Question 1
How does FortiGate act when using SSL VPN in web mode?
- A. FortiGate acts as an FDS server.
- B. FortiGate acts as an HTTP reverse proxy.
- C. FortiGate acts as DNS server.
- D. FortiGate acts as router.
Answer:
B
Explanation:
Reference:
https://pub.kb.fortinet.com/ksmcontent/Fortinet-Public/current/Fortigate_v4.0MR3/fortigate-
sslvpn-40-mr3.pdf
Comments
Question 2
Which three statements explain a flow-based antivirus profile? (Choose three.)
- A. Flow-based inspection uses a hybrid of the scanning modes available in proxy-based inspection.
- B. If a virus is detected, the last packet is delivered to the client.
- C. The IPS engine handles the process as a standalone.
- D. FortiGate buffers the whole file but transmits to the client at the same time.
- E. Flow-based inspection optimizes performance compared to proxy-based inspection.
Answer:
ADE
Explanation:
Reference: https://forum .fortinet.com/tm .aspx?m=192309
Comments
Question 3
Refer to the exhibits to view the firewall policy (Exhibit A) and the antivirus profile (Exhibit B).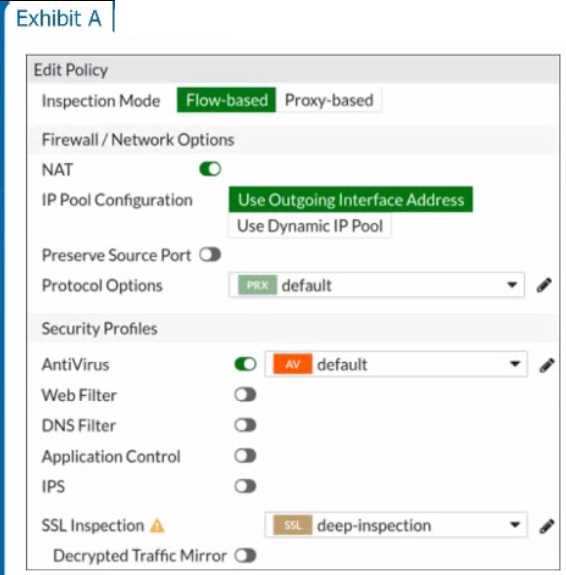
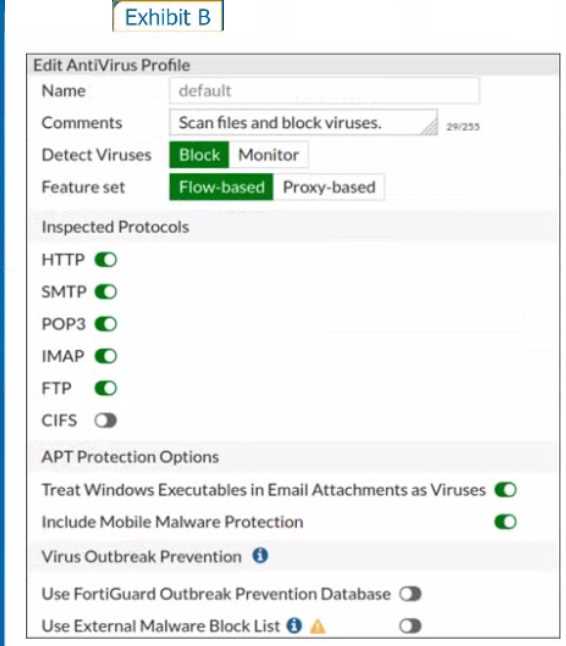
Which statement is correct if a user is unable to receive a block replacement message when
downloading an infected file for the first time?
- A. The firewall policy performs the full content inspection on the file.
- B. The flow-based inspection is used, which resets the last packet to the user.
- C. The volume of traffic being inspected is too high for this model of FortiGate.
- D. The intrusion prevention security profile needs to be enabled when using flow-based inspection mode.
Answer:
B
Explanation:
· "ONLY" If the virus is detected at the "START" of the connection, the IPS engine sends the block
replacement message immediately
· When a virus is detected on a TCP session (FIRST TIME), but where "SOME PACKETS" have been
already forwarded to the receiver, FortiGate "resets the connection" and does not send the last
piece of the file. Although the receiver got most of the file content, the file has been truncated and
therefore, can't be opened. The IPS engine also caches the URL of the infected file, so that if a
"SECOND ATTEMPT" to transmit the file is made, the IPS engine will then send a block replacement
message to the client instead of scanning the file again.
In flow mode, the FortiGate drops the last packet killing the file. But because of that the block
replacement message cannot be displayed. If the file is attempted to download again the block
message will be shown.
Comments
Question 4
A network administrator wants to set up redundant IPsec VPN tunnels on FortiGate by using two
IPsec VPN tunnels and static routes.
* All traffic must be routed through the primary tunnel when both tunnels are up
* The secondary tunnel must be used only if the primary tunnel goes down
* In addition, FortiGate should be able to detect a dead tunnel to speed up tunnel failover
Which two key configuration changes are needed on FortiGate to meet the design requirements?
(Choose two,)
- A. Configure a high distance on the static route for the primary tunnel, and a lower distance on the static route for the secondary tunnel.
- B. Enable Dead Peer Detection.
- C. Configure a lower distance on the static route for the primary tunnel, and a higher distance on the static route for the secondary tunnel.
- D. Enable Auto-negotiate and Autokey Keep Alive on the phase 2 configuration of both tunnels.
Answer:
BC
Explanation:
Study Guide – IPsec VPN – IPsec configuration – Phase 1 Network.
When Dead Peer Detection (DPD) is enabled, DPD probes are sent to detect a failed tunnel and bring
it down before its IPsec SAs expire. This failure detection mechanism is very useful when you have
redundant paths to the same destination, and you want to failover to a backup connection when the
primary connection fails to keep the connectivity between the sites up.
There are three DPD modes. On demand is the default mode.
Study Guide – IPsec VPN – Redundant VPNs.
Add one phase 1 configuration for each tunnel. DPD should be enabled on both ends.
Add at least one phase 2 definition for each phase 1.
Add one static route for each path. Use distance or priority to select primary routes over backup
routes (routes for the primary VPN must have a lower distance or lower priority than the backup).
Alternatively, use dynamic routing.
Configure FW policies for each IPsec interface.
Comments
Question 5
Which engine handles application control traffic on the next-generation firewall (NGFW) FortiGate?
- A. Antivirus engine
- B. Intrusion prevention system engine
- C. Flow engine
- D. Detection engine
Answer:
B
Explanation:
http://docs.fortinet.com/document/fortigate/6.0.0/handbook/240599/application-control
Reference: http://docs.fortinet.com/document/fortigate/6.0.0/handbook/240599/application-
control
Comments
Question 6
Refer to the exhibit.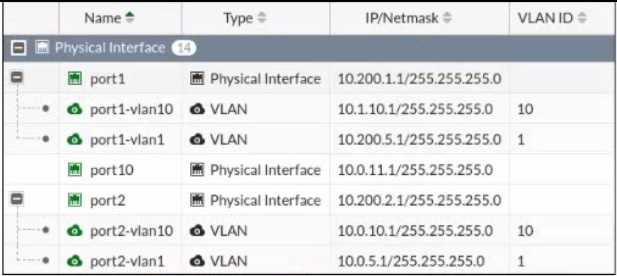
Given the interfaces shown in the exhibit. which two statements are true? (Choose two.)
- A. Traffic between port2 and port2-vlan1 is allowed by default.
- B. port1-vlan10 and port2-vlan10 are part of the same broadcast domain.
- C. port1 is a native VLAN.
- D. port1-vlan and port2-vlan1 can be assigned in the same VDOM or to different VDOMs.
Answer:
CD
Explanation:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-rules-about-VLAN-configuration-and-
VDOM-interf
https://kb.fortinet.com/kb/viewContent.do?externalId=FD30883
Comments
Question 7
Which statement about video filtering on FortiGate is true?
- A. Full SSL Inspection is not required.
- B. It is available only on a proxy-based firewall policy.
- C. It inspects video files hosted on file sharing services.
- D. Video filtering FortiGuard categories are based on web filter FortiGuard categories.
Answer:
B
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/7.0.0/new-features/190873/video-filtering
Comments
Question 8
Refer to the exhibit.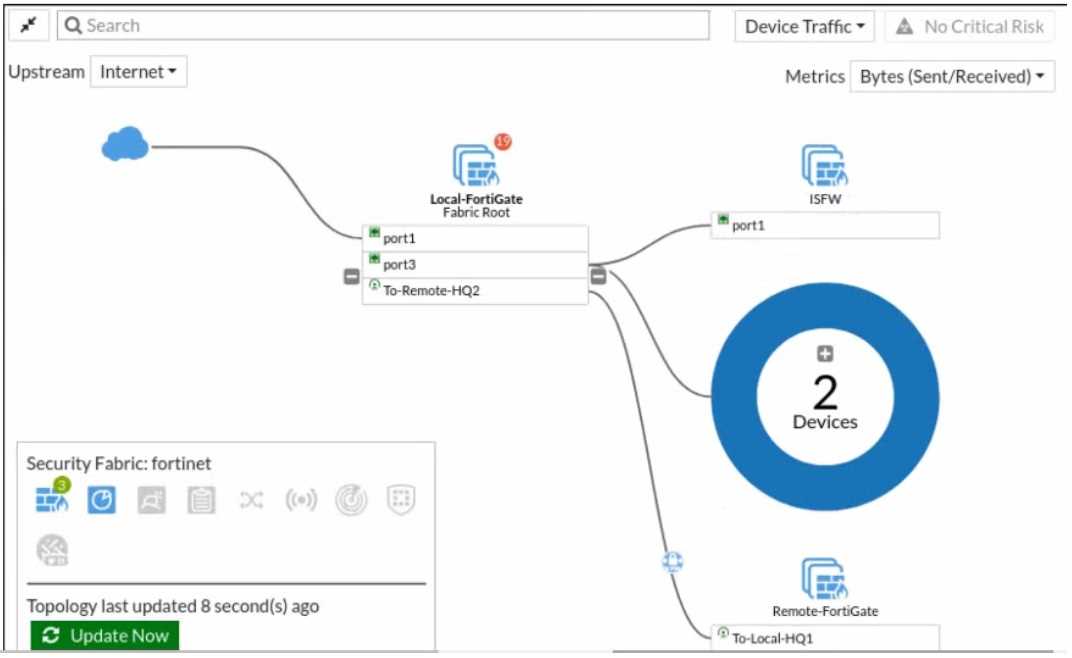
Given the security fabric topology shown in the exhibit, which two statements are true? (Choose
two.)
- A. There are five devices that are part of the security fabric.
- B. Device detection is disabled on all FortiGate devices.
- C. This security fabric topology is a logical topology view.
- D. There are 19 security recommendations for the security fabric.
Answer:
CD
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/5.6.0/cookbook/761085/results
https://docs.fortinet.com/document/fortimanager/6.2.0/new-features/736125/security-fabric-
topology
Comments
Question 9
A network administrator has enabled SSL certificate inspection and antivirus on FortiGate. When
downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When
downloading the same file through HTTPS, FortiGate does not detect the virus and the file can be
downloaded.
What is the reason for the failed virus detection by FortiGate?
- A. The website is exempted from SSL inspection.
- B. The EICAR test file exceeds the protocol options oversize limit.
- C. The selected SSL inspection profile has certificate inspection enabled.
- D. The browser does not trust the FortiGate self-signed CA certificate.
Answer:
AC
Explanation:
SSL Inspection Profile, on the Inspection method there are 2 options to choose from, SSL Certificate
Inspection or Full SSL Inspection. FG SEC 7.2 Studi Guide: Full SSL Inspection level is the only choice
that allows antivirus to be effective.
Comments
Question 10
Refer to the exhibits.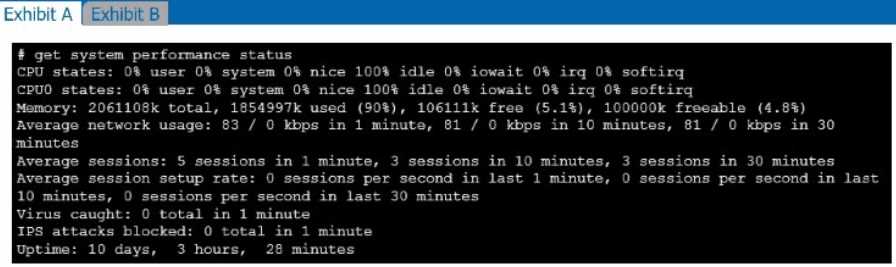
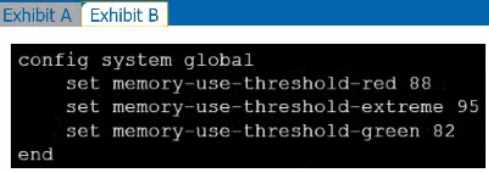
Exhibit A shows system performance output. Exhibit B shows a FortiGate configured with the default
configuration of high memory usage thresholds. Based on the system performance output, which
two statements are correct? (Choose two.)
- A. Administrators can access FortiGate only through the console port.
- B. FortiGate has entered conserve mode.
- C. FortiGate will start sending all files to FortiSandbox for inspection.
- D. Administrators cannot change the configuration.
Answer:
BD
Explanation:
Reference:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-Conserve-mode-changes/ta-
p/198502
https://community.fortinet.com/t5/FortiGate/Technical-Tip-Conserve-mode-changes/ta-p/198502
configurable thresholds
Though it is recommended to keep the default memory threshold, a new CLI command has been
added to allow administrators to adjust the thresholds.
Default values are :
- red : 88% of total memory is considered "used memory"
- extreme : 95% of total memory is considered "used memory"
- green : 82% of total memory is considered "used memory"
Comments
Page 1 out of 18
Viewing questions 1-10 out of 183
page 2