comptia sy0-601 practice test
CompTIA Security+ 2021
Last exam update: Jul 20 ,2024
Question 1
The lessons-learned analysis from a recent incident reveals that an administrative office worker received a call from someone claiming to be from technical support. The caller convinced the office worker to visit a website, and then download and install a program masquerading as an antivirus package. The program was actually a backdoor that an attacker could later use to remote control the worker's PC. Which of the following would be BEST to help prevent this type of attack in the future?
- A. Data loss prevention
- B. Segmentation
- C. Application whitelisting
- D. Quarantine
Answer:
c
Question 2
The process of passively gathering information prior to launching a cyberattack is called:
- A. tailgating.
- B. reconnaissance.
- C. pharming.
- D. prepending.
Answer:
b
Question 3
A security engineer obtained the following output from a threat intelligence source that recently performed an attack on the companys server: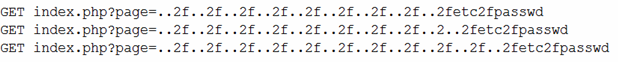
Which of the following BEST describes this kind of attack?
- A. Directory traversal
- B. SQL injection
- C. API
- D. Request forgery
Answer:
a
Question 4
Which of the following distributes data among nodes, making it more difficult to manipulate the data while also minimizing downtime?
- A. MSSP
- B. Public cloud
- C. Hybrid cloud
- D. Fog computing
Answer:
c
Question 5
Which of the following would be used to find the MOST common web-application vulnerabilities?
- A. OWASP
- B. MITRE ATT&CK
- C. Cyber Kill Chain
- D. SDLC
Answer:
a
Question 6
A financial institution would like to store its customer data in a cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would BEST meet the requirement?
- A. Asymmetric
- B. Symmetric
- C. Homomorphic
- D. Ephemeral
Answer:
c
Reference:
https://en.wikipedia.org/wiki/Homomorphic_encryption
Question 7
Which of the following is the correct order of volatility from MOST to LEAST volatile?
- A. Memory, temporary filesystems, routing tables, disk, network storage
- B. Cache, memory, temporary filesystems, disk, archival media
- C. Memory, disk, temporary filesystems, cache, archival media
- D. Cache, disk, temporary filesystems, network storage, archival media
Answer:
b
Question 8
A development team employs a practice of bringing all the code changes from multiple team members into the same development project through automation. A tool is utilized to validate the code and track source code through version control. Which of the following BEST describes this process?
- A. Continuous delivery
- B. Continuous integration
- C. Continuous validation
- D. Continuous monitoring
Answer:
b
Question 9
A technician is setting up a new firewall on a network segment to allow web traffic to the internet while hardening the network. After the firewall is configured, users receive errors stating the website could not be located. Which of the following would best correct the issue?
- A. Setting an explicit deny to all traffic using port 80 instead of 443
- B. Moving the implicit deny from the bottom of the rule set to the top
- C. Configuring the first line in the rule set to allow all traffic
- D. Ensuring that port 53 has been explicitly allowed in the rule set
Answer:
d
Question 10
A security architect is designing a remote access solution for a business partner. The business partner needs to access one Linux server at the company. The business partner wants to avoid managing a password for authentication and additional software installation. Which of the following should the architect recommend?
- A. Soft token
- B. Smart card
- C. CSR
- D. SSH key
Answer:
d