Question 1
How can you achieve remote access and internet availability in an OT network?
- A. Create a back-end backup network as a redundancy measure.
- B. Implement SD-WAN to manage traffic on each ISP link.
- C. Add additional internal firewalls to access OT devices.
- D. Create more access policies to prevent unauthorized access.
Answer:
B
Comments
Question 2
What are two critical tasks the OT network auditors must perform during OT network risk assessment
and management? (Choose two.)
- A. Planning a threat hunting strategy
- B. Implementing strategies to automatically bring PLCs offline
- C. Creating disaster recovery plans to switch operations to a backup plant
- D. Evaluating what can go wrong before it happens
Answer:
A,C
Comments
Question 3
What is the primary objective of implementing SD-WAN in operational technology (OT) networks'?
- A. Reduce security risk and threat attacks
- B. Remove centralized network security policies
- C. Enhance network performance of OT applications
- D. Replace standard links with lower cost connections
Answer:
C
Comments
Question 4
Refer to the exhibit.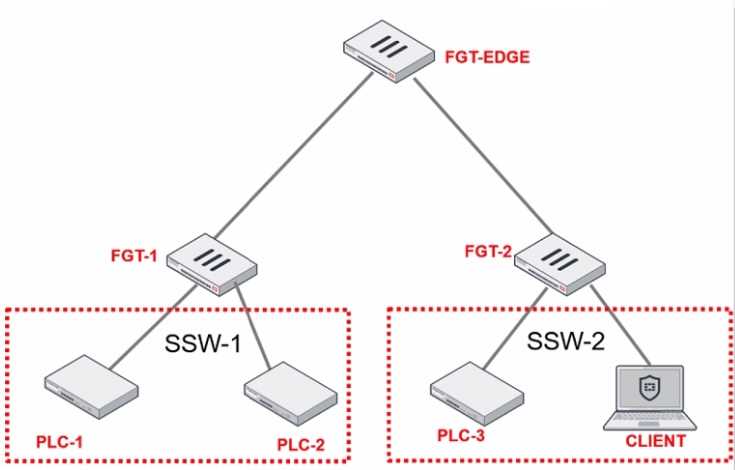
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1)
connecting both PLC-3 and CLIENT. PLC-3 and CLIENT cannot send traffic to each other.
Which two statements about the traffic between PCL-1 and PLC-2 are true? (Choose two.)
- A. The switch on FGT-2 must be hardware to implement micro-segmentation.
- B. Micro-segmentation on FGT-2 prevents direct device-to-device communication.
- C. Traffic must be inspected by FGT-EDGE in OT networks.
- D. FGT-2 controls intra-VLAN traffic through firewall policies.
Answer:
B,D
Comments
Question 5
An OT network consists of multiple FortiGate devices. The edge FortiGate device is deployed as the
secure gateway and is only allowing remote operators to access the ICS networks on site.
Management hires a third-party company to conduct health and safety on site. The third-party
company must have outbound access to external resources.
As the OT network administrator, what is the best scenario to provide external access to the third-
party company while continuing to secure the ICS networks?
- A. Configure outbound security policies with limited active authentication users of the third-party company.
- B. Create VPN tunnels between downstream FortiGate devices and the edge FortiGate to protect ICS network traffic.
- C. Split the edge FortiGate device into multiple logical devices to allocate an independent VDOM for the third-party company.
- D. Implement an additional firewall using an additional upstream link to the internet.
Answer:
C
Comments
Question 6
Refer to the exhibit.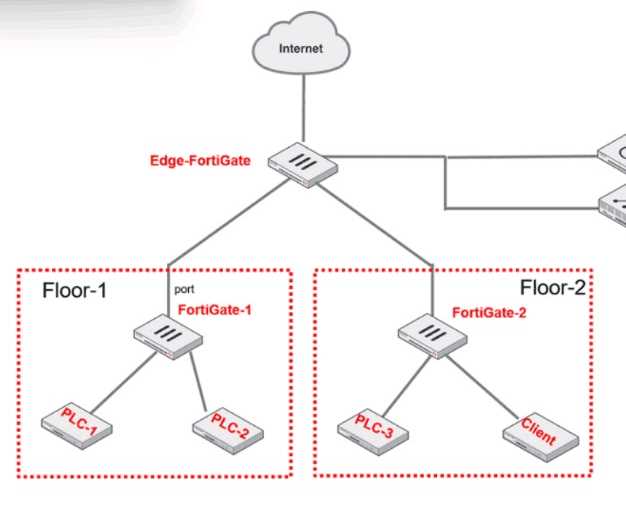
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1)
connecting both PLC-3 and CLIENT. PLC-3 and CLIENT can send traffic to each other at the Layer 2
level.
What must the OT admin do to prevent Layer 2-level communication between PLC-3 and CLIENT?
- A. Set a unique forward domain for each interface of the software switch.
- B. Create a VLAN for each device and replace the current FGT-2 software switch members.
- C. Enable explicit intra-switch policy to require firewall policies on FGT-2.
- D. Implement policy routes on FGT-2 to control traffic between devices.
Answer:
A,B
Comments
Question 7
Refer to the exhibit.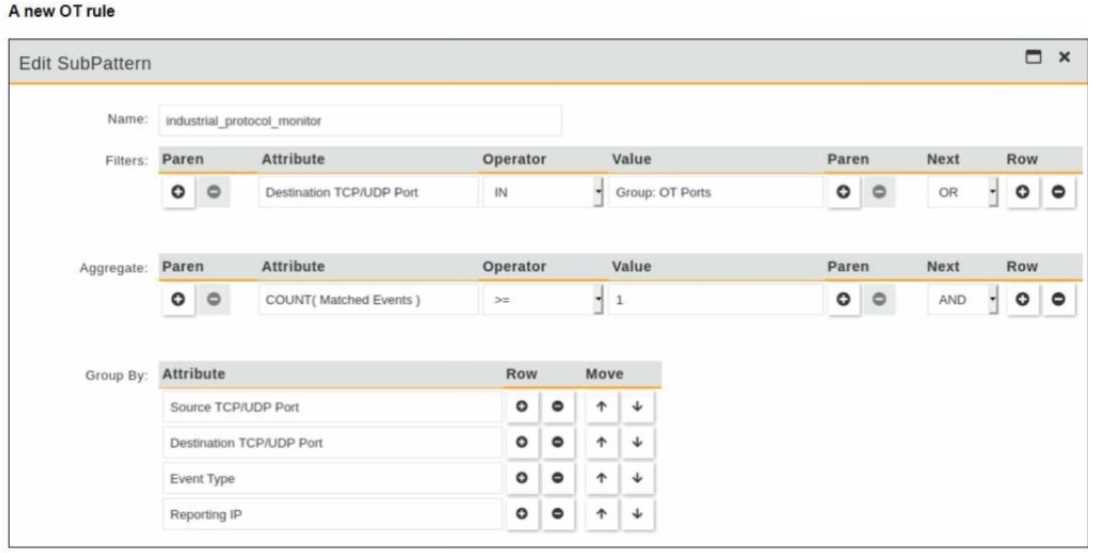
You are creating a new operational technology (OT) rule to monitor Modbus protocol traffic on
FortiSIEM
Which action must you take to ensure that all Modbus messages on the network match the rule?
- A. Add a new condition to filter Modbus traffic based on the source TCP/UDP port
- B. The condition on the SubPattern filter must use the AND logical operator
- C. the Aggregate section, set the attribute value to equal to or greater than 0
- D. In the Group By section remove all attributes that are not configured in the Filter section
Answer:
A
Comments
Question 8
Refer to the exhibit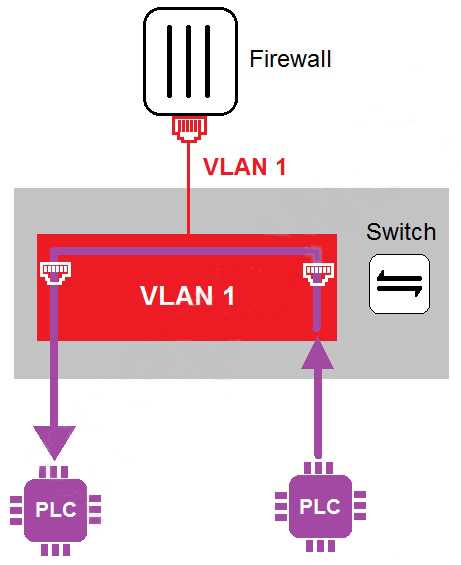
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without
going through the firewall.
Which statement about the topology is true?
- A. PLCs use IEEE802.1Q protocol to communicate each other.
- B. An administrator can create firewall policies in the switch to secure between PLCs.
- C. This integration solution expands VLAN capabilities from Layer 2 to Layer 3.
- D. There is no micro-segmentation in this topology.
Answer:
D
Comments
Question 9
FortiAnalyzer is implemented in the OT network to receive logs from responsible FortiGate devices.
The logs must be processed by FortiAnalyzer.
In this scenario, which statement is correct about the purpose of FortiAnalyzer receiving and
processing multiple log messages from a given PLC or RTU?
- A. To isolate PLCs or RTUs in the event of external attacks
- B. To configure event handlers and take further action on FortiGate
- C. To determine which type of messages from the PLC or RTU causes issues in the plant
- D. To help OT administrators configure the network and prevent breaches
Answer:
B
Comments
Question 10
Which three Fortinet products can you use for device identification in an OT industrial control system
(ICS)? (Choose three.)
- A. FortiSIEM
- B. FortiManager
- C. FortiAnalyzer
- D. FortiGate
- E. FortiNAC
Answer:
A,D,E
Comments
Page 1 out of 6
Viewing questions 1-10 out of 69
page 2