Question 1
A company requires hard drives to be securely wiped before sending decommissioned systems to recycling. Which of the following best describes this policy?
- A. Enumeration
- B. Sanitization Most Votes
- C. Destruction
- D. Inventory
Answer:
B
Comments
Question 2
An IT manager is increasing the security capabilities of an organization after a data classification initiative determined that sensitive data could be exfiltrated from the environment. Which of the following solutions would mitigate the risk?
- A. XDR
- B. SPF
- C. DLP
- D. DMARC
Answer:
C
Comments
Question 3
An engineer needs to find a solution that creates an added layer of security by preventing unauthorized access to internal company resources. Which of the following would be the best solution?
- A. RDP server
- B. Jump server Most Votes
- C. Proxy server
- D. Hypervisor
Answer:
B
Comments
Question 4
A security analyst is reviewing the logs on an organizations DNS server and notices the following unusual snippet: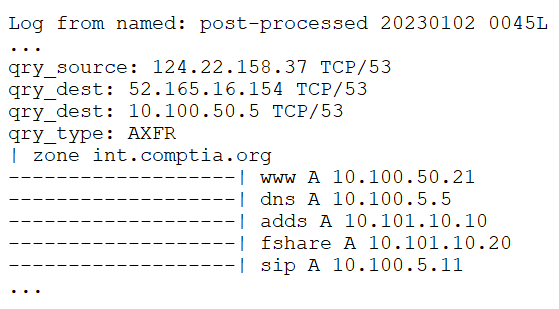
Which of the following attack techniques was most likely used?
- A. Determining the organization's ISP-assigned address space
- B. Bypassing the organization's DNS sinkholing
- C. Footprinting the internal network
- D. Attempting to achieve initial access to the DNS server
- E. Exfiltrating data from fshare.int.complia.org
Answer:
C
Comments
Question 5
Which of the following describes the maximum allowance of accepted risk?
- A. Risk indicator
- B. Risk level
- C. Risk score
- D. Risk threshold
Answer:
D
Comments
Question 6
Which of the following threat actors is the most likely to be motivated by profit?
- A. Hacktivist
- B. Insider threat
- C. Organized crime
- D. Shadow IT
Answer:
C
Comments
Question 7
Which of the following exercises should an organization use to improve its incident response process?
- A. Tabletop
- B. Replication
- C. Failover
- D. Recovery
Answer:
A
Comments
Question 8
A systems administrator would like to deploy a change to a production system. Which of the following must the administrator submit to demonstrate that the system can be restored to a working state in the event of a performance issue?
- A. Backout plan Most Votes
- B. Impact analysis
- C. Test procedure
- D. Approval procedure
Answer:
A
Comments
Question 9
A security engineer is installing an IPS to block signature-based attacks in the environment.
Which of the following modes will best accomplish this task?
- A. Monitor
- B. Sensor
- C. Audit
- D. Active
Answer:
D
Comments
Question 10
A city municipality lost its primary data center when a tornado hit the facility. Which of the following should the city staff use immediately after the disaster to handle essential public services?
- A. BCP
- B. Communication plan
- C. DRP
- D. IRP
Answer:
C
Comments
Page 1 out of 29
Viewing questions 1-10 out of 300
page 2