Question 1
An administrator is issuing the following command on a node trying to join a FortiSOAR duster as a
standby: csadm ha join-cluster --status active —role secondary --primary-node 10.0.1.160
The node fails to join the cluster. What is the issue?
- A. The role value should be worker.
- B. The primary node needs to be resolvable via FQDN.
- C. The IP address should be for secondary-node Instead of primary-node.
- D. The status value should be passive.
Answer:
D
Explanation:
When joining a FortiSOAR cluster as a standby node, the correct status value should be passive. Using
active would imply that the node is trying to join as an active node, which could cause conflicts in the
cluster setup. In FortiSOAR, standby nodes must be set as passive to ensure they are recognized
correctly and to avoid conflicts with the primary node or other active nodes within the cluster.
Therefore, setting the status to passive will resolve the issue and allow the node to join the cluster as
intended.
Comments
Question 2
When deleting a user account on FortiSOAR, you must enter the user ID in which file on FortiSOAR?
- A. userDelete.txt.
- B. config_yml
- C. scripts
- D. usersToDelete.txt
Answer:
D
Explanation:
When deleting a user account in FortiSOAR, the user ID must be entered into the usersToDelete.txt
file. This file is specifically used to list users that are marked for deletion. Once the user IDs are listed
in this file, the system can process the deletion of these accounts as part of its user management
operations. This method ensures that only specified users are deleted, as referenced in FortiSOAR's
administrative controls.
Comments
Question 3
Which two statements about upgrading a FortiSOAR HA cluster are true7 (Choose two.)
- A. Nodes can be upgraded while the primary node or secondary node are in the HA cluster.
- B. Upgrading a FortiSOAR HA cluster requires no downtime.
- C. The upgrade procedure for an active-active cluster and an active-passive cluster are the same.
- D. It is recommended that the passive secondary node be upgraded first, and then the active primary node.
Answer:
C, D
Explanation:
Upgrading a FortiSOAR HA cluster follows the same procedure regardless of whether it is configured
in an active-active or active-passive setup. The process generally involves upgrading one node at a
time to minimize service disruption. Best practices recommend upgrading the passive secondary
node first before moving to the active primary node. This sequence helps maintain cluster stability
and ensures that at least one node remains operational during the upgrade.
Comments
Question 4
Which SMS vendor does FortiSOAR support for two-factor authentication?
- A. Twilio
- B. Google Authenticator
- C. 2factor
- D. Telesign
Answer:
D
Explanation:
For two-factor authentication (2FA) via SMS, FortiSOAR supports integration with Telesign. This
vendor provides SMS-based 2FA services, enabling FortiSOAR to leverage Telesign's API for sending
verification codes as part of its security features. Telesign’s service is compatible with FortiSOAR,
ensuring secure user authentication when accessing the platform or certain features.
Comments
Question 5
Which three actions can be performed from within the war room? (Choose three)
- A. View graphical representation of all records linked to an incident in the Artifacts lab
- B. Change the room's status to Escalated to enforce hourly updates.
- C. Investigate issues by tagging results as evidence.
- D. Use the Task Manager tab to create, manage, assign, and track tasks.
- E. Integrate a third-party instant messenger directly into the collaboration workspace.
Answer:
A, C, D
Explanation:
In FortiSOAR's War Room, users can perform several actions to manage incidents effectively. They
can view a graphical representation of records linked to an incident in the Artifacts lab, which helps
visualize connections and dependencies. Additionally, the War Room supports tagging investigation
results as evidence, allowing for a structured approach to incident documentation. Users can also
manage tasks via the Task Manager tab, facilitating task creation, assignment, and tracking within the
incident response workflow.
Comments
Question 6
Which two statements about appliance users are true? (Choose two.)
- A. Appliance users do not have a login ID and do not add to the license count.
- B. Appliance users represent non-human users.
- C. Appliance users use two-factor authentication for messages sent to the API.
- D. Appliance users use time-expiring tokens for primary authentication.
Answer:
A, B
Explanation:
In FortiSOAR, appliance users are accounts that represent non-human entities, such as system
processes or integrations. These users do not require login IDs and therefore do not contribute to the
licensing user count. Appliance users are configured for backend tasks or to interact with external
systems, enabling automated processes without consuming standard user licenses. This approach
optimizes system resources and keeps licensing costs manageable.
Comments
Question 7
Which two statements about Elasticsearch are true? (Choose two.)
- A. Elasticsearch allows you to store, search, and analyze huge volumes of data quickly. In near real time, and return answers in milliseconds.
- B. To change the location of your Elasticsearch instance from the local instance to a remote location, you must update the falcon. conf file.
- C. The minimum version of the Elasticsearch cluster must be 6.0.2. if you want to externalize the Elasticsearch data.
- D. The global search mechanism in FortiSOAR leverages an Elasticsearch database to achieve rapid, efficient searches across the entire record system.
Answer:
A, D
Explanation:
Elasticsearch in FortiSOAR is used for its robust data handling capabilities, allowing rapid storage,
searching, and analysis of vast amounts of data in near real-time. Its integration with FortiSOAR’s
global search enables efficient querying across all records, providing quick response times and a
seamless user experience. The Elasticsearch database is crucial for handling extensive datasets and
delivering swift search results, making it integral to FortiSOAR's performance and data management
capabilities.
Comments
Question 8
Refer to the exhibit.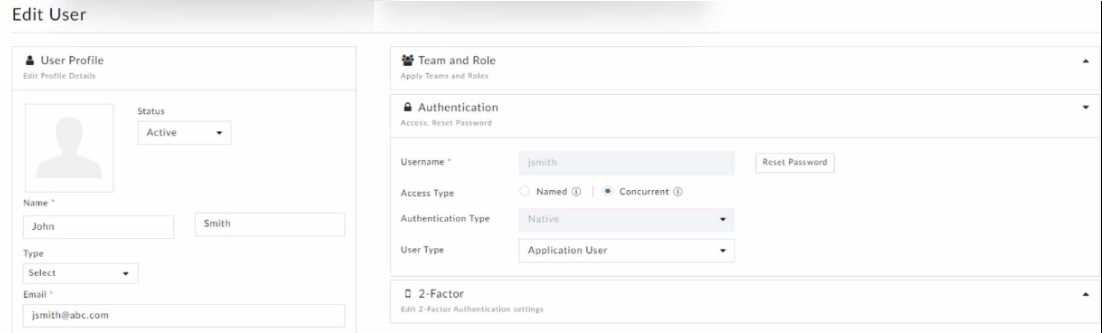
Which statement correctly describes the user's login behavior?
- A. The user is sent to a waiting queue if there are named users logged in.
- B. The user can log in only if there are enough seats available.
- C. The user will always be able to draw from the concurrent pool and log in.
- D. The user has an active concurrent session that does not time out.
Answer:
B
Explanation:
In FortiSOAR, when a user is configured with "Concurrent" access type, their ability to log in depends
on the availability of concurrent user seats. This means the user can only log in if there are available
seats in the concurrent pool. If all seats are occupied, the user must wait until a seat becomes free.
This configuration allows multiple users to share a pool of licenses, making it suitable for
environments where not all users need constant access.
Comments
Question 9
An administrator wants to collect and review all FortiSOAR log tiles to troubleshoot an issue. Which
two methods can they use to accomplish this? (Choose two.)
- A. Enter the csacta services —status command, and then copy the output.
- B. Download the logs from the GUI.
- C. Enter the caacta log —collect directory command.
- D. Review the contents of /var/log/messages.
Answer:
B, C
Explanation:
Administrators can collect and review FortiSOAR logs for troubleshooting in two primary ways. First,
they can download logs directly from the GUI, which provides access to various logs through an
intuitive interface. Secondly, using the command-line interface, the csacta log --collect command can
be used to gather all logs within a specified directory, enabling more detailed offline analysis. Both
methods offer comprehensive log collection to aid in diagnosing and resolving issues.
Comments
Question 10
Which three activities can be achieved using the FortiSOAR queue and shift management feature?
(Choose three)
- A. Initiate shift handovers
- B. Designate a coordinator to monitor queues and shifts
- C. Generate shift leads and shift members
- D. Set up queue meeting rooms
- E. Create queue rules based on matching conditions
Answer:
A, C, E
Explanation:
The FortiSOAR queue and shift management feature enables several key activities for managing
shifts and queues. Administrators can initiate shift handovers, allowing for smooth transitions
between shift leads and members. They can also designate specific roles within shifts, including shift
leads and members, to define responsibilities. Additionally, queue rules can be established based on
certain conditions, ensuring that incidents and tasks are assigned according to predefined criteria,
which helps streamline operations and improve response times.
Comments
Page 1 out of 3
Viewing questions 1-10 out of 39
page 2