Fortinet nse8-811 practice test
Fortinet NSE 8 Written Exam (NSE8_811) Exam
Last exam update: Jun 29 ,2025
Question 1
Click the Exhibit button.
Central NAT was configured on a FortiGate firewall. A sniffer shows ICMP packets out to a host on the
Internet egresses with the port1 IP address instead of the virtual IP(VIP) that was configured.
Referring to the exhibit, which configuration will ensure that ICMP traffic is also translated?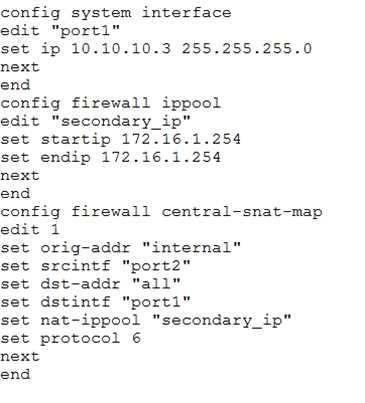
- A. config firewall ippool edit “secondry_ip” set arp-intf ‘port1’ next end
- B. config firewall central-snat-map edit 1 set protocol 1 next end
- C. config firewall central-snat-map edit 1 unset protocol next end
- D. config firewall central-snat-map edit 1 set orig-addr “all” next end
Answer:
C
Question 2
You configured a firewall policy with only a Web filter profile for accessing the Internet. Access to
websites belonging to the "Information Technology" category are blocked and to the "Business"
category are allowed. SSL deep inspection is not enabled on this policy.
A user wants to access the website
https://www.it-acme.com
which presents a certificate with
CN=www.acme.com. The it-acme.com domain is categorized as "Information Technology" and the
acme.com domain is categorized as "Business".
Which statement regarding this scenario is correct?
- A. The FortiGate is able to read the URL within HTTPS sessions when using SSL certificate inspection so the website will be blocked by the "Information Technology".
- B. The website will be blocked by category "Information Technology" as the SNI takes precedence over the certificate name.
- C. The website will be allowed by category "Business" as the certificate name takes precedence over the URL.
- D. Only with SSL deep inspection enabled will the FortiGate be able to categorized this website.
Answer:
B
Question 3
A FortOS devices is used for termination of VPNs for number of remote spoke VPN units (designated
group A spokes) using a phase 1 main mode dial-up tunnel using pre-shared. Your company recently
acquired another organization. You are asked establish VPN correctively for the newly acquired
organization's sites which new devices will be provisioned (designated Group B spokes). Both exiting
(Group A) and new (Group B) spoke units are dynamically addressed. You are asked to ensure that
spokes from the acquired organization (Group B) have different access permission than your existing
VPN spokes (Group A).
Which two solutions meet the represents for the new spoke group? (Choose two.)
- A. Implement a new phase 1 dial-up main mode tunnel with a different pre-shared key than the Group A spokes.
- B. Implement a new phase 1 dial-up main mode tunnel with certificate authentication.
- C. Implement a new phase 1 dial-up main mode tunnel with pre-shared keys and XAuth.
- D. Implement separate phase 1 dial-up aggressive mode tunnels with a distinct peer ID.
Answer:
CD
Question 4
Click the Exhibit button.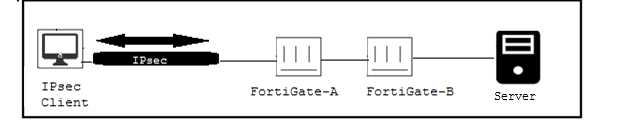
Only users authenticated in FortiGate-B can reach the server. A customer wants to deploy a single
sign-on solution for IPsec VPN users. Once a user is connected and authenticated to the VPN in
FortiGate-A, the user does not need to authenticate again in FortiGate B to reach the server.
Which two actions satisfy this requirement? (Choose two.)
- A. Use Kerberos authentication.
- B. FortiGate-A must generate a RADUIS accounting packets.
- C. Use FortiAuthenticator.
- D. Use the Collector Agent.
Answer:
BC
Question 5
Click the Exhibit button. An administrator implements a multi-chassis link aggregation (MCLAG)
solution using two FortiSwitch 448Ds and one FortiGate 3700D. As describes in the network topology
shown in the exhibit, two links are connected to each FortiSwitch. What is requires to implement this
solution? (Choose two.)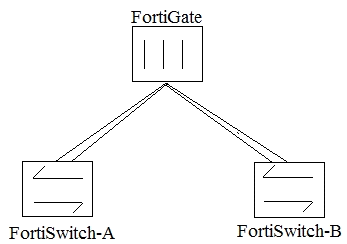
- A. Replace the FortiGate as this one does not have an ISF.
- B. Create two separate link aggregated (LAG) interfaces on the FortiGate side for each FortiSwitch.
- C. Add set fortilink-split-interface disable on the FortiLink interface.
- D. An ICL link between both FortiSwitch devices needs to be added.
Answer:
CD
Question 6
You must create a high Availability deployment with two FortiWebs in Amazon Services (AWS): each
on different Availability Zones(AZ) from the same region. At the same time, each FortiWeb should be
able to deliver content from the Web server of both of the AZs. Which deployment would will this
requirement?
- A. Configure the FortiWebs Active-Active Ha mode and use AWS Router 53 load Router balance the internal Web servers.
- B. Configure the FortiWebs in Active-Active HA mode and use AWS Elastic load Balancer (ELB) for the internal Web servers.
- C. Use AWS Router 53 to load balance FortiWebs in standone mode and use AWS Virtual private Cloud (VPC) peering to load balance the internal Web servers.
- D. Use AWS Elastic load Balancer (ELB) for both FortiWebs in standdone mode and the internal Web servers in an ELB sandwich.
Answer:
D
Explanation:
https://www.fortinet.com/content/dam/fortinet/assets/solution-guides/sb-aws-automatically-scale-
cloud-security.pdf
Question 7
You are asked to implement a single FortiGate 5000 chassis using Session-aware Load Balance Cluster
(SLBC) with Active Passive FortinControllers. Both FortiControllers have the configuration shown
below, with the rest of the configuration set to the default values:
onfig system ha
set mode dual
set password fortinetnse8
set group-id 5
set chassis-id 1
set minimize-chassis-failover enable
set hbdev b1
end
Both FortiControllers show Master status. What is the problem in this scenario?
- A. The management interface of both FotiControllers was connected on the some network.
- B. The priority should be set higher for ForControllers on slot-1.
- C. The b1 interface the two FortiConrollers do not see each other.
- D. The chassis ID settings on FotiControllers on slot 2 should be set to 2.
Answer:
C
Question 8
Click the Exhibit button.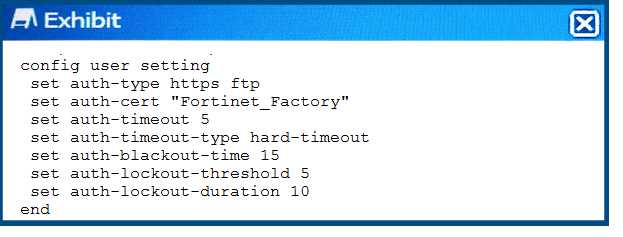
Referring to the exhibit, which two statements are true about local authentication? (Choose two.)
- A. The FortiGate will allow the TCP connection when a ClientHello message indicating a renegotiation is received.
- B. The user’s IP address will be blocked 15 seconds after five login failures.
- C. The user will be blocked 15 seconds after five login failures.
- D. The user will need to re-authenticate after five minutes.
Answer:
BD
Question 9
Exhibit
Click the Exhibit button.
You have deployed several perimeter FortiGates with internal segmentation FortiGates behind them.
All FortiGate devices are logging to FortiAnalyzer. When you search the logs in FortiAnalyzer for
denied traffic, you see numerous log messages, as shown in the exhibit, on your perimeter
FortiGates only.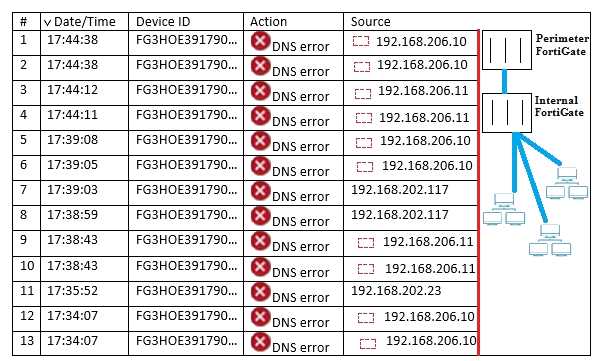
Which two actions would reduce the number of these log messages? (Choose two.)
- A. Apply an application control profile lo the perimeter FortiGates that does not inspect DNS traffic to the outbound firewall policy.
- B. Configure the internal ForbGates to communicate to ForpGuard using port 8888.
- C. Disable DNS events logging horn ForirGate In the config log fortianalyser filter section.
- D. Remove DNS signature* <rom the IPS protte appfced to the outbound firewall policy.
Answer:
BC
Explanation:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD40788
Question 10
Click the Exhibit button.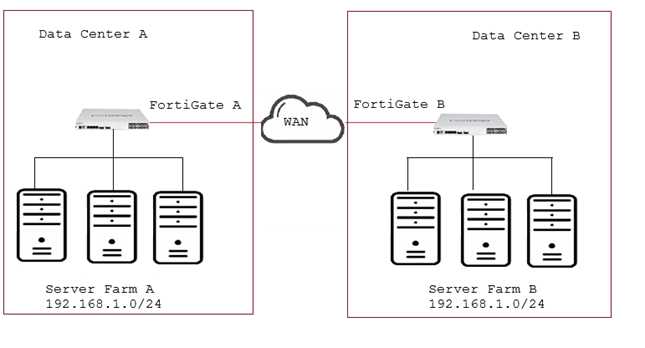
Your company has two data centers (DC) connected using a Layer 3 network. Servers in farm A need
to connect to servers in farm B as though they all were in the same Layer 2 segment. What would be
configured on the FortiGates on each DC to allow such connectivity?
- A. Create an IPsec tunnel with transport mode encapsulation.
- B. Create an IPsec tunnel with Mode encapsulation.
- C. Create an IPsec tunnel with VXLAN encapsulation.
- D. Create an IPsec tunnel with VLAN encapsulation.
Answer:
C
Explanation:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD40170
Question 11
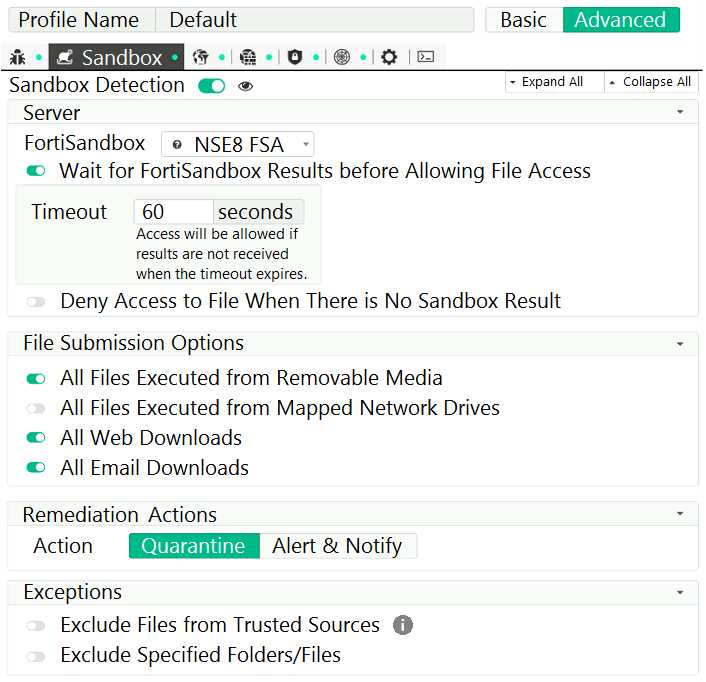
Anti-Virus Real-Time Protection is enabled without any exclusions.
Referring to the exhibit, which two behaviors will the FortiClient endpoint have after receiving the
profile update from the FortiClient EMS? (Choose two.)
- A. Access to a downloaded file will always be allowed after 60 seconds when the FortiSandbox is reachable.
- B. The user will not be able to access a downloaded file for a maximum of 60 seconds if it is not a virus and the FortiSandbox is reachable.
- C. Files executed from a mapped network drive will not be inspected by the FortiClient endpoint AntiVirus engine.
- D. If the Real-Time Protection does not detect a virus, the user will be able to access a downloaded file when the FortiSandbox is unreachable.
Answer:
BD
Explanation:
https://docs.fortinet.com/document/forticlient/6.0.0/ems-administration-guide/324667/sandbox-
detection
Question 12
FortiMail configured with the protected domain "internal lab".
Which two envelopes addresses will need an access control rule to relay e-mail sent for
unauthenticated users? (Choose two.)
- A. MAIL FROM: traming@fortinet com: RCPT TO: student@fortinet com
- B. MAIL FROM student@fortinet com: RCPT TO [email protected]
- C. MAIL FROM: trainmg@internallab; RCPT TO student@mternallab
- D. MAIL FROM student@internal lab: RCPT TO [email protected]
Answer:
AD
Explanation:
https://help.fortinet.com/fmail/5-3-6/admin/index.html#page/FortiMail_Online_Help/policy_09_10.html
Question 13
Exhibit
Click the Exhibit button.
The exhibit shows the configuration of a service protection profile (SPP) in a FortiDDoS device.
Which two statements are true about the traffic matching being inspected by this SPP? (Choose two.)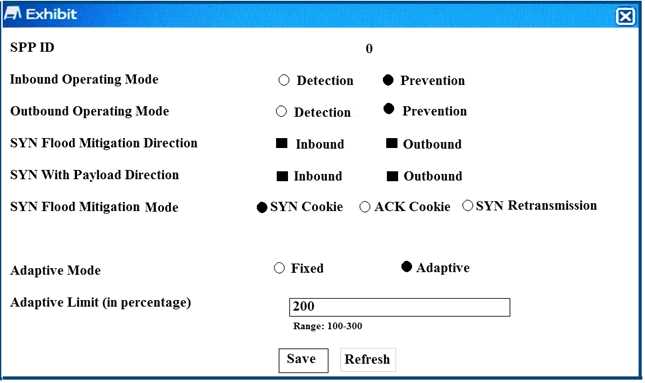
- A. Traffic that does match any spp policy will not be inspection by this spp.
- B. FortiDDos will not send a SYNACK if a SYN packet is coming from an IP address that is not the legtimate IP (LIP) address table.
- C. FortiDooS will start dropping packets as soon as the traffic executed the configured maintain threshold.
- D. SYN packets with payloads will be drooped.
Answer:
AD
Explanation:
https://help.fortinet.com/fddos/4-3-0/FortiDDoS/Configuring_SPP_settings.htm
SYN cookieSends a SYN/ACK with a cookie value in the TCP sequence field. If it receives an ACK
back with the right cookie, an RST/ACK packet is sent and the IP address is added to the legitimate IP
address table. If the client then retries, it succeeds in making a TCP connection.
So apparently, the very first SYN/ACK with a cookie value is sent when the IP address is not in the
legitimate IP address table yet.
Question 14
A company has just deployed a new FortiMail in gateway mode. The administrator is asked to
strengthen e-mail protection by applying the policies shown below.
- E-mails can only be accepted if a valid e-mail account exists.
- Only authenticated users can send e-mails out
Which two actions will satisfy the requirements? (Choose two. )
- A. Configure recipient address verification.
- B. Configure inbound recipient policies.
- C. Configure outbound recipient policies.
- D. Configure access control rules.
Answer:
AD
Question 15
Refer to the exhibit.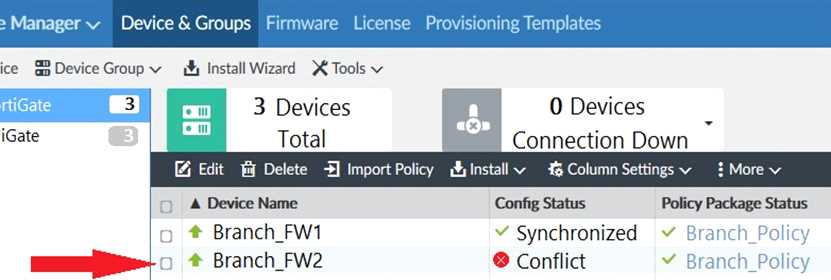
You log into FortiManager, access the Device Manager window and notice that one of the managed
devices is not in normal status.
Referring to the exhibit, which two statements correctly describe the status and result of the affected
device? (Choose two.)
- A. The device configuration was changed on the local FortiGate side only; auto-update is disabled.
- B. The changed configuration on the FortiGate will remain the next time that the device configuration is pushed from FortiManager.
- C. The device configuration was changed on both the local FortiGate side and the FortiManager side; autoupdate is disabled.
- D. The changed configuration on the FortiGate will be overwritten in favor of what is on the FortiManager the next time that the device configuration is pushed.
Answer:
CD