Question 1
Which of the following pen testing reports provides detailed information about all the tasks
performed during penetration testing?
- A. Client-Side Test Report
- B. Activity Report
- C. Host Report
- D. Vulnerability Report
Answer:
A
Comments
Question 2
The IP protocol was designed for use on a wide variety of transmission links. Although the maximum
length of an IP datagram is 64K, most transmission links enforce a smaller maximum packet length
limit, called a MTU.
The value of the MTU depends on the type of the transmission link. The design of IP accommodates
MTU differences by allowing routers to fragment IP datagrams as necessary. The receiving station is
responsible for reassembling the fragments back into the original full size IP datagram.
IP fragmentation involves breaking a datagram into a number of pieces that can be reassembled
later. The IP source, destination, identification, total length, and fragment offset fields in the IP
header, are used for IP fragmentation and reassembly.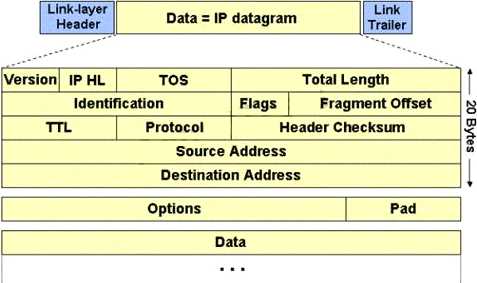
The fragment offset is 13 bits and indicates where a fragment belongs in the original IP datagram.
This value is a:
- A. Multiple of four bytes
- B. Multiple of two bytes
- C. Multiple of eight bytes
- D. Multiple of six bytes
Answer:
C
Comments
Question 3
The Web parameter tampering attack is based on the manipulation of parameters exchanged
between client and server in order to modify application data, such as user credentials and
permissions, price and quantity of products, etc.
Usually, this information is stored in cookies, hidden form fields, or URL Query Strings, and is used to
increase application functionality and control. This attack takes advantage of the fact that many
programmers rely on hidden or fixed fields (such as a hidden tag in a form or a parameter in a URL) as
the only security measure for certain operations.
Attackers can easily modify these parameters to bypass the security mechanisms that rely on them.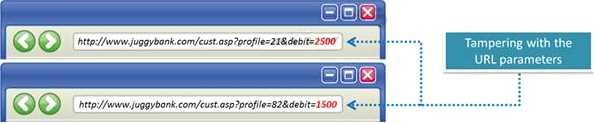
What is the best way to protect web applications from parameter tampering attacks?
- A. Validating some parameters of the web application
- B. Minimizing the allowable length of parameters
- C. Using an easily guessable hashing algorithm
- D. Applying effective input field filtering parameters
Answer:
D
Comments
Question 4
Which one of the following scans starts, but does not complete the TCP handshake sequence for
each port selected, and it works well for direct scanning and often works well through firewalls?
- A. SYN Scan
- B. Connect() scan
- C. XMAS Scan
- D. Null Scan
Answer:
A
Comments
Question 5
The first and foremost step for a penetration test is information gathering. The main objective of this
test is to gather information about the target system which can be used in a malicious manner to
gain access to the target systems.
Which of the following information gathering terminologies refers to gathering information through
social engineering on-site visits, face-to-face interviews, and direct questionnaires?
- A. Active Information Gathering
- B. Pseudonymous Information Gathering
- C. Anonymous Information Gathering
- D. Open Source or Passive Information Gathering
Answer:
A
Comments
Question 6
You are running known exploits against your network to test for possible vulnerabilities. To test the
strength of your virus software, you load a test network to mimic your production network. Your
software successfully blocks some simple macro and encrypted viruses.
You decide to really test the software by using virus code where the code rewrites itself entirely and
the signatures change from child to child, but the functionality stays the same. What type of virus is
this that you are testing?
- A. Metamorphic
- B. Oligomorhic
- C. Polymorphic
- D. Transmorphic
Answer:
A
Comments
Question 7
Which of the following statements is true about Multi-Layer Intrusion Detection Systems (mIDSs)?
- A. Decreases consumed employee time and increases system uptime
- B. Increases detection and reaction time
- C. Increases response time
- D. Both Decreases consumed employee time and increases system uptime and Increases response time
Answer:
A
Comments
Question 8
Paulette works for an IT security consulting company that is currently performing an audit for the
firm ACE Unlimited. Paulette's duties include logging on to all the company's network equipment to
ensure IOS versions are up-to-date and all the other security settings are as stringent as possible.
Paulette presents the following screenshot to her boss so he can inform the clients about necessary
changes need to be made. From the screenshot, what changes should the client company make?
Exhibit: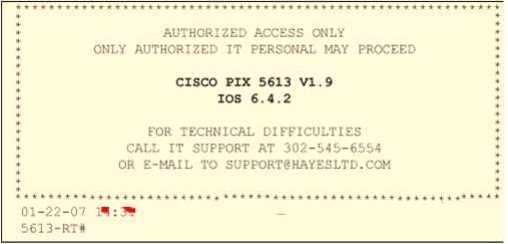
- A. The banner should not state "only authorized IT personnel may proceed"
- B. Remove any identifying numbers, names, or version information
- C. The banner should include the Cisco tech support contact information as well
- D. The banner should have more detail on the version numbers for the network equipment
Answer:
B
Comments
Question 9
Which of the following statements is true about the LM hash?
- A. Disabled in Windows Vista and 7 OSs
- B. Separated into two 8-character strings
- C. Letters are converted to the lowercase
- D. Padded with NULL to 16 characters
Answer:
A
Comments
Question 10
Which of the following is NOT related to the Internal Security Assessment penetration testing
strategy?
- A. Testing to provide a more complete view of site security
- B. Testing focused on the servers, infrastructure, and the underlying software, including the target
- C. Testing including tiers and DMZs within the environment, the corporate network, or partner company connections
- D. Testing performed from a number of network access points representing each logical and physical segment
Answer:
B
Comments
Page 1 out of 20
Viewing questions 1-10 out of 204
page 2