Question 1
What does FortiClient do as a fabric agent? (Choose two.)
- A. Provides IOC verdicts
- B. Creates dynamic policies
- C. Provides application inventory
- D. Automates Responses
Answer:
CD
Comments
Question 2
Exhibit.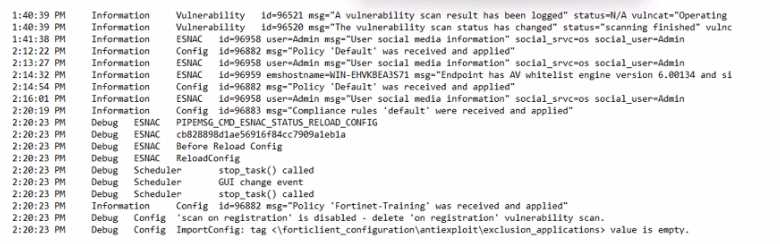
Based on the FortiClient logs shown in the exhibit, which endpoint profile policy is currently applied
lo the ForliClient endpoint from the EMS server?
- A. Fortinet-Training
- B. Default configuration policy c
- C. Compliance rules default
- D. Default
Answer:
A
Explanation:
Observation of Logs:
The logs show a policy named "Fortinet-Training" being applied to the endpoint.
Evaluating Policies:
The log entries indicate that the "Fortinet-Training" policy was received and applied.
Conclusion:
Based on the logs, the currently applied policy on the FortiClient endpoint is "Fortinet-Training".
Reference:
FortiClient EMS policy configuration and log analysis documentation from the study guides.
Comments
Question 3
Refer to the exhibit.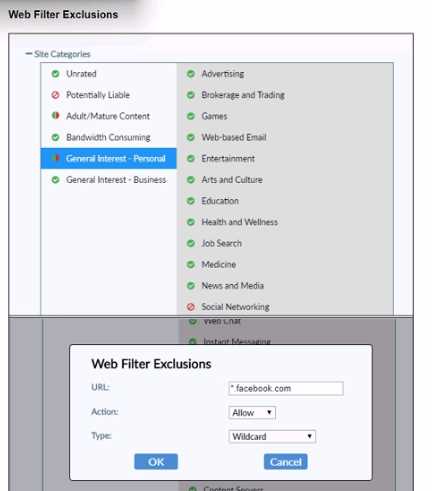
Based on the settings shown in the exhibit, which action will FortiClient take when users try to access
www facebook com?
- A. FortiClient will allow access to Facebook.
- B. FortiClient will block access to Facebook and its subdomains.
- C. FortiClient will monitor only the user's web access to the Facebook website
- D. FortiClient will prompt a warning message to want the user before they can access the Facebook website
Answer:
B
Explanation:
Observation of Web Filter Exclusions:
The exhibit shows a web filter exclusion for "*.facebook.com" with the action set to "Allow."
Evaluating Actions:
This configuration means that FortiClient will allow access to Facebook and its subdomains.
Conclusion:
When users try to access "
www.facebook.com
," FortiClient will allow the access based on the web
filter exclusion settings.
Reference:
FortiClient web filter configuration and exclusion documentation from the study guides.
Comments
Question 4
Why does FortiGate need the root CA certificate of FortiCient EMS?
- A. To revoke FortiClient client certificates
- B. To sign FortiClient CSR requests
- C. To update FortiClient client certificates
- D. To trust certificates issued by FortiClient EMS
Answer:
A
Explanation:
Understanding the Need for Root CA Certificate:
The root CA certificate of FortiClient EMS is necessary for FortiGate to trust certificates issued by
FortiClient EMS.
Evaluating Use Cases:
FortiGate needs the root CA certificate to establish trust and validate certificates issued by FortiClient
EMS.
Conclusion:
The primary reason FortiGate needs the root CA certificate of FortiClient EMS is to trust certificates
issued by FortiClient EMS.
Reference:
FortiClient EMS and FortiGate certificate management documentation from the study guides.
Comments
Question 5
Which three features does FortiClient endpoint security include? (Choose three.)
- A. DLP
- B. Vulnerability management
- C. L2TP
- D. lPsec
- E. Real-lime protection
Answer:
BDE
Explanation:
Understanding FortiClient Features:
FortiClient endpoint security includes several features aimed at protecting and managing endpoints.
Evaluating Feature Set:
Vulnerability management is a key feature of FortiClient, helping to identify and address
vulnerabilities (B).
IPsec is supported for secure VPN connections (D).
Real-time protection is crucial for detecting and preventing threats in real-time (E).
Eliminating Incorrect Options:
Data Loss Prevention (DLP) (A) is typically managed by FortiGate or FortiMail.
L2TP (C) is a protocol used for VPNs but is not specifically a feature of FortiClient endpoint security.
Reference:
FortiClient endpoint security features documentation from the study guides.
Comments
Question 6
Which component or device defines ZTNA lag information in the Security Fabric integration?
- A. FortiClient
- B. FortiGate
- C. FortiClient EMS
- D. FortiGate Access Proxy
Answer:
C
Explanation:
Understanding ZTNA:
Zero Trust Network Access (ZTNA) requires defining tags for identifying and managing endpoint
access.
Evaluating Components:
FortiClient EMS is responsible for managing and defining ZTNA tag information within the Security
Fabric.
Conclusion:
The correct component that defines ZTNA tag information in the Security Fabric integration is
FortiClient EMS.
Reference:
ZTNA and FortiClient EMS configuration documentation from the study guides.
Comments
Question 7
Which security fabric component sends a notification io quarantine an endpoint after IOC detection
"n the automation process?
- A. FortiAnalyzer
- B. FortiGate
- C. FortiClient EMS
- D. FortiClient
Answer:
C
Explanation:
Understanding the Automation Process:
In the Security Fabric, automation processes can include actions such as quarantining an endpoint
after an IOC (Indicator of Compromise) detection.
Evaluating Responsibilities:
FortiClient EMS plays a crucial role in endpoint management and can send notifications to
quarantine endpoints.
Conclusion:
The correct security fabric component that sends a notification to quarantine an endpoint after IOC
detection is FortiClient EMS.
Reference:
FortiClient EMS and automation process documentation from the study guides.
Comments
Question 8
An administrator configures ZTNA configuration on the FortiGate. Which statement is true about the
firewall policy?
- A. It redirects the client request to the access proxy.
- B. It uses the access proxy.
- C. It defines ZTNA server.
- D. It only uses ZTNA tags to control access for endpoints.
Answer:
A
Explanation:
"The firewall policy matches and redirects client requests to the access proxy VIP"
https://docs.fortinet.com/document/fortigate/7.0.0/new-features/194961/basic-ztna-configuration
Comments
Question 9
Refer to the exhibit.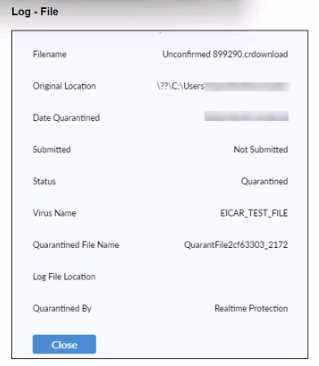
Based on the FortiClient tog details shown in the exhibit, which two statements ace true? (Choose
two.)
- A. The filename Is Unconfirmed 899290.crdovnload.
- B. The file status is Quarantined
- C. The filename is sent to FortiSandbox for further inspection.
- D. The file location is \??\D:\Users\.
Answer:
AB
Comments
Question 10
Which two are benefits of using multi-tenancy mode on FortiClient EMS? (Choose two.)
- A. Separate host servers manage each site.
- B. Licenses are shared among sites
- C. The fabric connector must use an IP address to connect to FortiClient EMS.
- D. It provides granular access and segmentation.
Answer:
C, D
Explanation:
Understanding Multi-Tenancy Mode:
Multi-tenancy mode allows multiple independent sites or tenants to be managed from a single
FortiClient EMS instance.
Evaluating Benefits:
Licenses can be shared among sites, making it cost-effective (B).
It provides granular access and segmentation, allowing for detailed control and separation between
tenants (D).
Eliminating Incorrect Options:
Separate host servers managing each site (A) is not a feature of multi-tenancy mode.
The fabric connector's use of an IP address (C) is unrelated to multi-tenancy benefits.
Reference:
FortiClient EMS multi-tenancy configuration and benefits documentation from the study guides.
Comments
Page 1 out of 5
Viewing questions 1-10 out of 55
page 2