Question 1
Refer to the exhibits which show a topology diagram (Topology), and a configuration element (Access Control Rule).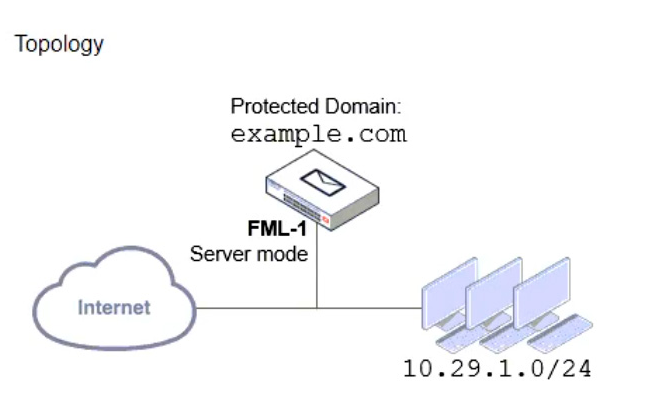
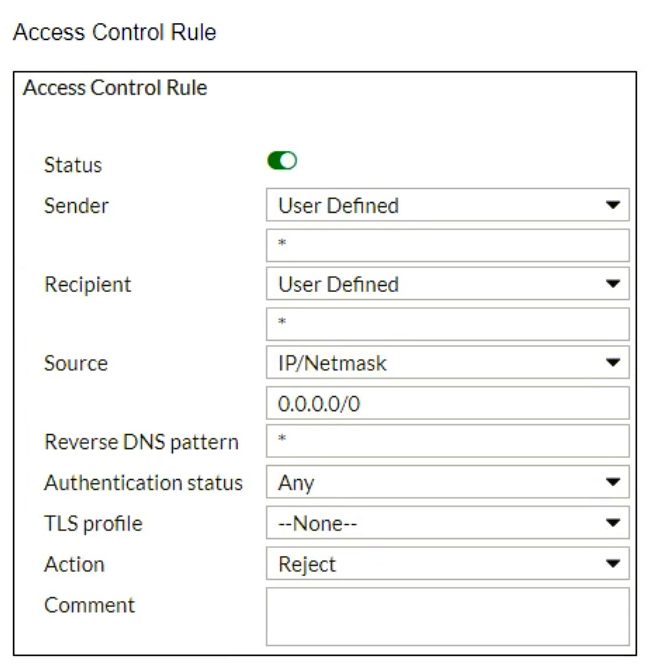
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain.
Which two settings should be used to configure the access receive rule? (Choose two.)
- A. The Sender IP/netmask should be set to 10.29.1.0/24.
- B. The Action should be set to Reject.
- C. The Recipient pattern should be set to *@example.com.
- D. The Authentication status should be set to Authenticated.
Answer:
ad
Comments
Question 2
An organization has different groups of users with different needs in email functionality, such as address book access, mobile device access, email retention periods, and disk quotas.
Which FortiMail feature specific to server mode can be used to accomplish this?
- A. Resource profiles
- B. Domain-level service settings
- C. Access profiles
- D. Address book management options
Answer:
a
Comments
Question 3
Which statement about how impersonation analysis identifies spoofed email addresses is correct?
- A. It uses behavior analysis to detect spoofed addresses.
- B. It uses DMARC validation to detect spoofed addresses.
- C. It maps the display name to the correct recipient email address.
- D. It uses SPF validation to detect spoofed addresses.
Answer:
b
Comments
Question 4
In which two places can the maximum email size be overridden on FortiMail? (Choose two.)
- A. IP Policy configuration
- B. Protected Domain configuration
- C. Resource Profile configuration
- D. Session Profile configuration
Answer:
bc
Comments
Question 5
Refer to the exhibit which displays the domain configuration of a transparent mode FortiMail device.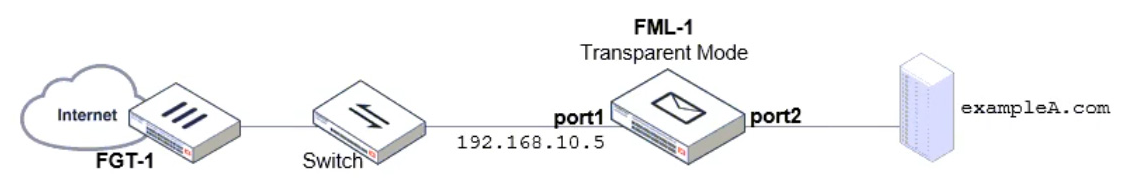
Based on the exhibit, which two sessions are considered incoming sessions? (Choose two.)
- A. DESTINATION IP: 172.16.32.56 MAIL FROM: [emailprotected] RCPT TO: [emailprotected]
- B. DESTINATION IP: 192.168.54.10 MAIL FROM: [emailprotected] RCPT TO: [emailprotected]
- C. DESTINATION IP: 10.25.32.15 MAIL FROM: [emailprotected] RCPT TO: [emailprotected]
- D. DESTINATION IP: 172.16.32.56 MAIL FROM: [emailprotected] RCPT TO: [emailprotected]
Answer:
ad
Comments
Question 6
A FortiMail device is configured with the protected domain example.com.
If none of the senders is authenticated, which two envelope addresses will require an access receive rule? (Choose two.)
- A. MAIL FROM: [emailprotected] RCPT TO: [emailprotected]
- B. MAIL FROM: [emailprotected] RCPT TO: [emailprotected]
- C. MAIL FROM: [emailprotected] RCPT TO: [emailprotected]
- D. MAIL FROM: [emailprotected] RCPT TO: [emailprotected]
Answer:
ab
Comments
Question 7
Refer to the exhibit, which shows an inbound recipient policy.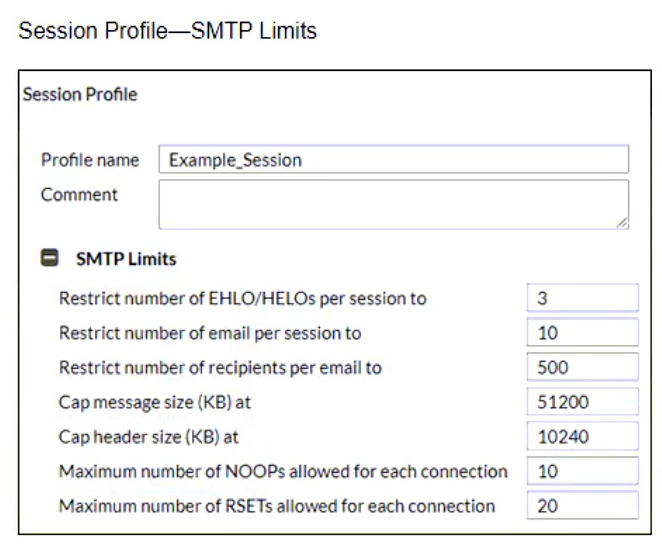
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
- A. Move this incoming recipient policy to the top of the list.
- B. Configure a matching IP policy with the exclusive flag enabled.
- C. Configure an access delivery rule to enforce authentication.
- D. Configure an access receive rule to verify authentication status.
Answer:
d
Comments
Question 8
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9:INTERNAL.
Which two statements describe what this policy ID means? (Choose two.)
- A. Access control policy number 9 was used.
- B. The FortiMail configuration is missing an access delivery rule.
- C. The email was processed using IP-based policy ID 4.
- D. FortiMail is applying the default behavior for relaying inbound email.
Answer:
ac
Comments
Question 9
Refer to the exhibit which shows the output of an email transmission using a telnet session.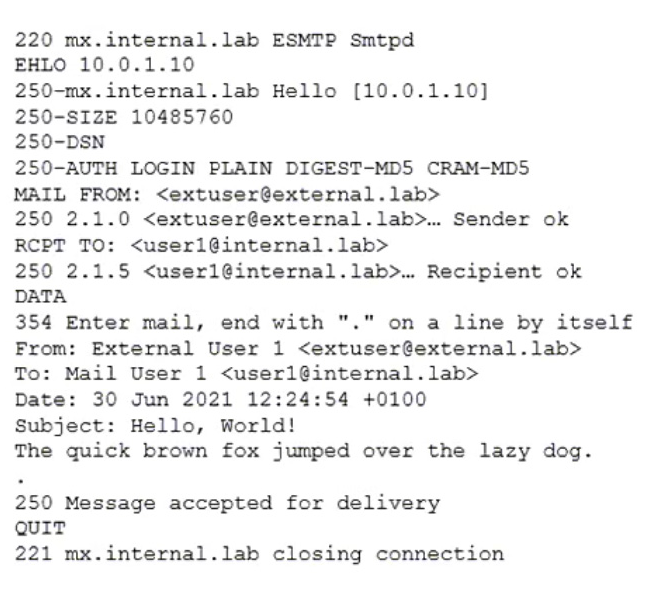
What are two correct observations about this SMTP session? (Choose two.)
- A. The SMTP envelope addresses are different from the message header addresses.
- B. The "250 Message accepted for delivery" message is part of the message body.
- C. The "Subject" is part of the message header.
- D. The "220 mx.internal.lab ESMTP Smtpd" message is part of the SMTP banner.
Answer:
cd
Comments
Question 10
Refer to the exhibit which displays a list of IBE users on a FortiMail device.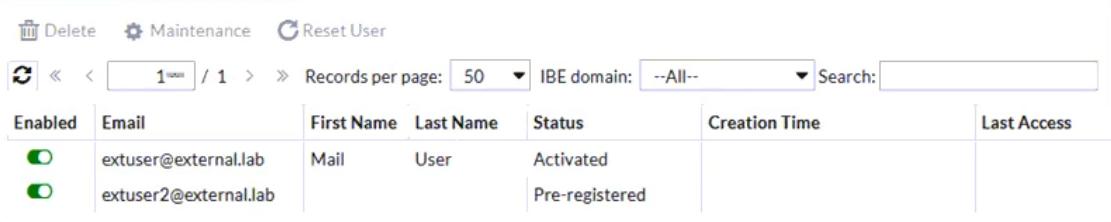
Which statement describes the pre-registered status of the IBE user [email protected]?
- A. The user has received an IBE notification email, but has not accessed the HTTPS URL or attachment yet.
- B. The user was registered by an administrator in anticipation of IBE participation.
- C. The user account has been de-activated, and the user must register again the next time they receive an IBE email.
- D. The user has completed the IBE registration process, but has not yet accessed their IBE email.
Answer:
a
Comments
Page 1 out of 2
Viewing questions 1-10 out of 28
page 2