Question 1
Refer to the exhibit.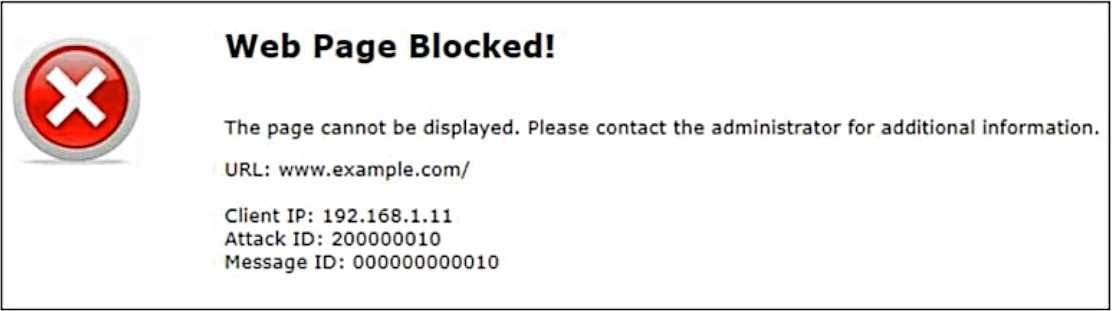
Attack ID 20000010 is brute force logins.
Which statement is accurate about the potential attack?
- A. The attacker has successfully retrieved the credentials to www.example.com.
- B. www.example.com is running attacks against the client 192.168.1.11.
- C. The attack has happened 10 times.
- D. 192.168.1.11 is sending suspicious traffic to FortiWeb.
Answer:
D
Explanation:
The Attack ID of 20000010 refers to a brute force login attempt, which typically indicates that the
client IP (192.168.1.11) is sending suspicious or malicious traffic to the FortiWeb. FortiWeb detected
and blocked this suspicious activity, which is why the page is shown as blocked.
Comments
Question 2
Which three stages are part of creating a machine learning (ML) bot detection algorithm? (Choose
three.)
- A. Model building
- B. Model running
- C. Model verification
- D. Sample collecting
- E. Model Bayesian analysis
Answer:
A, C, D
Explanation:
Model building: In this stage, you design and develop the ML model, which involves selecting
appropriate algorithms and features to detect bot activity.
Model verification: This is where you test and evaluate the model's performance to ensure it can
accurately detect bots without false positives or negatives.
Sample collecting: Gathering relevant data samples (e.g., bot and non-bot traffic) to train the
machine learning model is crucial to ensure it can learn from various scenarios.
Comments
Question 3
Under which two circumstances does FortiWeb use its own certificates? (Choose two.)
- A. Connecting to browser clients using SSL
- B. Making a secondary HTTPS connection to a server where FortiWeb acts as a client
- C. Routing an HTTPS connection to a FortiGate
- D. An administrator session connecting to the GUI using HTTPS
Answer:
B, D
Explanation:
Making a secondary HTTPS connection to a server where FortiWeb acts as a client: When FortiWeb
needs to connect to an external server via HTTPS (acting as a client), it may use its own certificates
for that connection.
An administrator session connecting to the GUI using HTTPS: FortiWeb uses its own certificates to
secure the HTTPS connection between the administrator and the FortiWeb GUI. This ensures secure
access for management purposes.
Comments
Question 4
You are using HTTP content routing on FortiWeb. You want requests for web application A to be
forwarded to a cluster of web servers, which all host the same web application. You want requests
for web application B to be forwarded to a different, single web server.
Which statement regarding this solution is true?
- A. You must chain policies so that all requests go to the virtual server for policy A first, and then redirect requests for web application B to go to the virtual server for policy B
- B. You must create static routes on the FortiWebto allow these requests.
- C. You must put the single web server for application B into a server pool and use it with HTTP content routing.
- D. The server policy always applies the same web protection profile to both web application A and web application B.
Answer:
C
Explanation:
To forward requests for web application B to a single web server, you would configure FortiWeb to
use HTTP content routing and create a server pool specifically for web application B. In FortiWeb,
server pools are used to group servers together based on application requirements, and you can
configure the pool to contain only a single web server for application B.
Comments
Question 5
What can a FortiWeb administrator do if a client has been incorrectly period blocked?
- A. Allow the period block to expire on its own, you cannot override it.
- B. Manually release the IP address from the blocklist.
- C. Disable and re-enable the server policy.
- D. Force a new IP address to the client.
Answer:
B
Explanation:
If a client has been incorrectly blocked due to a period block, the FortiWeb administrator can
manually release the IP address from the blocklist. This allows the client to access the application
again before the block expires naturally.
Comments
Question 6
Which two functions does the first layer of the FortiWeb anomaly machine learning (ML) analysis
mechanism perform? (Choose two.)
- A. Determines whether an anomaly is a real attack or just a harmless anomaly that should be ignored
- B. Determines a probability model behind every parameter and HTTP method passing through FortiWeb
- C. Determines whether traffic is an anomaly, based on observable features overtime
- D. Determines if a detected threat is a false-positive or not
Answer:
B, C
Explanation:
The first layer of the FortiWeb anomaly machine learning (ML) analysis mechanism focuses on
analyzing traffic and creating a probability model for parameters and HTTP methods to detect
potential anomalies. It also assesses traffic patterns over time to determine whether certain
behavior is anomalous. These functions are key to understanding and classifying traffic before further
analysis is done.
Comments
Question 7
Which is an example of a cross-site scripting (XSS) attack?
- A. SELECT username FROM accounts WHERE username='admin';-- ' AND password='password';
- B. <img src="http://badfile/nothere" onerror=alert(document.cookie);>
- C. SELECT username FROM accounts WHERE username='XSS' ' AND password='alert("http://badurl.com")';
- D. <IMG SRC="xss.png">
Answer:
B
Explanation:
Cross-Site Scripting (XSS) is a type of web security vulnerability that allows attackers to inject
malicious scripts into web pages viewed by users. This can lead to session hijacking, credential theft,
or redirection to malicious sites. XSS attacks typically exploit vulnerabilities in web applications that
fail to properly sanitize user input.
Here’s an analysis of the given options:
A . SELECT username FROM accounts WHERE username='admin';-- ' AND password='password';
This is an example of SQL Injection (SQLi) rather than XSS. It manipulates SQL queries to bypass
authentication, not execute JavaScript in a user’s browser.
B . <img src="http://badfile/nothere" onerror=alert(document.cookie);>
This is a classic XSS attack.
It uses an <img> tag with a non-existent src attribute.
The onerror event triggers when the image fails to load, executing alert(document.cookie);, which
can expose session cookies.
This method is commonly used for stealing cookies or executing arbitrary scripts.
C . SELECT username FROM accounts WHERE username='XSS' ' AND
password='alert("http://badurl.com")';
This is neither a valid SQL injection nor a valid XSS attack.
The syntax suggests an incorrect SQL query rather than JavaScript execution in a browser.
D . <IMG SRC="xss.png">
This is not a valid XSS attack unless there is an additional event handler like onload, onerror, or
onmouseover executing JavaScript.
By itself, it just loads an image and does not execute any malicious script.
Thus, Option B is the correct answer as it represents a real-world XSS attack technique.
Reference:
OWASP XSS Guide: https://owasp.org/www-community/attacks/xss/
Fortinet XSS Protection Documentation: https://docs.fortinet.com/
Comments
Question 8
Which Layer 7 routing method does FortiWeb support?
- A. URL policy routing
- B. OSPF
- C. BGP
- D. HTTP content routing
Answer:
D
Explanation:
FortiWeb is a Web Application Firewall (WAF) designed to protect web applications from various
threats. Among its features, FortiWeb supports Layer 7 routing methods, which operate based on the
content of the HTTP/HTTPS traffic.
HTTP Content Routing refers to the capability of directing incoming web traffic to specific backend
servers based on characteristics found within the HTTP requests, such as URL paths, headers, or
other content. This allows for more granular and efficient distribution of traffic, ensuring that
requests are handled by the appropriate servers based on their content.
Analysis of Options:
A . URL policy routing: While this term suggests routing decisions based on URL policies, it is not a
standard term used in FortiWeb's documentation. FortiWeb's content routing encompasses URL-
based decisions, making this option less precise.
B . OSPF (Open Shortest Path First): This is a Layer 3 routing protocol used for IP routing within an
Autonomous System. It operates at the network layer and is not related to Layer 7 routing methods.
C . BGP (Border Gateway Protocol): Another Layer 3 routing protocol, BGP is used for routing
between Autonomous Systems on the internet. It does not pertain to Layer 7 or application-layer
routing.
D . HTTP content routing: This aligns with FortiWeb's capabilities to make routing decisions based on
the content of HTTP requests, such as URL paths, headers, or other application-layer data. This is a
Layer 7 routing method supported by FortiWeb.
Therefore, the correct answer is D. HTTP content routing.
Reference:
FortiWeb 7.2.6 Administration Guide: "FortiWeb provides advanced Layer 7 load balancing and
authentication offload services."
cloud.orange-business.com
FortiWeb Data Sheet: "FortiWeb provides advanced Layer 7 load balancing and authentication offload
services."
Exclusive Networks
FortiWeb on OCB-FE - Installation and Deployment Guide: "FortiWeb provides advanced Layer 7 load
balancing and authentication offload services."
cloud.orange-business.com
These references confirm that FortiWeb supports HTTP content routing as a Layer 7 routing method.
Comments
Question 9
Which command will enable debugging for the FortiWeb user tracking feature?
- A. debug enable user-tracking 7
- B. diagnose debug application user-cracking 7
- C. debug application user-cracking 7
- D. diagnose debug enable user-cracking 7
Answer:
B
Explanation:
To enable debugging for the user tracking feature in FortiWeb, you would use the command diagnose
debug application user-tracking 7. This command enables debugging for the user-tracking
application and sets the debug level to 7, providing detailed logs for troubleshooting.
Comments
Question 10
Refer to the exhibit.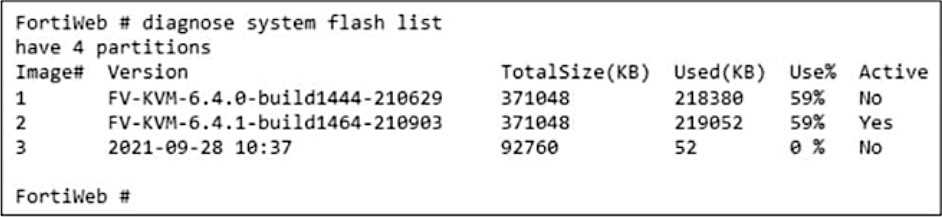
What is true about this FortiWeb device? (Choose two.)
- A. It has 41% of the disk available for logging.
- B. It was upgraded to a different version after initial installation.
- C. It is currently running version 6.4.0.
- D. It is currently running version 6.4.1.
Answer:
B
Explanation:
It was upgraded to a different version after initial installation: The device has multiple partitions with
different firmware versions (6.4.0 and 6.4.1), indicating that it was upgraded after the initial
installation from version 6.4.0 to 6.4.1.
Comments
Page 1 out of 3
Viewing questions 1-10 out of 36
page 2