Question 1
Where will you find the reputation IP database, if you want to monitor traffic from known bad IP
reputation using OSSIM SIEM?
- A. /etc/ossim/reputation
- B. /etc/ossim/siem/server/reputation/data
- C. /etc/siem/ossim/server/reputation.data
- D. /etc/ossim/server/reputation.data
Answer:
D
Explanation: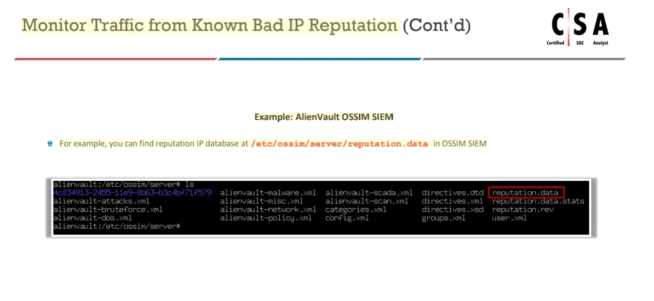
Comments
Question 2
According to the Risk Matrix table, what will be the risk level when the probability of an attack is very
low and the impact of that attack is major?
- A. High
- B. Extreme
- C. Low
- D. Medium
Answer:
D
Explanation: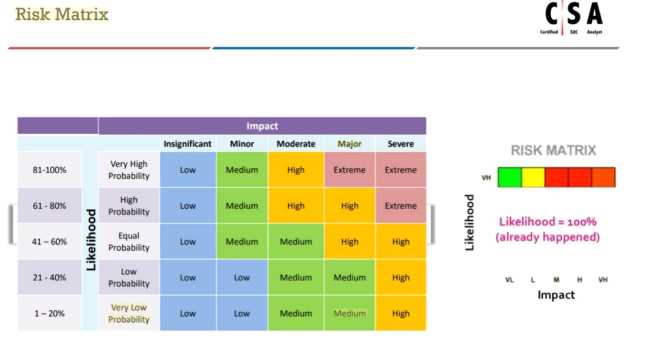
Comments
Question 3
Which of the following command is used to view iptables logs on Ubuntu and Debian distributions?
- A. $ tailf /var/log/sys/kern.log
- B. $ tailf /var/log/kern.log
- C. # tailf /var/log/messages
- D. # tailf /var/log/sys/messages
Answer:
B
Explanation:
Reference:
https://tecadmin.net/enable-logging-in-iptables-on-linux/
Comments
Question 4
Which of the following technique involves scanning the headers of IP packets leaving a network to
make sure
that the unauthorized or malicious traffic never leaves the internal network?
- A. Egress Filtering
- B. Throttling
- C. Rate Limiting
- D. Ingress Filtering
Answer:
A
Explanation:
Reference:
https://grokdesigns.com/wp-content/uploads/2018/04/CEH-v9-Notes.pdf
(99)
Comments
Question 5
Which of the following formula is used to calculate the EPS of the organization?
- A. EPS = average number of correlated events / time in seconds
- B. EPS = number of normalized events / time in seconds
- C. EPS = number of security events / time in seconds
- D. EPS = number of correlated events / time in seconds
Answer:
C
Explanation: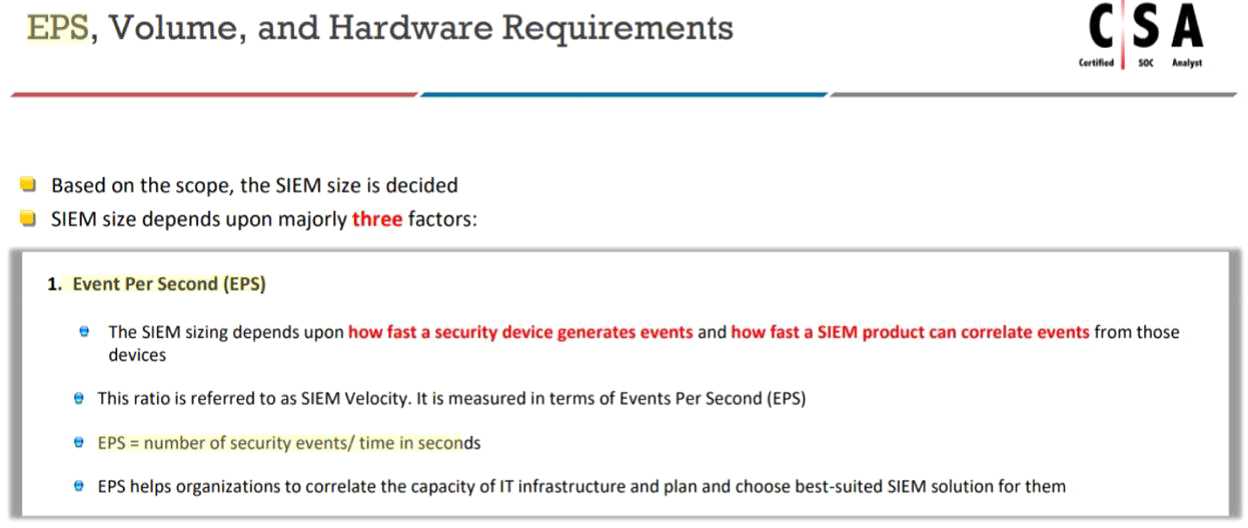
Comments
Question 6
Juliea a SOC analyst, while monitoring logs, noticed large TXT, NULL payloads.
What does this indicate?
- A. Concurrent VPN Connections Attempt
- B. DNS Exfiltration Attempt
- C. Covering Tracks Attempt
- D. DHCP Starvation Attempt
Answer:
B
Explanation:
Reference:
https://www.google.com/url
?
sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwj8gZaKq_PuAhWGi1wKHfQTC0oQFjAAegQI
ARAD
&url=https%3A%2F%2Fconf.splunk.com%2Fsession%2F2014%
2Fconf2014_FredWilmotSanfordOwings_Splunk_Security.pdf&usg=AOvVaw3ZLfzGqM-
VUG7xKtze67ac
Comments
Question 7
An organization is implementing and deploying the SIEM with following capabilities.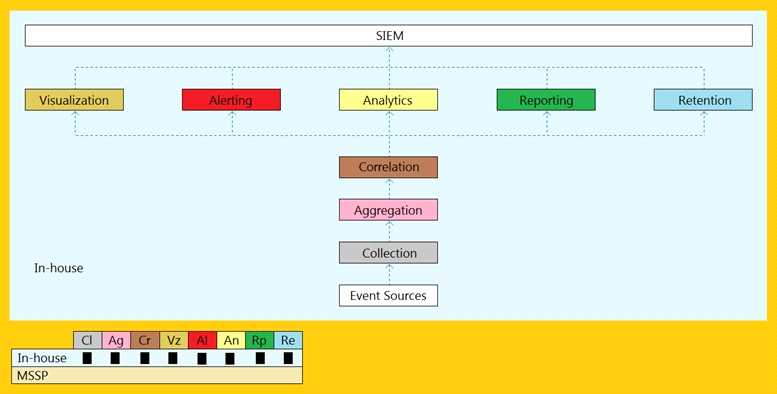
What kind of SIEM deployment architecture the organization is planning to implement?
- A. Cloud, MSSP Managed
- B. Self-hosted, Jointly Managed
- C. Self-hosted, Self-Managed
- D. Self-hosted, MSSP Managed
Answer:
C
Explanation: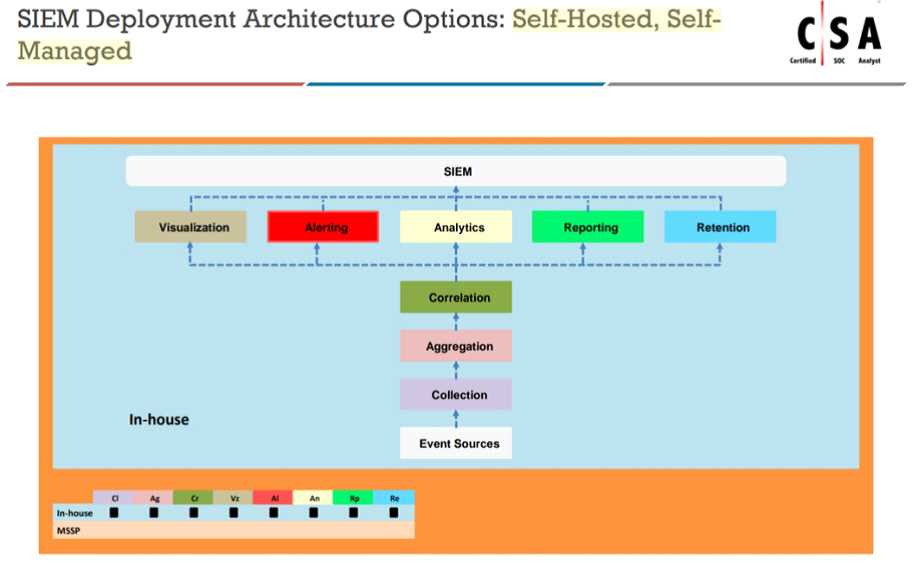
Comments
Question 8
What is the process of monitoring and capturing all data packets passing through a given network
using different tools?
- A. Network Scanning
- B. DNS Footprinting
- C. Network Sniffing
- D. Port Scanning
Answer:
C
Explanation:
Reference:
https://www.greycampus.com/opencampus/ethical-hacking/sniffing-and-its-types
Comments
Question 9
Which of the following is a report writing tool that will help incident handlers to generate efficient
reports on detected incidents during incident response process?
- A. threat_note
- B. MagicTree
- C. IntelMQ
- D. Malstrom
Answer:
C
Comments
Question 10
Which of the following Windows features is used to enable Security Auditing in Windows?
- A. Bitlocker
- B. Windows Firewall
- C. Local Group Policy Editor
- D. Windows Defender
Answer:
C
Explanation:
Reference:
https://resources.infosecinstitute.com/topic/how-to-audit-windows-10-application-logs/
Comments
Page 1 out of 9
Viewing questions 1-10 out of 100
page 2