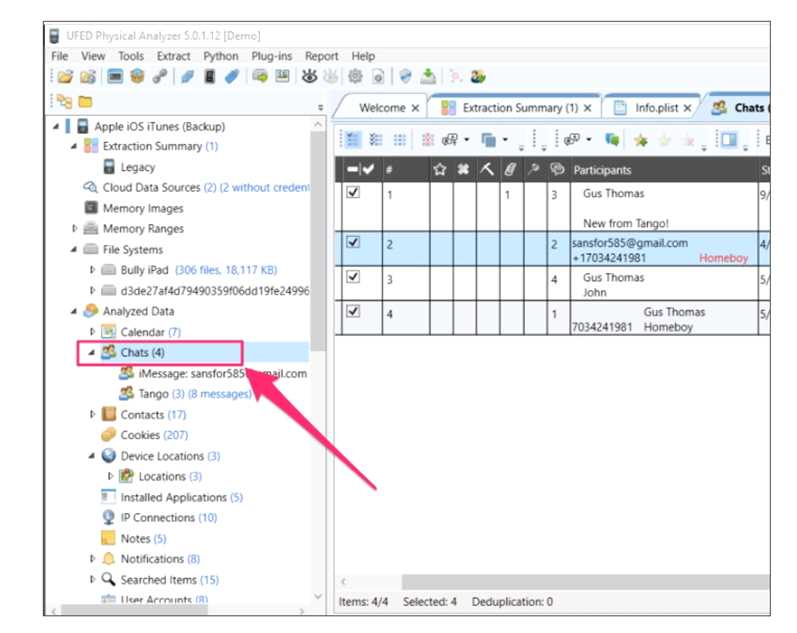
Which of the following locations may contain additional chat information?
A. Memory ranges from a physical dump of the device
B. Databases installed and maintained by the application
C. Internet history plist files found in logical acquisitions
D. IP connections used by the application
Answer:
B
Explanation
Comments
Page 1 out of 7
Viewing questions 1-10 out of 75
page 2