Fortinet nse5-fsm-5-2 practice test
Fortinet NSE 5 - FortiSIEM 5.2 Exam
Last exam update: Oct 15 ,2024
Question 1
Which two export methods are available for FortiSIEM analytics results? (Choose two.)
A.CSV
B.PNG
C.HTML
D. PDF
Answer:
AD
Question 2
What is a prerequisite for a FortiSIEM supervisor with a worker deployment, using the proprietary
flat file database?
A.The
CMDB
database
must
be
on
NFS
B.The
event
database
must
be
on
NFS
C.The
event
database
must
be
on
a
local
disk
D. The \archive mount must be on a local disk
Answer:
B
Question 3
An administrator wants to search for events received from Linux and Windows agents.
Which attribute should the administrator use in search filters, to view events received from agents
only.
- A. External Event Receive Protocol
- B. Event Received Proto Agents
- C. External Event Receive Raw Logs
- D. External Event Receive Agents
Answer:
A
Question 4
If a performance rule is triggered repeatedly due to high CPU use. what occurs m the incident table?
- A. A new incident is created each time the rule is triggered, and the First Seen and Last Seen times are updated.
- B. The incident status changes to Repeated and the First Seen and Last Seen times are updated.
- C. A new incident is created based on the Rule Frequency value, and the First Seen and Last Seen times are updated
- D. The Incident Count value increases, and the First Seen and Last Seen tomes update
Answer:
A
Question 5
What is a prerequisite for FortiSIEM Linux agent installation?
- A. The web server must be installed on the Linux server being monitored
- B. The auditd service must be installed on the Linux server being monitored
- C. The Linux agent manager server must be installed.
- D. Both the web server and the audit service must be installed on the Linux server being monitored
Answer:
D
Question 6
Which process converts Raw log data to structured data?
- A. Data enrichment
- B. Data classification
- C. Data parsing
- D. Data validation
Answer:
C
Question 7
Which database is used for storing anomaly data, that is calculated for different parameters, such as
traffic and device resource usage running averages, and standard deviation values?
- A. Profile DB
- B. Event DB
- C. CMDB
- D. SVN DB
Answer:
A
Question 8
In FotiSlEM enterprise licensing mode, if the link between the collector and data center FortiSlEM
cluster a down what happens?
- A. The collector drops incoming events like syslog. but slops performance collection
- B. The collector continues performance collection of devices, but stops receiving syslog
- C. The collector buffers events
- D. The collector processes stop, and events are dropped
Answer:
D
Question 9
Refer to the exhibit.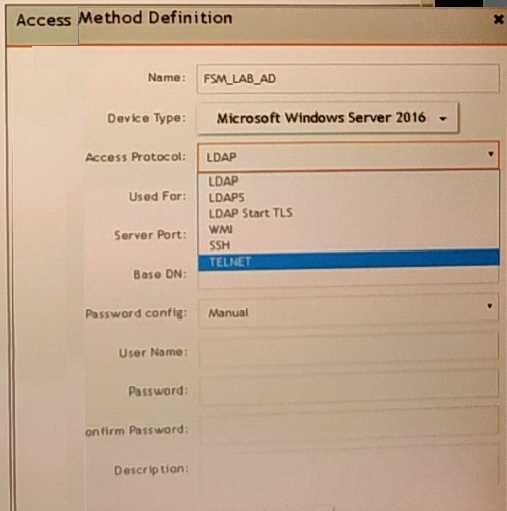
A FortiSIEM administrator wants to collect both SIEM event logs and performance and availability
metrics (PAM) events from a Microsoft Windows server
Which protocol should the administrator select in the Access Protocol drop-down list so that
FortiSIEM will collect both SIEM and PAM events?
- A. TELNET
- B. WMI
- C. LDAPS
- D. LDAP start TLS
Answer:
A
Question 10
What are the four categories of incidents?
- A. Devices, users, high risk, and low risk
- B. Performance, availability, security, and change
- C. Performance, devices, high risk, and low risk
- D. Security, change, high risk, and low risk
Answer:
B
Question 11
Refer to the exhibit.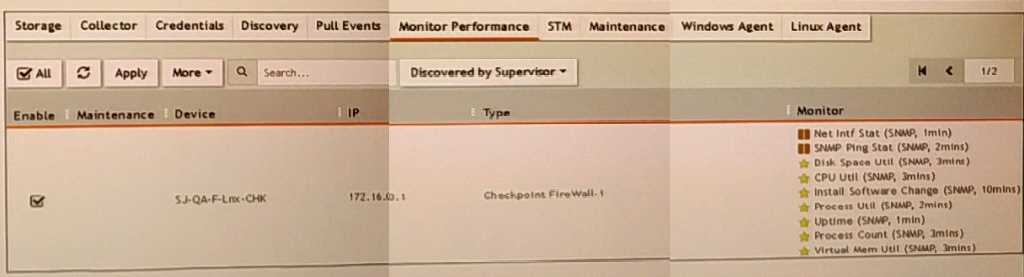
What do the yellow stars listed in the Monitor column indicate?
- A. A yellow star indicates that a metric was applied during discovery, and data has been collected successfully
- B. A yellow star indicates that a metric was applied during discovery, but data collection has not started
- C. A yellow star indicates that a metric was applied during discovery, but FortiSIEM is unable to collect data.
- D. A yellow star indicates that a metric was not applied during discovery and, therefore, FortiSEIM was unable to collect data.
Answer:
B
Question 12
Refer to the exhibit.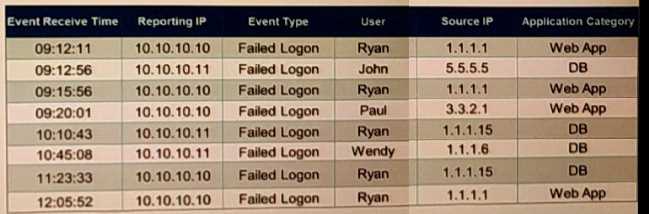
If events are grouped by Event Receive Time, Reporting IP, and User attributes in FortiSIEM, how
many results will be displayed?
- A. Eight results will be displayed
- B. Four results will be displayed
- C. Two results will be displayed
- D. Unique attributes cannot be grouped
Answer:
D
Question 13
Refer to the exhibit.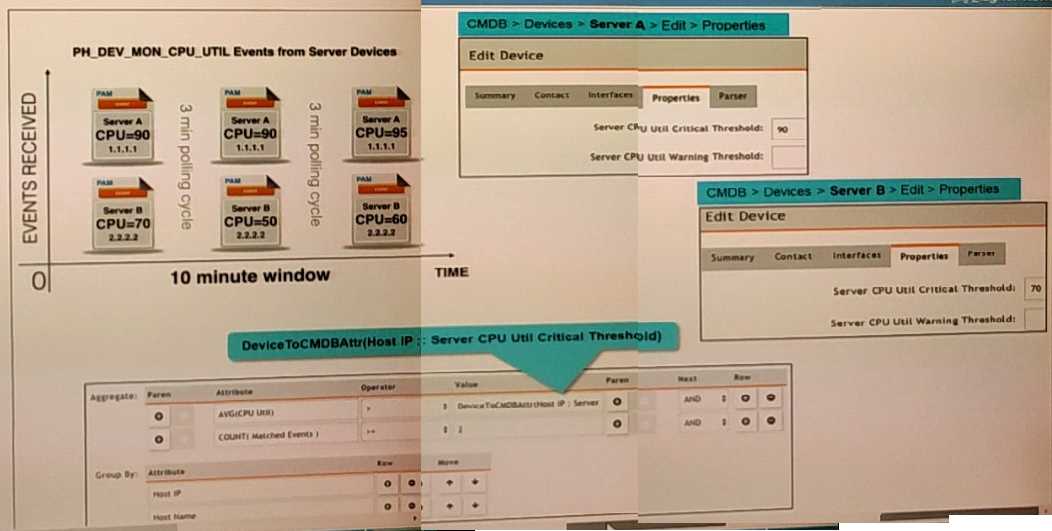
Three events are collected over a 10-minutc time period from two servers Server A and Server B.
Based on the settings being used for the rule subpattern. how many incidents will the servers
generate?
- A. Server A will not generate any incidents and Server B will not generate any incidents
- B. Server A will generate one incident and Server B wifl generate one incident
- C. Server A will generate one incident and Server B will not generate any incidents
- D. Server B will generate one incident and Server A will not generate any incidents
Answer:
A
Question 14
What are the four possible incident status values?
- A. Active, dosed, cleared, open
- B. Active, cleared, cleared manually, system cleared
- C. Active, closed, manual, resolved
- D. Active, auto cleared, manual, false positive
Answer:
C
Question 15
Which discovery scan type is prone to miss a device, if the device is quiet and the entry foe that
device is not present in the ARP table of adjacent devices?
- A. CMDB scan
- B. L2 scan
- C. Range scan
- D. Smart scan
Answer:
D