Question 1
Refer to the exhibits.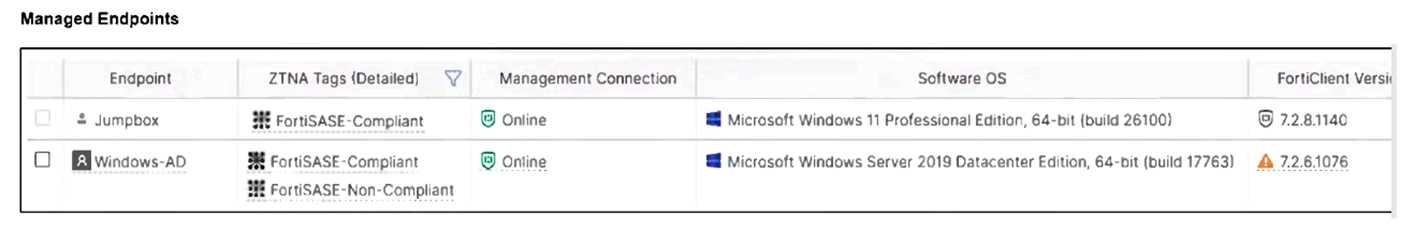
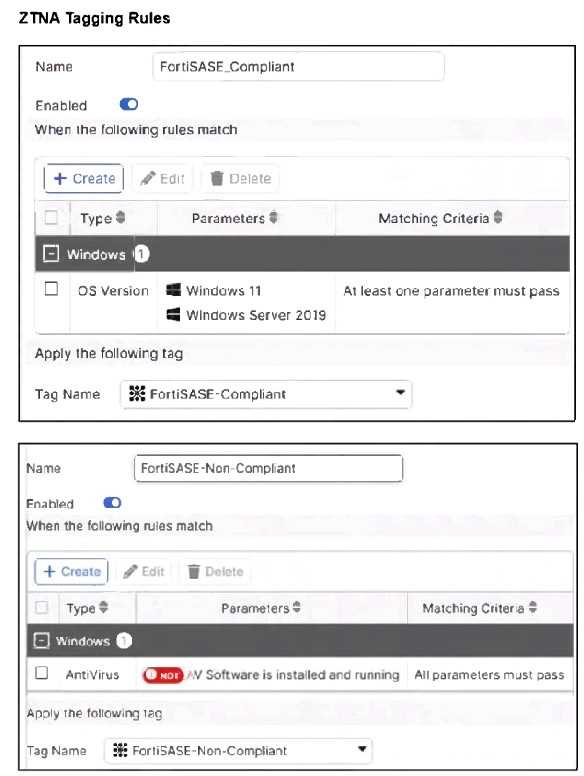
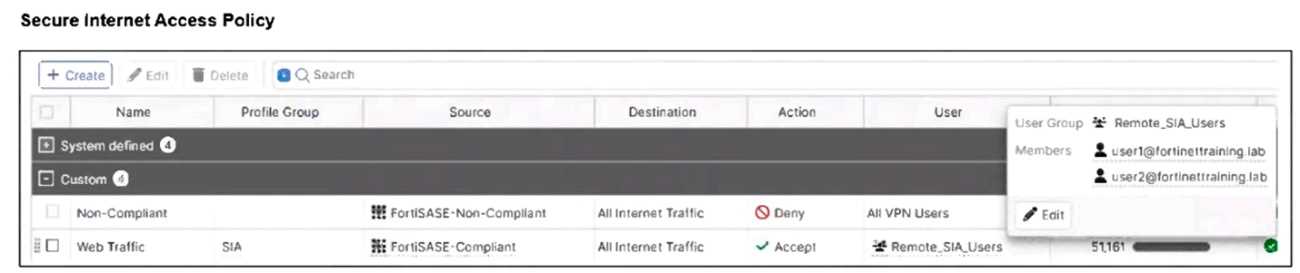
Jumpbox and Windows-AD are endpoints from the same remote location. Jumpbox can access the
internet through FortiSASE, while Windows-AD can no longer access the internet.
Based on the information in the exhibits, which reason explains the outage on Windows-AD?
- A. Windows-AD is excluded from FortiSASE management.
- B. The FortiClient version installed on Windows AD does not match the expected version on FortiSASE.
- C. The device posture for Windows-AD has changed.
- D. The remote VPN user on Windows-AD no longer matches any VPN policy.
Answer:
C
Explanation:
The Windows-AD endpoint now has both "FortiSASE-Compliant" and "FortiSASE-Non-Compliant"
tags due to failing the antivirus software check. As a result, the Secure Internet Access Policy matches
the "Non-Compliant" rule, which is set to Deny, causing the device to lose internet access.
Comments
Question 2
Which description of the FortiSASE inline-CASB component is true?
- A. It has limited visibility when data is transmitted.
- B. It detects data in motion.
- C. It is placed outside the traffic path.
- D. It relies on API to integrate with cloud services.
Answer:
B
Explanation:
FortiSASE inline-CASB operates in the traffic path to provide real-time visibility and control over data
in motion as it is transmitted to and from cloud applications.
Comments
Question 3
Which authentication method overrides any other previously configured user authentication on
FortiSASE?
- A. MFA
- B. Local
- C. RADIUS
- D. SSO
Answer:
D
Explanation:
Single Sign-On (SSO) overrides any other previously configured user authentication method on
FortiSASE, taking precedence for user authentication.
Comments
Question 4
What are two advantages of using zero-trust tags? (Choose two.)
- A. Zero-trust tags can determine the security posture of an endpoint.
- B. Zero-trust tags can be assigned to endpoint profiles based on user groups.
- C. Zero-trust tags can be used to allow or deny access to network resources.
- D. Zero-trust tags can help monitor endpoint system resource usage.
Answer:
A,C
Explanation:
Zero-trust tags assess endpoint compliance based on defined posture rules and are used in access
policies to control whether a device is permitted or denied access to specific network resources.
Comments
Question 5
Which FortiSASE feature ensures least-privileged user access to corporate applications that are
protected by an on-premises FortiGate device?
- A. secure web gateway (SWG)
- B. zero trust network access (ZTNA)
- C. cloud access security broker (CASB)
- D. remote browser isolation (RBI)
Answer:
B
Explanation:
ZTNA enforces least-privileged access by verifying user identity and device posture before granting
access to specific corporate applications, even when protected by an on-premises FortiGate.
Comments
Question 6
A company must provide access to a web server through FortiSASE secure private access for
contractors.
What is the recommended method to provide access?
- A. Configure a TCP access proxy forwarding rule and push it to the contractor FortiClient endpoint.
- B. Update the DNS records on the endpoint to access private applications.
- C. Publish the web server URL on a bookmark portal and share it with contractors.
- D. Update the PAC file with the web server URL and share it with contractors.
Answer:
C
Explanation:
The bookmark portal is the recommended method for providing contractors access to private web
applications through FortiSASE Secure Private Access, as it offers a user-friendly, secure, and
controlled access mechanism without requiring full network connectivity.
Comments
Question 7
Your FortiSASE customer has a small branch office in which ten users will be using their personal
laptops and mobile devices to access the internet.
Which deployment should they use to secure their internet access with minimal configuration?
- A. Deploy FortiGate as a LAN extension to secure internet access.
- B. Deploy FortiAP to secure internet access.
- C. Deploy FortiClient endpoint agent to secure internet access.
- D. Deploy SD-WAN on-ramp to secure internet access.
Answer:
B
Explanation:
Deploying FortiAP enables secure internet access for unmanaged personal devices in small branch
offices with minimal configuration by automatically directing traffic through FortiSASE, eliminating
the need for endpoint installation or complex setup.
Comments
Question 8
Which information does FortiSASE use to bring network lockdown into effect on an endpoint?
- A. Zero-day malware detection on endpoint
- B. The number of critical vulnerabilities detected on the endpoint
- C. The security posture of the endpoint based on ZTNA tags
- D. The connection status of the tunnel to FortiSASE
Answer:
C
Explanation:
FortiSASE uses ZTNA tags to assess the endpoint’s security posture. If the posture is non-compliant
based on predefined rules, FortiSASE enforces network lockdown to restrict access accordingly.
Comments
Question 9
For monitoring potentially unwanted applications on endpoints, which information is available on
the FortiSASE software installations page?
- A. the vendor of the software
- B. the endpoint the software is installed on
- C. the license status of the software
- D. the usage frequency of the software
Answer:
B
Explanation:
The FortiSASE software installations page shows which endpoints have specific software installed,
allowing administrators to monitor potentially unwanted applications across the network.
Comments
Question 10
What is the recommended method to upgrade FortiClient in a FortiSASE deployment?
- A. Remote users must upgrade the FortiClient manually.
- B. FortiSASE automatically upgrades FortiClient when a new version is released.
- C. The FortiSASE administrator must assign endpoint groups to an endpoint upgrade rule.
- D. The FortiSASE administrator will upload the desired FortiClient version to the FortiSASE portal and push it to endpoints.
Answer:
C
Explanation:
In FortiSASE, the recommended method to upgrade FortiClient is to configure an endpoint upgrade
rule and assign it to specific endpoint groups. This ensures controlled and automated upgrades
across managed devices.
Comments
Page 1 out of 5
Viewing questions 1-10 out of 53
page 2