Question 1
Exhibit.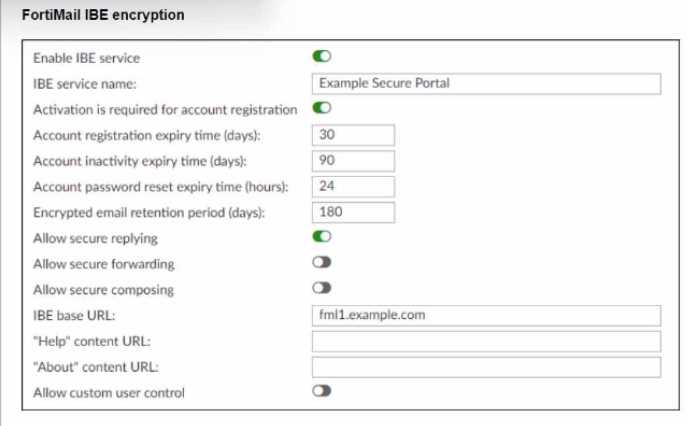
Reter to the exhibit, which shows the IBE Encryption page of a FortiMail device. Which user account
behavior can you expect from these IBE settings?
- A. After initial registration. IBE users can access the secure portal without authenticating again for 90 days.
- B. Registered IBE users have 90 days from the time they receive a notification email message to access their IBE email.
- C. IBE user accounts will expire after 90 days of inactivity and must register again to access new IBE email message.
- D. First time IBE users must register to access their email within 90 days of receiving the notification email message
Answer:
C
Comments
Question 2
A FortiMail is configured with the protected domain example.com.
On this FortiMail, which two envelope addresses are considered incoming? (Choose two.)
- A. EMAIL FROM: nisGhosted.r.et RCPT 70: noceexampIe.com
- B. MAIL FROM: supporteexample.com RCPT TO: [email protected]
- C. MAIL FROM: accountsGexample.ccm RCPT TO: [email protected]
- D. MAIL FROM: training&external.crg RCPT TO: student30extersal.org
Answer:
B, C
Comments
Question 3
Refer to the exhibit, which shows a few lines of FortiMail logs.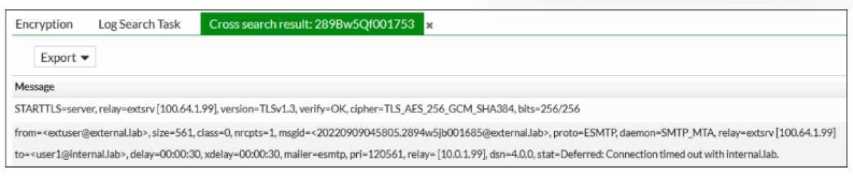
Based on these log entries, which two statements describe the operational status of this FortiMail
device? (Choose two.)
- A. FortiMail is experiencing issues accepting the connection from the external. lab MTA.
- B. FortiMail is experiencing issues delivering the email to the internal. lab MTA.
- C. The FortiMail device is in server mode.
- D. The FortiMail device is in gateway or transparent mode.
Answer:
B, D
Comments
Question 4
Refer to the exhibit, which shows the output of an email transmission using a telnet session.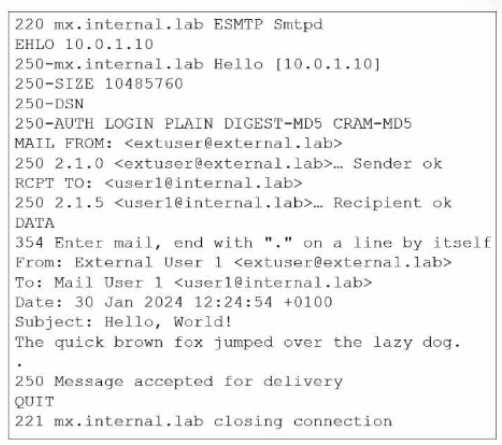
What are two correct observations about this SMTP session? (Choose two.)
- A. The SMTP envelope addresses are different from the message header addresses.
- B. The "Subject" is part of the message header.
- C. The"220 mx. internal, lab ESMTP Smtpd" message is part of the SMTP banner.
- D. The "250 Message accepted for delivery" message is part of the message body.
Answer:
B, C
Comments
Question 5
Which license must you apply to a FortiMail device to enable the HA centralized monitoring
features?
- A. Cloud gateway license
- B. Advanced Management and MSSP license
- C. Office 365 protection license
- D. Enterprise license
Answer:
B
Comments
Question 6
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to their
protected domain. After searching the logs, the administrator identities that the DSNs were not
generated because of any outbound email sent from their organization.
Which FortiMail antispam technique can the administrator enable to prevent this scenario?
- A. Spoofed header detection
- B. Spam outbreak protection.
- C. FortiGuard IP Reputation
- D. Bounce address tag validation
Answer:
D
Comments
Question 7
Refer to the exhibit, which displays the Mail Settings page of a FortiMail device running in gateway
mode.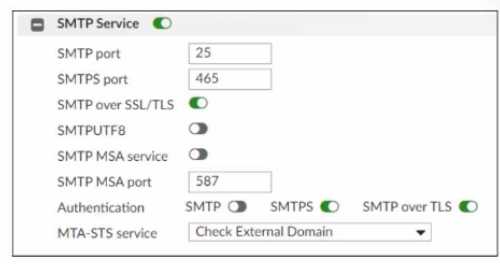
In addition to selecting Check External Domain in the MTA-STS service field, what else must an
administrator do to enable MTA-STS?
- A. Enable MTA-STS in the associated TLS profile.
- B. Enable SMTPUTF8 support in the mail server settings.
- C. Enable secure authentication in the associated SMTP authentication profile.
- D. Enable MTA-STS action in the appropriate inbound recipient policy.
Answer:
C
Comments
Question 8
Which two factors are required for an active-active HA configuration of FortiMail in server mode?
(Choose two.)
- A. Devices must be deployed behind a load balancer.
- B. Service monitoring must be configured for remote SMTP
- C. A primary must be designated to initially process email.
- D. Mail data must be stored on a NAS server.
Answer:
AD
Comments
Question 9
Refer to the exhibit, which displays an access control rule.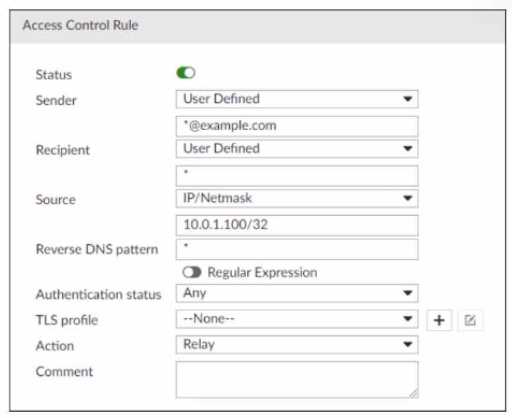
What are two expected behaviors for this access control rule? (Choose two.)
- A. Email must originate from an example. com email address.
- B. Senders must be authenticated to match this rule.
- C. Email matching this rule will be relayed.
- D. Emails must be sent from the 10.0.1.0/24 subnet.
Answer:
A, B
Comments
Question 10
Reter to the exhibits.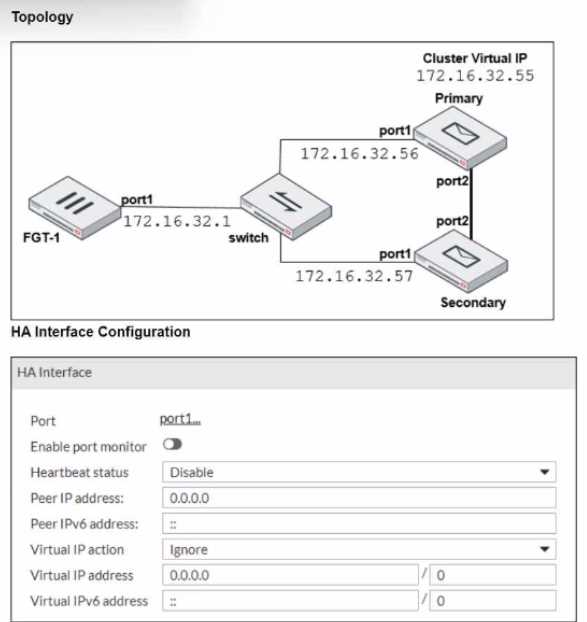
The exhibits display a topology diagram of a FortiMail cluster (Topology) and the primary HA
interface configuration of the Primary FortiMail (HA Interface Configuration)
Which three actions are recommended when configuring the primary FortiMail HA interface?
(Choose three.)
- A. In the Heartbeat status drop-down list, select Primary
- B. In the Virtual IP action drop-down list, select Use
- C. In the Virtual IP address field, type 172.16.32.55/24
- D. In the Peer IP address field, type 172.16.32.57
- E. Disable Enable port monitor
Answer:
B, C, D
Comments
Page 1 out of 5
Viewing questions 1-10 out of 53
page 2