Question 1
Which three of the following are components of a security rule? (Choose three.)
- A. Security String
- B. Methods
- C. Action
- D. User or host profile
- E. Trigger
Answer:
CDE
Reference:
https://docs.fortinet.com/document/fortinac/8.8.0/administration-guide/167668/add-
or-modify-a-rule
Comments
Question 2
Which system group will force at-risk hosts into the quarantine network, based on point of
connection?
- A. Forced Isolation
- B. Physical Address Filtering
- C. Forced Quarantine
- D. Forced Remediation
Answer:
D
Explanation:
A remediation plan is established, including a forensic analysis and a reload of the system. Also, users
are forced to change their passwords as the system held local user accounts.
Reference:
https://oit.rice.edu/quarantining-process-used-it-staff-members-introduction
Comments
Question 3
During the on-boarding process through the captive portal, why would a host that successfully
registered remain stuck in the Registration VLAN? (Choose two.)
- A. Bridging is enabled on the host
- B. There is another unregistered host on the same port.
- C. The ports default VLAN is the same as the Registration VLAN.
- D. The wrong agent is installed.
Answer:
BD
Explanation:
Scenario 4: NAT detection disabled, using endpoint compliance policy and agent.
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/868f1267-
7299-11e9-81a4-00505692583a/fortinac-admin-operation-85.pdf
Comments
Question 4
In which view would you find who made modifications to a Group?
- A. The Event Management view
- B. The Security Events view
- C. The Alarms view
- D. The Admin Auditing view
Answer:
D
Explanation:
It’s important to audit Group Policy changes in order to determine the details of changes made to
Group Policies by delegated users.
Reference:
https://www.lepide.com/how-to/audit-chnages-made-to-group-policy-objects.html
Comments
Question 5
Which two of the following are required for endpoint compliance monitors? (Choose two.)
- A. Persistent agent
- B. Logged on user
- C. Security rule
- D. Custom scan
Answer:
AD
Explanation:
DirectDefense’s analysis of FireEye Endpoint attests that the products help meet the HIPAA Security
Rule.
In the menu on the left click the + sign next to Endpoint Compliance to open it.
Reference:
https://www.fireeye.com/content/dam/fireeye-www/products/pdfs/cg-pci-and-hipaa-
compliances.pdf
https://docs.fortinet.com/document/fortinac/8.5.2/administration-guide/92047/add-or-modify-a-
scan
Comments
Question 6
What would happen if a port was placed in both the Forced Registration and the Forced Remediation
port groups?
- A. Only rogue hosts would be impacted.
- B. Both enforcement groups cannot contain the same port.
- C. Only al-risk hosts would be impacted.
- D. Both types of enforcement would be applied.
Answer:
B
Reference:
https://docs.fortinet.com/document/fortinac/8.3.0/administration-
guide/837785/system-groups
Comments
Question 7
Which command line shell and scripting language does FortiNAC use for WinRM?
- A. Linux
- B. Bash
- C. DOS
- D. Powershell
Answer:
D
Explanation:
Open Windows PowerShell or a command prompt. Run the following command to determine if you
already have WinRM over HTTPS configured.
Reference:
https://docs.fortinet.com/document/fortinac/8.7.0/administration-guide/246310/winrm-
device-profile-requirements-and-setup
Comments
Question 8
Where do you look to determine when and why the FortiNAC made an automated network access
change?
- A. The Event view
- B. The Port Changes view
- C. The Connections view
- D. The Admin Auditing view
Answer:
B
Reference:
https://docs.fortinet.com/document/fortigate/6.2.3/cookbook/536166/viewing-event-
logs
Comments
Question 9
What capability do logical networks provide?
- A. VLAN-based inventory reporting
- B. Application of different access values from a single access policy
- C. Autopopulation of device groups based on point of connection
- D. Interactive topology view diagrams
Answer:
A
Explanation:
NTM also includes reporting utilities such as network and inventory reports. You can generate
reports for subnets, switch ports, and VLANs.
Reference:
https://logicalread.com/network-diagram/#.YBk9ZOgzbIU
Comments
Question 10
Refer to the exhibit, and then answer the question below.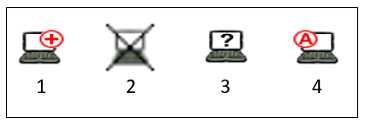
Which host is rogue?
- A. 1
- B. 3
- C. 2
- D. 4
Answer:
B
Reference:
https://docs.fortinet.com/document/fortinac/8.6.0/administration-
guide/283146/evaluating-rogue-hosts
Comments
Page 1 out of 2
Viewing questions 1-10 out of 30
page 2