Question 1
Refer to the exhibit, which shows a partial configuration from the remote authentication server.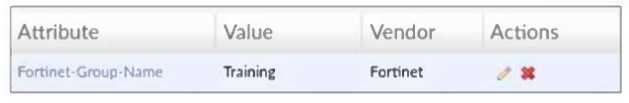
Why does the FortiGate administrator need this configuration?
- A. To set up a RADIUS server Secret.
- B. To authenticate Any FortiGate user groups.
- C. To authenticate and match the Training OU on the RADIUS server.
- D. To authenticate only the Training user group.
Answer:
D
Explanation:
The Fortinet-Group-Name attribute is used to restrict authentication to users who belong specifically
to the "Training" user group on the RADIUS server.
Comments
Question 2
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.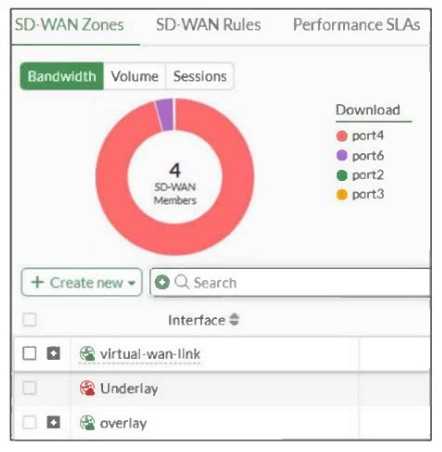
Based on the exhibit, which statement is true?
- A. The Underlay zone is the zone by default.
- B. The Underlay zone contains no member.
- C. port2 and port3 are not assigned to a zone.
- D. The virtual-wan-link and overlay zones can be deleted.
Answer:
A
Explanation:
The Underlay zone is the default SD-WAN zone, typically representing the physical interfaces in the
SD-WAN configuration before overlay or virtual links are added.
Comments
Question 3
Which three statements explain a flow-based antivirus profile? (Choose three.)
- A. FortiGate buffers the whole file but transmits to the client at the same time.
- B. Flow-based inspection uses a hybrid of the scanning modes available in proxy-based inspection.
- C. If a virus is detected, the last packet is delivered to the client.
- D. Flow-based inspection optimizes performance compared to proxy-based inspection.
- E. The IPS engine handles the process as a standalone.
Answer:
A, B, D
Explanation:
Flow-based antivirus buffers the entire file while simultaneously transmitting data to the client to
minimize latency.
Flow-based inspection combines multiple scanning techniques from proxy-based modes for efficient
detection.
Flow-based inspection provides better performance by processing traffic on the fly without full proxy
overhead.
Comments
Question 4
Refer to the exhibit.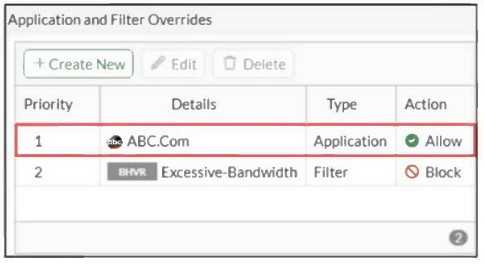
An administrator has configured an Application Overrides for the ABC.Com application signature and
set the Action to Allow. This application control profile is then applied to a firewall policy that is
scanning all outbound traffic. Logging is enabled in the firewall policy. To test the configuration, the
administrator accessed the ABC.Com web site several times.
Why are there no logs generated under security logs for ABC.Com?
- A. The ABC.Com Type is set as Application instead of Filter.
- B. The ABC.Com is configured under application profile, which must be configured as a web filter profile.
- C. The ABC.Com Action is set to Allow.
- D. The ABC.Com is hitting the category Excessive-Bandwidth.
Answer:
C
Explanation:
When the action is set to Allow in an application override, traffic matching this override is allowed
without generating security logs because it bypasses deeper inspection and blocking.
Comments
Question 5
Which two statements describe characteristics of automation stitches? (Choose two.)
- A. Actions involve only devices included in the Security Fabric.
- B. An automation stitch can have multiple triggers.
- C. Multiple actions can run in parallel.
- D. Triggers can involve external connectors.
Answer:
C, D
Explanation:
Automation stitches can execute multiple actions concurrently (in parallel).
Triggers for automation stitches can come from external connectors beyond just Fortinet devices.
Comments
Question 6
Which three statements about SD-WAN performance SLAs are true? (Choose three.)
- A. They rely on session loss and jitter.
- B. They can be measured actively or passively.
- C. They are applied in a SD-WAN rule lowest cost strategy.
- D. They monitor the state of the FortiGate device.
- E. All the SLAtargets can be configured.
Answer:
A, B, E
Explanation:
SD-WAN SLAs monitor metrics like packet loss and jitter to evaluate link performance.
SLA measurements can be performed using active probing or passive monitoring.
Administrators can configure all SLA target parameters to define performance criteria.
Comments
Question 7
Which two statements are true about an HA cluster? (Choose two.)
- A. An HA cluster cannot have both in-band and out-of-band management interfaces at the same time.
- B. Link failover triggers a failover if the administrator sets the interface down on the primary device.
- C. When sniffing the heartbeat interface, the administrator must see the IP address 169.254.0.2.
- D. HA incremental synchronization includes FIB entries and IPsec SAs.
Answer:
B, D
Explanation:
Setting an interface down on the primary device triggers a failover due to link failover detection.
HA incremental synchronization includes forwarding information base (FIB) entries and IPsec security
associations (SAs) to maintain session continuity.
Comments
Question 8
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy.
When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file.
When downloading the same file through HTTPS, FortiGate does not detect the virus and does not
block the file, allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)
- A. The selected SSL inspection profile has certificate inspection enabled.
- B. The website is exempted from SSL inspection.
- C. The El CAR test file exceeds the protocol options oversize limit.
- D. The browser does not trust the FortiGate self-signed CA certificate.
Answer:
B, D
Comments
Question 9
You have configured the below commands on a FortiGate.
What would be the impact of this configuration on FortiGate?
- A. FortiGate will enable strict RPF on ail its interfaces and port1 will be enable for asymmetric routing.
- B. FortiGate will enable strict RPF on all its interfaces and port1 will be exempted from RPF checks.
- C. Port1 will be enabled with flexible RPF, and all other interfaces will be enabled for strict RPF
- D. The global configuration will take precedence and FortiGate will enable strict RPF on all interfaces.
Answer:
B
Explanation:
The global setting enables strict source checking (RPF) on all interfaces by default. The per-interface
setting disables the source check on port1, exempting it from strict RPF enforcement.
Comments
Question 10
Refer to the exhibit.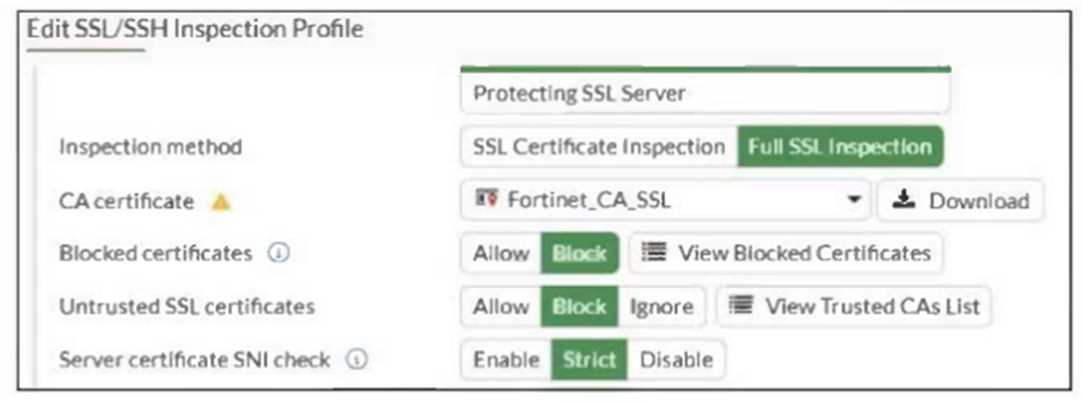
What would be the impact of these settings on the Server certificate SNI check configuration on
FortiGate?
- A. FortiGate will accept and use the CN in the server certificate for URL filtering if the SNI does not match the CN or SAN fields.
- B. FortiGate will accept the connection with a warning if the SNI does not match the CN or SAN fields.
- C. FortiGate will close the connection if the SNI does not match the CN or SAN fields.
- D. FortiGate will close the connection if the SNI does not match the CN and SAN fields
Answer:
D
Explanation:
With the Server certificate SNI check set to Strict, FortiGate enforces that the SNI must match either
the Common Name (CN) or Subject Alternative Name (SAN) in the server certificate; otherwise, it
closes the connection.
Comments
Page 1 out of 4
Viewing questions 1-10 out of 50
page 2